A glimpse to the phishing and malware situation in Mexico (April – June)
Abstract
As mentioned on the first statistics report of phishing and malware, it is important to show the most common cases to alert users and reduce the number of people affected.
During this trimester, some of the most interesting phishing campaigns were related to the Mexican Service Tax Administration (Servicio de Administración Tributaria, SAT) and with .cab files sent as attachments. There was also an increase in the amount of fake Banamex emails and the appearance of fake emails of Banorte, Netflix, WhatsApp and CFE (Federal Electricity Commission in Mexico), which were not observed during the first statistics report. Another notable characteristic is that phishing campaigns have opted to include two links, one for users and one for enterprises, and each redirects to different phishing sites. As for malware, the most common type is the malicious Word document.

Introduction
Thanks to the users that report the suspicious emails that get to their accounts, we have taken down several phishing sites, provoking the frustration of the criminals, who even attempt to block our IP addresses to stop us from accessing their fake websites.
However, this is not enough and we keep doing our best to take down these sites. Remember that you can send us the emails that you found suspicious to phishing at cert dot unam dot mx or malware at cert dot unam dot mx, we check every one of them to prevent other people from being affected by these frauds, since for every URL between 500 and 60 thousand people can fall, depending on the popularity of the campaign.
Have you ever wondered how many people click on the links of the fake emails? According to the statistics of the domain bilgor.ee, during April, 20 of the most visited URLs included the word “Bancomer” and the first place got 62561 clicks. Now, this is just one domain, there are thousands more being used to host fake sites.
Phishing
Following are some examples of the phishing and malware cases, sent through email, that were observed between April and June of this year.
· SAT
One of the most interesting cases seen during the April-June trimester was related to emails that supplanted the identity of the SAT, asking the user to register an email to receive notifications.

After clicking the link, the user is redirected to the official Hotmail site where the login credentials are requested. Once the user authenticates, a screen asking the user to allow an alleged application shows up. The application requests permissions to access the information of the profile and the contact list.
In this case, the name of the application was “Registro Promociones” but it could be any other. If you accidentally agreed to allow the application, you can revoke the permissions by giving click on your username and selecting the following options: Account Configuration > Security and Privacy > Applications and Services > Manage permissions.
· CFE and Telmex
The emails that supposedly came from Telmex or the Federal Electricity Commission were related to debts or account statements and the details, they say, can be consulted on the Word document attached that, when opened, downloads a malicious executable from a remote server.
· Netflix
Netflix’s phishing emails say the user has won a subscription to the service. After clicking the link, the user is redirected to the login website of Hotmail/Outlook, where it is asked to authorize the use of an application in a similar way as in the fake SAT emails. After accepting the application, the attackers get access to the user’s account.
· Visa
From Visa phishing emails were not received, rather the URLs were reported to the UNAM-CERT. These redirected to a form, with fields in English or Italian, which said it was “verified by Visa” and where the user is asked to submit personal data such as: name, surname, email, birth date, cell phone number, credit card number, etc.
The email that was supposedly sent by WhatsApp redirected to a fake website that sales pharmaceuticals.
· PayPal
PayPal’s phishing emails report an unusual behavior on the user’s account or related to the banking card and invite the user to log in. After clicking the link, users are redirected to a fake PayPal website that might even have an SSL certificate.
· “Your couple is cheating you” (in Spanish: Tu pareja te engaña)
These emails, where someone unknown claims to have proves that the user is being cheated on, contain a malicious Word document that downloads malware after they are opened. In this case, the type of malware downloaded was the ransomware CTB-Locker and, therefore, the files of the people who open the Word document are ciphered.
· Banamex
As mentioned at the beginning, during this trimester we observed a considerable increase in the amount of emails related to Banamex. During the past months it was not common to receive them, being Bancomer and Santander the most supplanted institutions. The subjects used to trick people are related to: blocked accounts for “security reasons”, updates of data once a month “due to the federal law of data protection” and information related to withdrawals or purchases. In some cases, the emails had malicious Word documents attached.

· Bancomer
For Bancomer, the subjects used are the following: reactivation of the secure access on the portal, renovation of the “advanced service”, activation of cell phone alerts, unblocking a card, renovation of the “secure access device” and verification of the cellphone number.

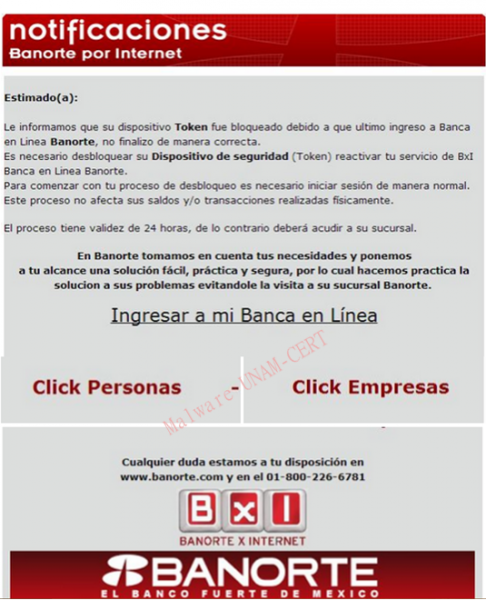
· Banorte
The number of phishing emails related to Banorte was very low; however, we considered it was important to include it. In this case, the emails mention that the token has been blocked and that it is necessary to log in.
· Scotiabank
The fake Scotiabank emails also mention the reform of the data protection law to make users write information about themselves and their banking cards in phishing websites. It is also common the use of threats, such as “your account will be suspended”, to pressure users.
· Santander
The users of this bank must be careful with the emails that ask them to verify their cellphone number, login to find out why their banking cards were allegedly limited or to unblock their account or the access to the online banking.

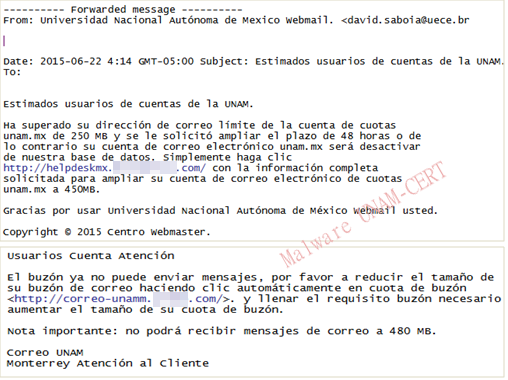
· Limit of email accounts
También se recibieron varios reportes de usuarios de la UNAM a los que les había llegado un correo diciendo que el buzón de su cuenta estaba saturado y que debían proporcionar ciertos datos para aumentar el tamaño del buzón.
Malware
· Cab
A cabinet file contains several files compressed as one and are commonly used to organize Microsoft Windows installation files that copy to a system.
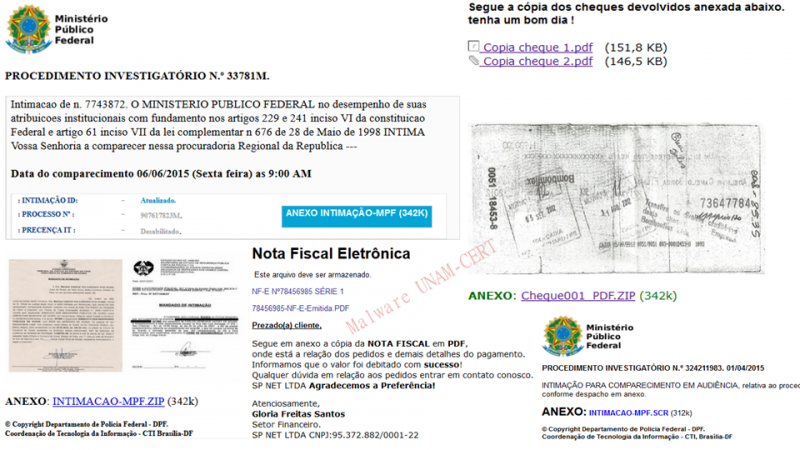
· CPL
During this trimester we also received several CPL files. The related emails are in Portuguese and contain images of fake bank checks, fiscal notes or federal investigation procedures to appear real and convince the user to download files from the links on the email. As mentioned in the report about a CPL sample, this kind of file is commonly used by banking Trojan developers who target Brazilian users. Remember that cpl files are dynamic link libraries that contain the functionality of the Control Panel icons, so they can be executed with double click.
Estadísticas
The statistics shown below are based on the emails sent to the malware analysis team at UNAM-CERT through [phishing at cert dot unam dot mx] and [malware at cert dot unam dot mx] between April 1st and June 23th of 2015. It does not represent the whole malware and phishing situation in Mexico; it is, as the title suggests, a “glimpse” of the phishing attacks observed in our country during the last three months. Spam related emails were not considered.
According to our analysis, the most common targets for phishing attacks were banking institutions that together represent 69%. Of these, 66% focused on banks in Mexico (Bancomer, Banamex, Santander, Scotiabank, IXE, Banorte and HSBC) y 3% were related to banks in Brazil (Banco do Brasil, Bradesco, Caixa and Itau).
Most of them included links to redirect the user to malicious websites, whether to steal data or to download malware. 16% contained attachments that the user was supposed to download to, for example, “check the bank statement” or the information related to a “withdrawal from the bank account”.
Out of this 16%, most of the attachments were Word documents (.doc). In second place, cabinet files (.cab). And, in lesser amount, PDF files. Contrary to what was presented on the past report, .zip files were not received, being replaced by .cab files.