Pharming and Phising in Brazilian sites
Some days ago we received a mail, which notified about a malicious code propagated using a URL as the following:
http://XXXXXXX#/fotos_flagrante-Dilma.JPEG?0.25970
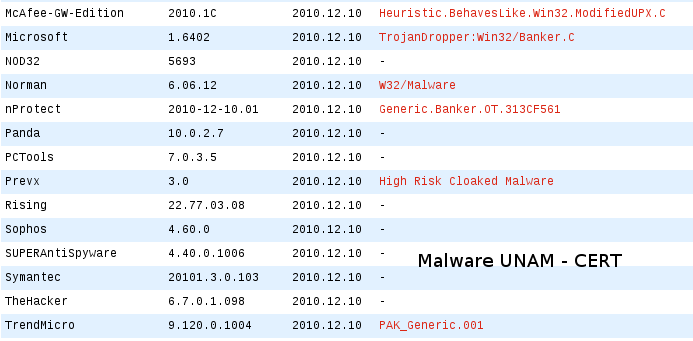
The file could be downloaded from the previous link, it is identified as fotos.com. So far, the antivirus engines that detect it as a threat, are the following:
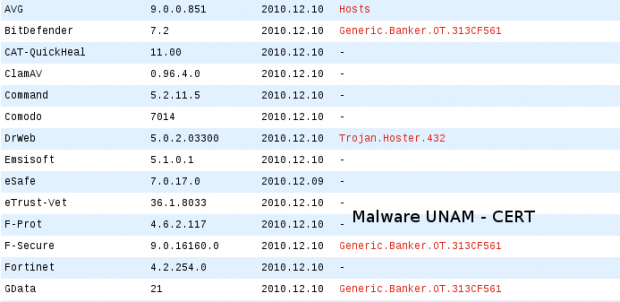
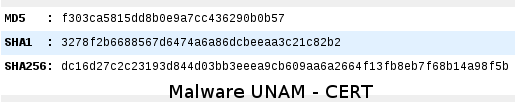
The digital information from the sample is shown as follows:
When executed, it starts Internet Explorer and Firefox, making a query to the site httpXXXXXX://boloob.com/ /new/total_visitas.php
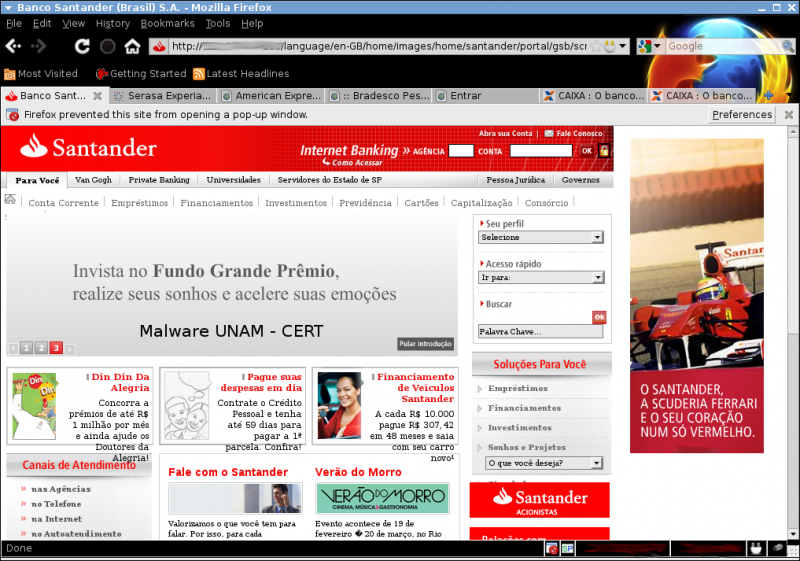
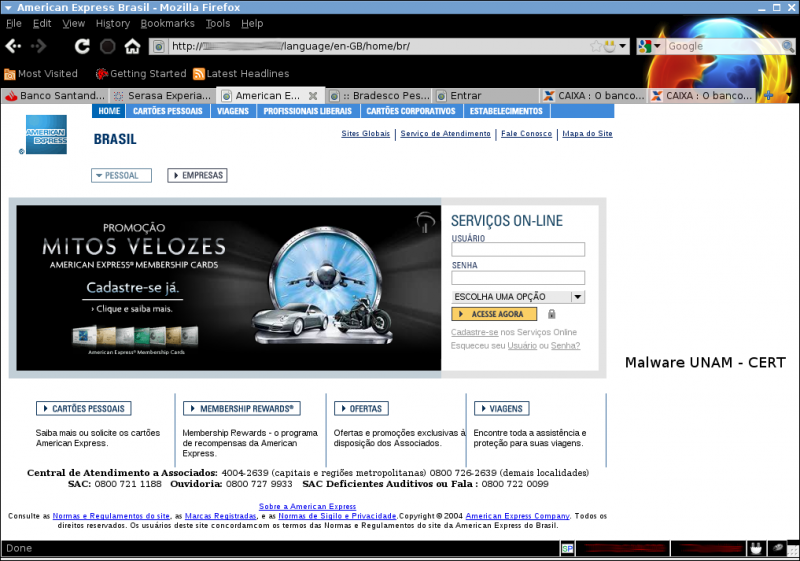
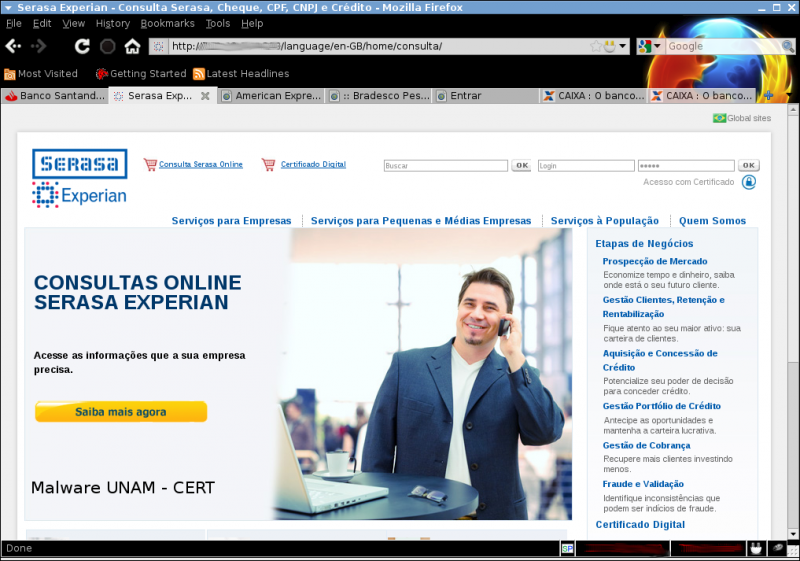
It performs the deleting of the hosts file in the computer and creates a new one making a pharming of the next sites:
173.XXX.XXX.203 serasa.com.br
173.XXX.XXX.203 www.serasa.com.br
173.XXX.XXX.203 bradescopj.com.br 173.XXX.XXX.203 itau.com.br 173.XXX.XXX.203 bradesconetempresa.com.br 173.XXX.XXX.203 www.bradesconetempresa.com.br 173.XXX.XXX.203 www.santander.com.br 173.XXX.XXX.203 www.banespa.com.br 173.XXX.XXX.203 www.santanderbanespa.com.br 173.XXX.XXX.203 santander.com.br 173.XXX.XXX.203 banespa.com.br 173.XXX.XXX.203 santanderbanespa.com.br 173.XXX.XXX.203 www.americanexpress.com.br 173.XXX.XXX.203 americanexpress.com.br 173.XXX.XXX.203 www.msn.com 173.XXX.XXX.203 msn.com 173.XXX.XXX.203 www.hotmail.com 173.XXX.XXX.203 hotmail.com 173.XXX.XXX.203 www.live.com 173.XXX.XXX.203 live.com 173.XXX.XXX.203 www.itau.com.br 173.XXX.XXX.203 www.itaupersonnalite.com.br 173.XXX.XXX.203 itaupersonnalite.com.br 173.XXX.XXX.203 www.banrisul.com.br 173.XXX.XXX.203 banrisul.com.br 173.XXX.XXX.203 www.bradesco.com.br 173.XXX.XXX.203 www.bradescoprime.com.br 173.XXX.XXX.203 www.prime.com.br 173.XXX.XXX.203 bradesco.com.br 173.XXX.XXX.203 bradescoprime.com.br 173.XXX.XXX.203 prime.com.br 173.XXX.XXX.203 www.bradescopessoajuridica.com.br 173.XXX.XXX.203 bradescopessoajuridica.com.br 173.XXX.XXX.203 www.bradescopj.com.br 173.XXX.XXX.203 www.bb.com.br 173.XXX.XXX.203 bb.com.br 173.XXX.XXX.203 www.bancodobrasil.com.br 173.XXX.XXX.203 bancodobrasil.com.br 173.XXX.XXX.203 www.caixa.com.br 173.XXX.XXX.203 www.caixa.gov.br 173.XXX.XXX.203 www.caixaeconomica.com.br 173.XXX.XXX.203 www.caixaeconomica.gov.br 173.XXX.XXX.203 www.caixaeconomicafederal.gov.br 173.XXX.XXX.203 www.cef.com.br 173.XXX.XXX.203 www.cef.gov.br 173.XXX.XXX.203 caixa.com.br 173.XXX.XXX.203 caixa.gov.br 173.XXX.XXX.203 caixaeconomica.com.br 173.XXX.XXX.203 caixaeconomica.gov.br 173.XXX.XXX.203 caixaeconomicafederal.com.br 173.XXX.XXX.203 caixaeconomicafederal.gov.br 173.XXX.XXX.203 cef.com.br 173.XXX.XXX.203 cef.gov.br At present, the phishing for the following sites remain active: santander.com.br http://173.XXX.XXX.203/language/en-GB/home/images/home/santander/portal/gsb/script/templates/GCMRequest.do.htm serasa.com.br http://173.XXX.XXX.203/language/en-GB/home/consulta/ americanexpress.com.br http://173.XXX.XXX.203/language/en-GB/home/br/ bradesco.com.br http://173.XXX.XXX.203/language/en-GB/home/bnet/ caixa http://173.XXX.XXX.203/language/en-GB/home/cef/ hotmail.com msn.com live.com http://173.XXX.XXX.203/logs/index.htm It can be observed in the site code that it stores account names and passwords, using a php file, in , later it redirects to the genuine hotmail site.http://187.X.X.225/sb/get.php y posteriormente realiza la redirección hacia el sitio oficial de hotmail. Phishing sites: