DroidKungFu and the exploits RageAgainstTheCage and Exploid for Android
Summary
The analyzed sample is a trojan that pretends to be an application to play Solitaire while doing other background activities without the user’s consent, such as exploiting vulnerabilities and installing additional applications or unwanted advertisements (adware). This trojan belongs to the DroidKungFu malware family, detected on 2011 and that started affecting applications in China. The DroidKungFu variants have two important characteristics: they use exploits to escalate privileges (known as RageAgainstTheCage and Exploid) and these are ciphered with AES. Its main actions are: collecting information about the device to send it to remote servers, exploiting vulnerabilities to root the device, install other applications and receive instructions of its C&C (although this functionality could not be researched because the domains were down).
Introduction
Android’s fast growth and popularity have caused a considerable increase in the malicious applications developed for this platform. Malware usually gets to a mobile device through an application that was downloaded and installed by the user or by another application. Most of DroidKungFu variants can be found on application markets or forums although, during the first years, attacks mainly focused on Chinese users. VirusTotal report can be checked here.
Static Analysis
Applications on Android are basically compressed files with “apk” extension, but with a specific structure. This can be verified using the file command on the sample, which in this case was called solitaire.apk.
All the applications must have a file called AndroidManifest.xml on their root directory. This file contains essential information about the application for the Android system: it describes the application’s components and lists the necessary permissions and libraries that the application needs, amongst other things.
When an Android application is compiled, the manifest file is converted to binary format.
AndroidManifest.xml
After decoding the manifest file to make it readable, the following permissions can be seen:
- · INTERNET: Internet access.
- · READ_PHONE_STATE: Allows to know the phone state.
- · ACCESS_NETWORK_STATE: To know the network state.
- · ACCESS_WIFI_STATE: To know the Wi-Fi state.
- · CHANGE_WIFI_STATE: To change the Wi-Fi state.
- · WRITE_EXTERNAL_STORAGE: To write in an external storage device, such as the SD card.
- · INSTALL_PACKAGES: To install applications.
- · ACCESS_COARSE_LOCATION: To access the device’s approximate location.
- · READ_SMS: Read SMS.
- · WRITE_SMS: Write SMS.
- · RECEIVE_BOOT_COMPLETED: Receive a notification when the device finishes booting.
- · READ_EXTERNAL_STORAGE: Read from an external storage device, such as the SD card.
- · ACCESS_FINE_LOCATION: Allows to know the device’s location.
- · ACCESS_LOCATION_EXTRA_COMMANDS: Access to additional location commands.
Almost at the end of the manifest file, on the “Activity” label, it is specified the first code section that will execute after the application is opened, which in this case is “.Solitaire”.
Unlike Windows applications, apk files can have multiple entry points that may be activated by the user’s actions or by system events. In this case, the application solitaire.apk is composed of four main activities:
- The card game .Solitaire
- com.google.update.Dialog
- cn.domob.android.ads.DomobActivity
- com.adwo.adsdk.AdwoAdBrowserActivity
It also contains a service, com.google.update.UpdateService, which executes in the background and contains the payload. And a receiver, com.google.update.Receiver, that checks whether the device has finished booting (BOOT_COMPLETED) to execute the previously mentioned service.
Defined as meta-data is the string ST_START_DELAY used by the application to specify the delay time in which the payload will execute, that is 1800 seconds or 30 minutes. And also the string ADMOGO_KEY with a value equal to b2609a99a69045269897d92cc685d4b3.
The next step is to convert the APK file to a JAR file and continue its analysis.
Strings in another language
During the analysis of the malicious application several strings that Google Translate identifies as simplified Chinese were found. Some examples are shown below, with their possible translation:
请授权: Authorized
确认: Confirm
打开USB调试 : USB debugging
本软件: Software
需要root权限才能使用全部功能: Requires root privileges to use the full functionality
Adware
Four packets were observed on the decompiled code: l, cn.domob.android, com and uk.co.lilhermit.android.core. Some of the classes with third party APIs found inside these packets were: com.adwo.adsdk, com.madhouse.android.ads y com.admogo.adapters.com. Madhouse, Domob and Adwo are advertisement enterprises for mobile devices that work mainly in China. According to HKCERT, both Admogo and Domob appear as malware families because they install a high risk plugin and steal information from the device to send it to a remote server. Admogo, in particular, has one class for several advertisements companies of different countries, as shown on the following image.
On the other hand, lilhermit appears to be a developer of non-malicious Android apps, so it is possible that the class called “Native” from uk.co.lilhermit.android.core was copied from the code of another application or from the GitHub repository of the author to be reused with malicious purposes.
Payload
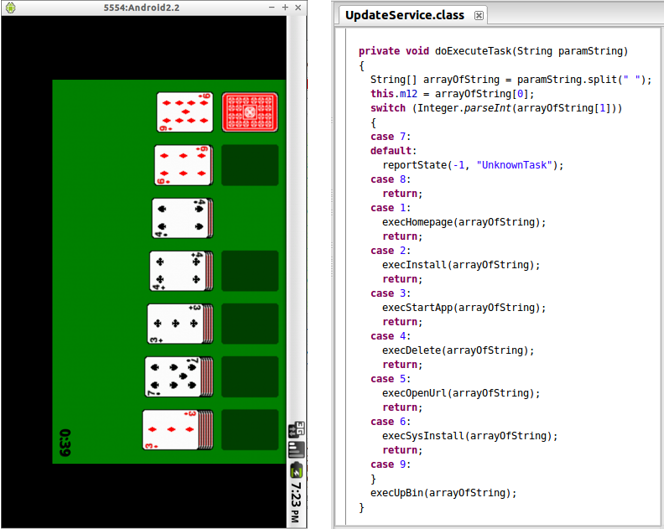
The payload is found in a class called com.google.UpdateService, to appear as an official Google update, legitimate and benign. This class contains the functions to generate POST requests with the device’s information, execute exploits and, if they succeed, execute the instructions sent by the C&C: execHomepage, execInstall, execStartApp, execDelete, execOpenURL, execSysInstall and execUpBin.
Exploits
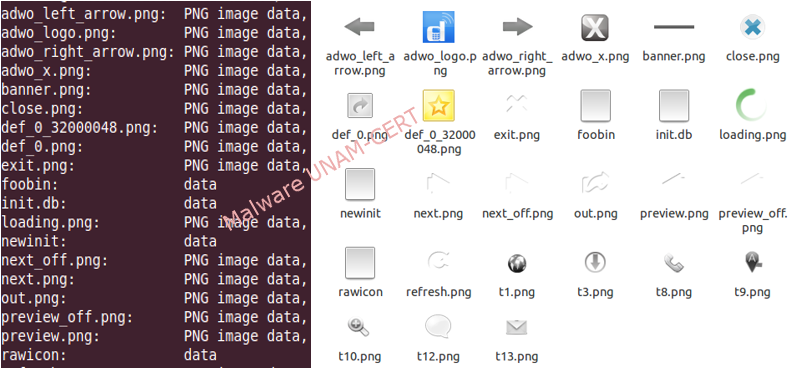
The assets/ directory contains several icons with PNG images and four files called foobin, init.db, newinit and rawicon of type “data”. These files are encrypted with AES and contain, amongst other things, two exploits that the malicious application uses to escalate privileges and install additional applications without the user’s intervention. These exploits are known as RageAgainstTheCage (CVE-2010-EASY) and Exploid (CVE-2009-1185).
Normal applications, such as the ones installed through Google Play Store, are stored in /data, which is the Android partition were the data, the configurations and the necessary files to the operation of the installed applications.
System applications, such as the ones preinstalled on the device, are stored in /system and a standard Android user does not have writing permissions and therefore cannot install or uninstall anything. This malware sample need to execute commands as root to be able to install another application.
The application decrypts with AES the files foobin, init.db, newint and rawicon using the key defined inside the class com.google.update.RU.
Once the files were decrypted, it was discovered that:
- The file foobin is an ELF (executable for Linux) with the exploit CVE-2009-1185.
- The file init.db is a Jar file that seems to be a copy of the sample with the same files in the assets/ directory: foobin, newinit and rawicon.
- The file newinit is an ELF with the exploit CVE-2010-EASY.
- The file rawicon es of type data.
The md5 hashes and their VirusTotal reports are listed below:
e789e154ad68e2cbb2d405220bc01529 foobin.decrypt
a6083f69ced5412b89a55658d33af175 init.db.decrypt
a6b6df55eb0404406f7b66879e34d581 newinit.decrypt
78437157c5d2df45be73caa5ed9b0a13 rawicon.decrypt
· RageAgainstTheCage
The sample uses an exploit known as RageAgainstTheCage, which takes advantage of the vulnerability CVE-2010-EASY to escalate privileges and install applications as root. This exploit creates “zombie” processes using fork() until the maximum number of running processes for a given ID, indicated by RLIMIT_NPROC, is exceeded and fails. Then, the parent process kills adbd causing it to restart. During restart it executes as root, however its permissions should change to those of the user shell afterwards.
Normally, setuid() would decrement the count of root processes and increment the number of processes run by the shell user. However the number of allowed processes for the shell user is at its maximum which makes setuid() fail and, because there is no validation to know whether the call to setuid() was successful, the process keeps executing as root. Since adb is still executing as root, this causes that, when using the command “adb –d shell”, you obtain a root terminal.
This vulnerability is fixed for Android versions 2.3 and more recent.
· Exploid
After its execution sends messagesusing the NETLINK KOBJECT_UEVENT protocol, which was designed to make processes hear kernel events, not to send messages through it. Because under normal circumstancesonly the kernel sends messages through this protocol, other processes running with root permissions assume that the malicious messages come from the kernel, also executing them with root permissions. This is achieved by creating a socket and specifying NETLINK_KOBJECT_UEVENT in the netlink_family parameter. The path to the exploit is indicated by a symbolic link in /proc/sys/kernel/hotplug so that, when invoked, it will run with root permissions.
Dynamic Analysis
The icon of the malicious app already install can be seen on the following image:
When the application is executed for the first time, it shows the instructions of the game. After this, the application starts.
Network Traffic
After executing the sample, the malicious accions begin in the background. This network traffic is related to the adware part of the sample which, as mentioned above, obtains information of the device to send it to a remote server.
First, the following GET requests related to Adsmogo were observed:
· cfg.adsmogo.com – 115.182.30.82
GET /GetInfo.ashx?appid=b2609a99a69045269897d92cc685d4b3&appver=275&v=1.0.3&client=2&pn=com.gp.solitaire&userver=461.0&adtype=2&country=us&nt=1&mno=310260&uuid=e8a1112658fdeb899033567722ef3e8c&os=2.2&dn=sdk&size=1280*768&cc=1&cm=418.61&ram=841176kb
· req.adsmogo.com – 115.182.30.67
GET /exrequest.ashx?appid=b2609a99a69045269897d92cc685d4b3&nid=0bb038b07ad24026b5841d29805fbc35&type=33&uuid=e8a1112658fdeb899033567722ef3e8c&client=2&adtype=1&country=us
The collected data is explained below:
| cfg.adsmogo.com | req.adsmogo.com |
| appid = App ID | appid = App ID |
| appver = App version | nid = AdsMOGO parameter |
| v = AdsMOGO SDK version | type = AdsMOGO parameter |
| client = AdsMOGO parameter | uuid = Universally unique identifier of the device |
| pn = App name | client = AdsMOGO parameter |
| userver = AdsMOGO parameter | adtype = Advertisement type |
| adtype = Advertisement type | country = Country |
| country = Country | |
| nt = Network type (1 mobile, 2 wifi) | |
| mno = Mobile network operator | |
| uuid = Universally unique identifier of the device | |
| os = Android version | |
| dn = Device name | |
| size = Screen size | |
| cc = Processor | |
| BogoMips = Measurement of CPU speed | |
| ram = RAM memory |
· r2.adwo.com 42.62.76.8
Afterwards the sample makes a POST request to send information in this order:
- “v” and “2” of unknown purpose
- Identifier of the advertisement
- IMEI, in this case is 000000000000000 because an emulator was used
- Device model: unknown
- Device name: sdk
- Cellphone number: 15555215554
- Name of the package that has the non-malicious app used by the trojan: com.gp.solitaire
· Other domains
There were also requests to appsrv1.madserving.cn/cr/394aff6985646490 (IP address 117.121.22.228), search.gongfu-android.com, search.best188.com and search.best188.net; however, this part of the analysis could not continue due to the domains being down. From otros reports about the sample’s malware family is possible to deduce that the last three were related to a C&C.
Other URLs were also found on the strings extracted from the application, as seen below:
Recommended links
Android/DroidKungFu uses AES encryption
Security Alert: New DroidKungFu Variant -- AGAIN! -- Found in Alternative Android Markets