Facebook comments carry out pharming against mexican banks
A fake email from Facebook was spread in December. The email shows a message about an alleged comment from Sammy Villanueva.
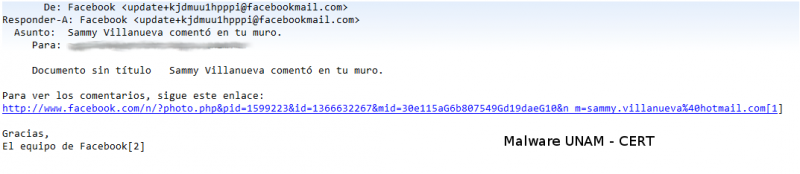
When the link is opened, it redirects to where it was downloaded a malicious executable file called ComentarioSammyVillanueva.exe.
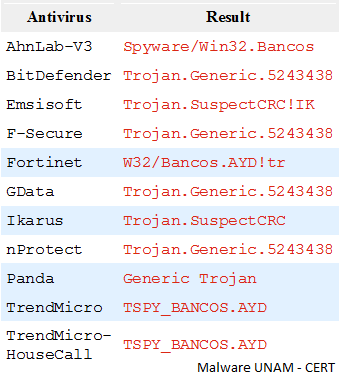
Analyzing the executable file with different antivirus engines to the present day 11 engines detect it.
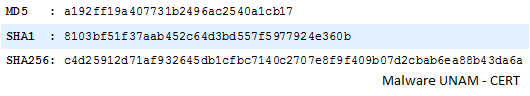
Its hashes are:
When executed, the malicious file is copied in %WINDOWS%\System32\tmss.exe, whose hash was verified to determine if they had the same code.
Therefore, due to the existence in %WINDOWS%\System, it can be executed from any directory in the PC's PATH. Despite this, the malware adds a registry key to execute the malicious code in each system startup.
KU\S-1-5-21-484763869-813497703-1177238915-500\Software\Microsoft\Windows NT\CurrentVersion\Windows\load: "C:\Windows\System32\tmss.exe"The malware modified the hosts file, containing the following content:
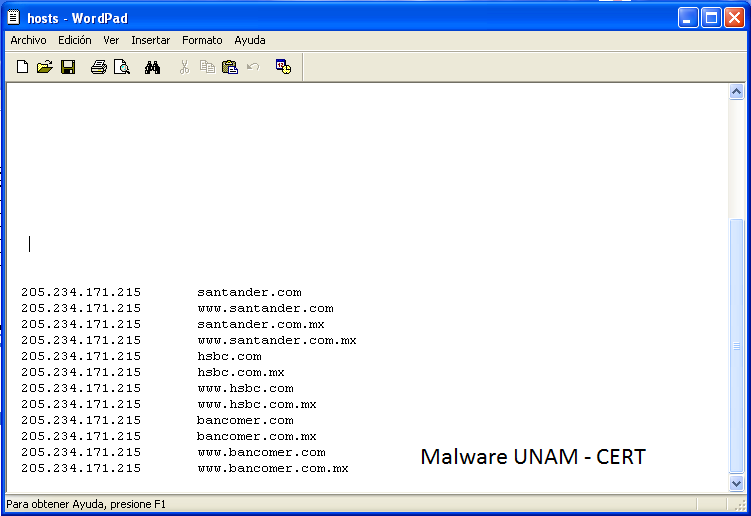
The malware continuously make DNS queries to the site quieroo.nom.es, which replies with the IP address added to the hosts file.
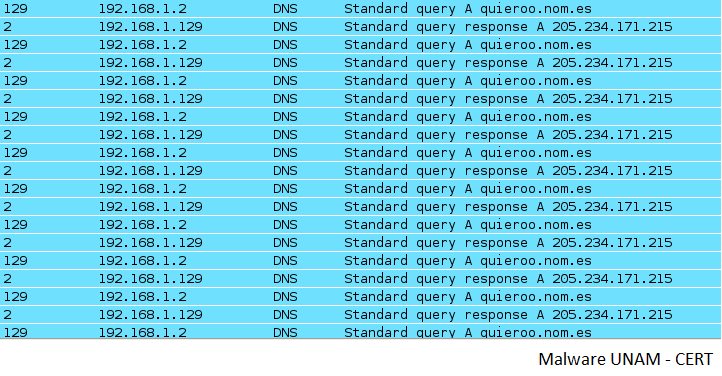
We had information that previously the malware was doing pharming to a site with IP address 189.201.18.170.
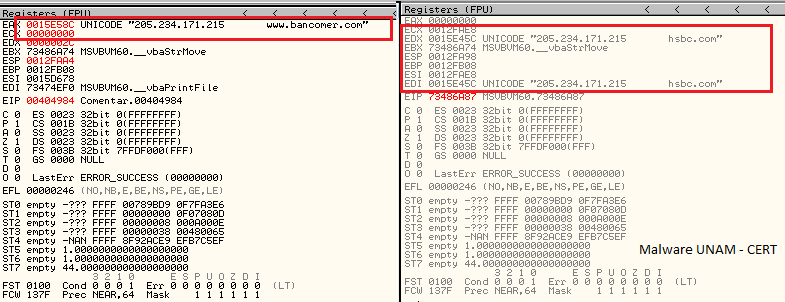
As the files have the same MD5, we verified how the host table is updated without any query to an external site. First, it seemed that the malicious sites were hosted in the same executable and it was also possible that the programmer created an algorithm to decipher the IP address and wrote it in the hosts file. However, using a disassembler we could not find any suspicious pattern. It was considered that the information was hidden using a simple ciphering like XOR or with bitwise shifts, some tools were used to look for patterns of this kind, but no information could be found.
Olly Dbg was used to debug the malware and it allows to identify the IP address origin. When the executable starts querying for the site quieroo.nom.es and the site replies with the address mentioned above, then starts to add that address to the hosts file.
The test was made using a different address in the DNS server and the query was replied with another address.
The main servers of this site are ns1.cdmon.net, ns2.cdmon.net and ns3.cdmon.net, the site is hosted in Chicago, Illinois.