Bots spreading continues on messenger
It is no wonder, but this year started with a common problem in 2010: malicious code spreading through instant message, in this case, through Microsoft Windows Live Messenger.
.
This is the message:
=====================================================================
te han dad oee no te molesta si subo esta foto tuya a mi face?
http://<ciertodominio.com>/fotos/FOTO-12-01-2011.JPG
=====================================================================
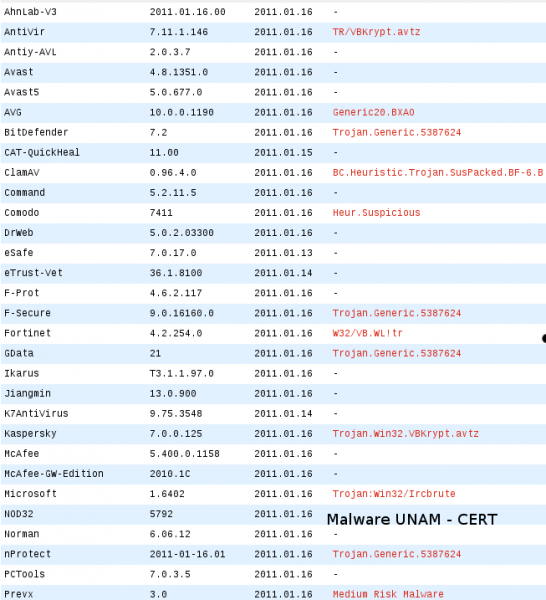
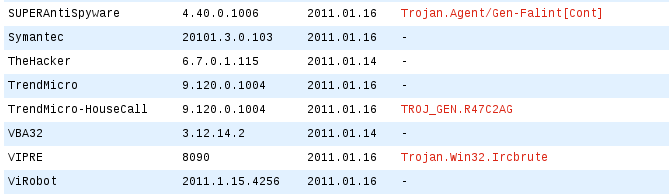
The JPG file, which actually is a Windows executable, was identified by the following antivirus engines:
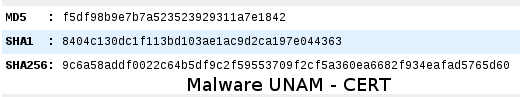
Its hashes are the following:
Executing the sample, it was copied to the folder C:\DOCUME~1\<suario>\CONFIG~1\Temp\, it created the process service, which added the registry key HKLM\Software\Microsoft\Windows\CurrentVersion\Run, with the registry value "Windows Services"="service.exe", to guarantee its next execution in the system and it opened the TCP port 3274, which was connected to the IRC server in the port 6667.
The IP address 212.X.X.241 belongs to the site server95527.santrex.net, hosted in Germany.
The IRC communication is shown as follows:
NICK {XP\MEX\569006}
USER X * 0 :X
MODE {XP\MEX\569006} -ix
JOIN ##spam##
PONG irc.priv8net.com
PONG irc.priv8net.com
PONG irc.priv8net.com