Fake application to update bank account details steals information
A user notified UNAM-CERT about an executable file received. It was mentioned that the file was a banking Trojan.
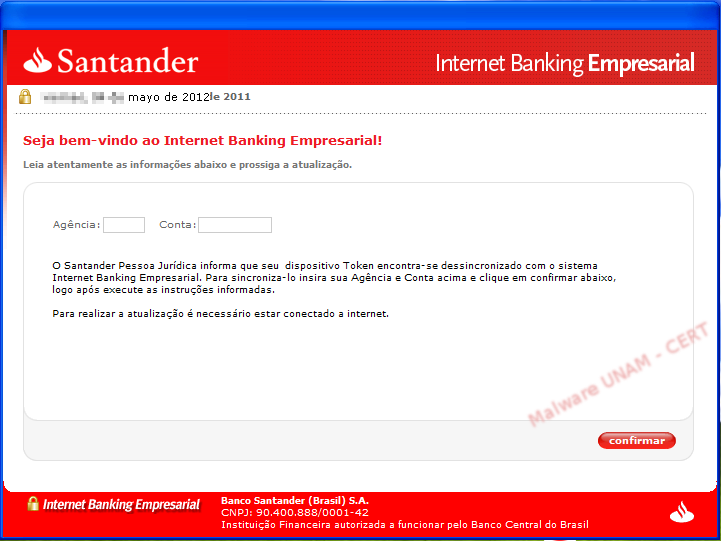
The file, called “sincronizar.exe” pretended to be a valid application from the Santander Bank.
At the time of the analysis, the file was detected by 27 antivirus engines and classified it as a banking Trojan.
We could not identify the programming language in which it was written and, during the string analysis, we did not find any clues that showed us the objective of the malicious file.
During its execution, the sample connected immediately to a remote host. On the captured traffic we could see the DNS request and the IP address that responded, as well as a request to the site /css/ip.php.
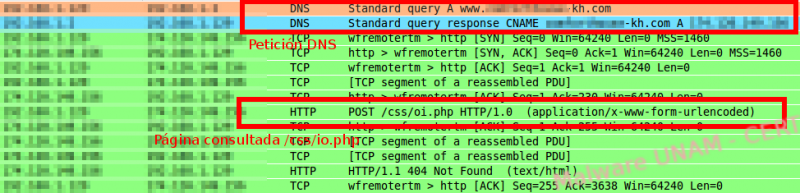
We also discovered that the application sent the name of the computer in the variable called “subject”; however, by the time we did this analysis, the page was no longer available.
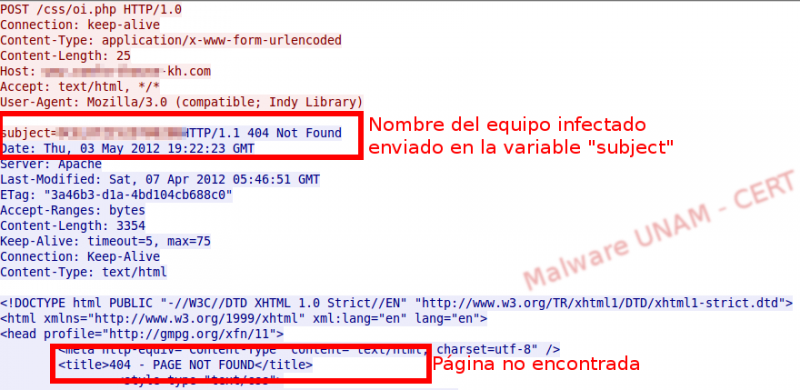
Thus, it sent an error message when starting.

However, the error message was not send by the process sincronizar.exe; a child process, called Atualizar.exe, was created from the original sample.

The program sincronizar.exe, when executed, created the file Atualizar.exe and executed as well, creating a process. Atualizar.exe was located in C:\Documents and Settings\[User]\Local Settings\Temp\RarSFX0\Atualizar.exe.
Atualizar.exewas written in Delphi. After being analyzed on VirusTotal, 29 antivirus engines detected it as malicious and classified it as a banking Trojan.

Therefore, sincronizar.exe is only a compressor of the real malicious file, Atualizar.exe. This is the reason why we could not identify its programming language.
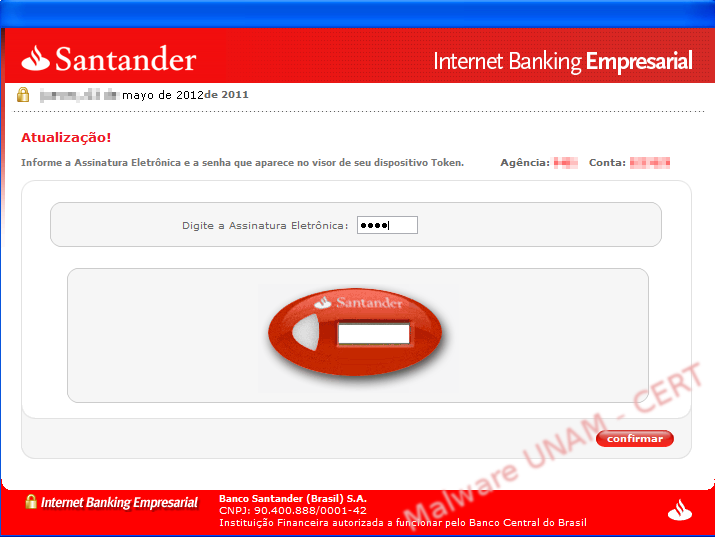
After the error message, the fake application that pretends to be from the Santander Bank finally appears. It requested two numbers: Agency and Account (Agência e Conta in Portuguese).
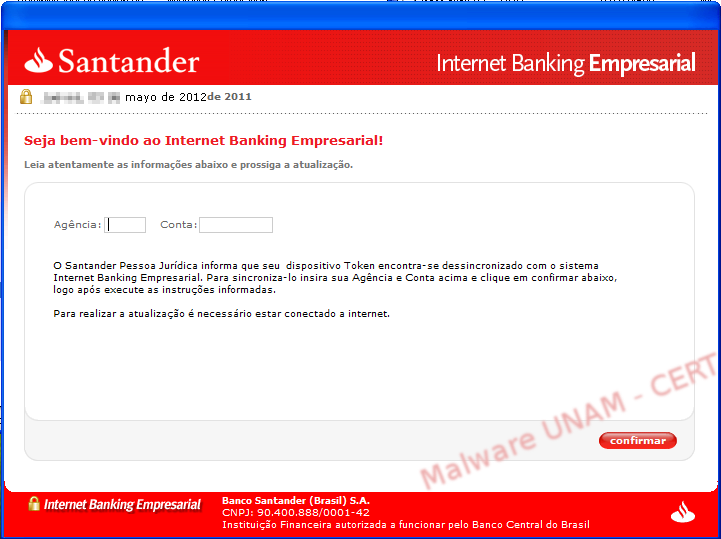
We wrote the requested information and discovered the application only validated the number of digits: 4 characters for the agency and 7 for the account. After clicking on the “confirmar” (confirm) button, the information is sent to the site /css/io.php, resending the subject variable with the computer’s name and the message variable with the captured data.
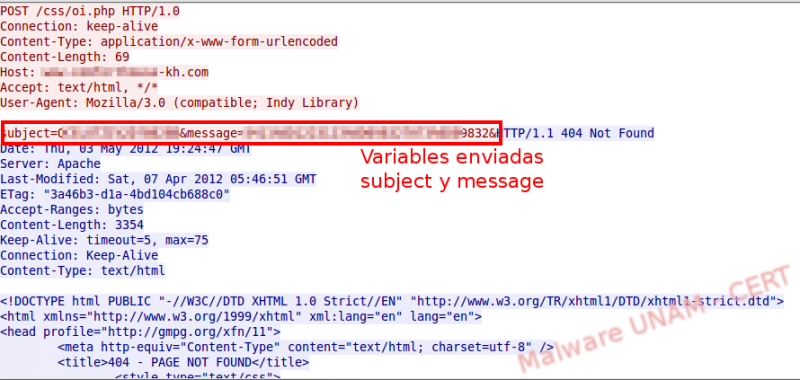
In each screen, displayed by the malware after clicking the button “confirmar”, the information was sent to the external host.

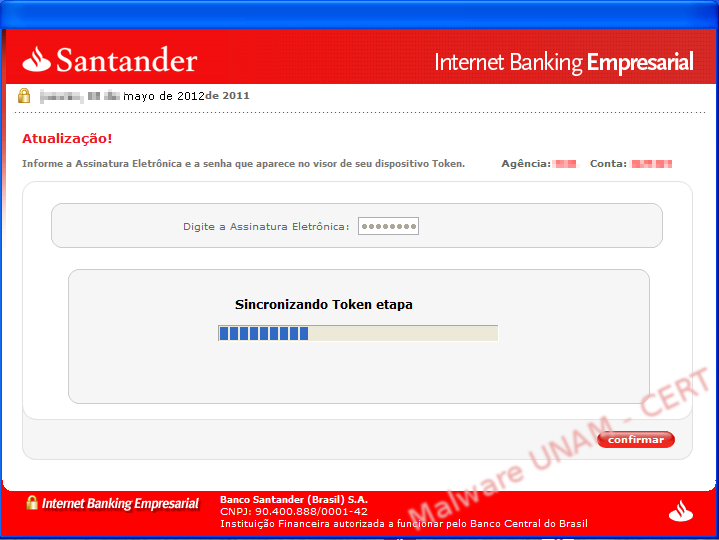
In the end, it supposedly synchronized with the token, showing a progress bar of the update.
The user’s data was sent to a website absolutely unaffiliated to Santader. Luckily, by the time we analyzed the sample, this website was no longer capturing the stolen information. However, to avoid being victims of this kind of theft, is important to use common sense when downloading and executing programs from the Internet