Fake applications keep stealing information using social engineering
On a previous post, we informed about a fake application that pretended to come from the Santander Bank. In the same site we found an executable file called BKINTER.exe.

This file was detected by 25 antivirus engines.
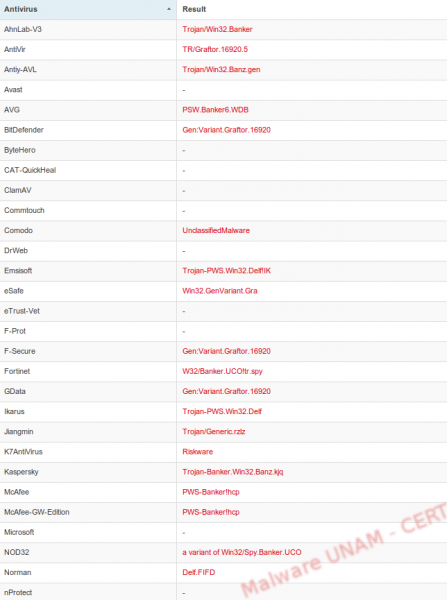
Similarly to the last time, after copying the file on the desktop of a computer with Windows XP, we saw that the icon looked like a legitimate bank application.

After clicking the file, the following screen, that invites the user to click on the “Enter” button, was displayed:

When the button is clicked, the application requests a user and a password.

As the last time, it forced the user to type a username and a password twice, after sending a message declaring the data as invalid. As we commented on the last post, this is done to avoid user’s mistakes since the malware writers have no way of validating that the data is correct.

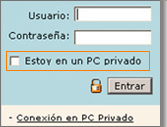
Generally, criminals will attempt to clone the website of the bank so that the users don’t suspect they are being victims of a theft. In this case, the session login of the fake Bankinter application is very similar to the original one on the blue section. An image of the legitimate session login is shown below.
Furthermore, Bankinter authenticates through a card of coordinates to carry out online transactions. For this reason, on the next screen, the fake application asked me to supply the card of coordinates.
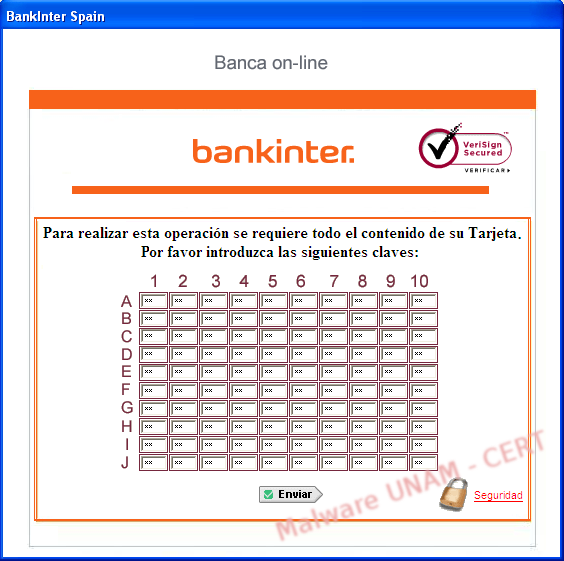
We wrote bogus information on the form and after clicking on the “Send” button the application opened local port 1048 and connected to the same remote site that we mentioned on the last post. The captured information was processed on the site /images/pop.asp (last time it was on the popa.asp site).
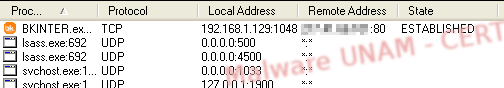
On the string sent, each data entered is placed in numeric variables: variable 1 corresponds to the user, variable 2 to the password and variables 3 and 4 correspond to the user and the password provided by the user the second time and the rest of the variables, from 5 to 104 correspond to the fake data of the card of coordinates.
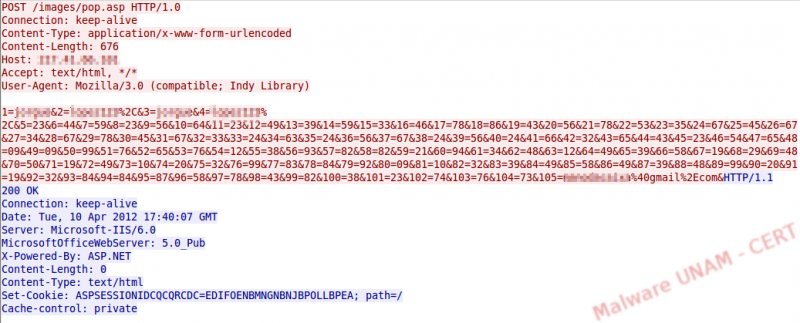
The content of the last variable, the 105, showed a gmail address; we changed this email for one to which we had access. The information captured by the application arrived to our mail inbox shortly afterwards.
After sending the data, the application displayed a message about the alleged operation, indicating it had been completed successfully.

After clicking the “Final” button, the application “thanked the user for the cooperation” and finished.

The email sent to out inbox had a different format from the previous analysis, although it also came from the site pop.asp.
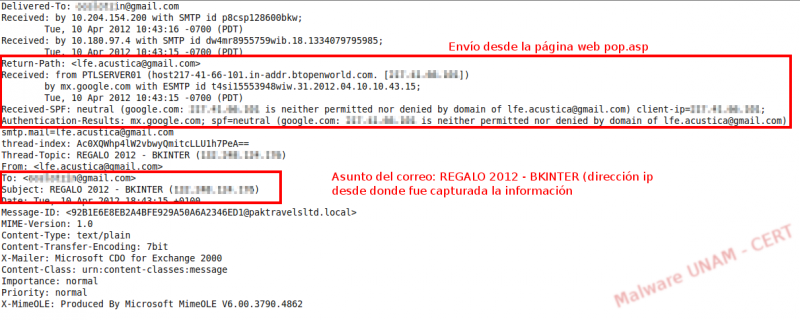
In this occasion, the body of the message contained the information of the card of coordinates.

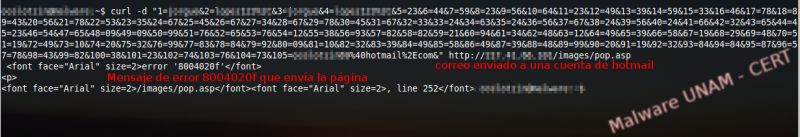
The application also validated the use of a gmail account, because we made several attempts with different accounts and it returned an error message. On the image below, the string sent to the website and the error message it returned, are shown.
This malware sample was very simple and only tried to use social engineering to collect classified information from its victims. It is very important to use our common sense when a message in an email asks us to download and execute a program, especially if it requires classified information such as the matrix of secret numbers of our bank account.
Fortunately, this executable file is detected by many antivirus engines.