Fake E-mail from tarjetasbubba.com
The Computer Emergency Response Team UNAM-CERT received a report which notified a suspicious email campaign from tarjetasbubba.com service. A link contained in the text body led to the malware piece.
The malicious downloads came from a rogue website whom domain posed as belonging to the service "Postales y tarjetas virtuales" of tarjetasbubba.com.
The official site page is: http://www.tarjetasbubba.com/
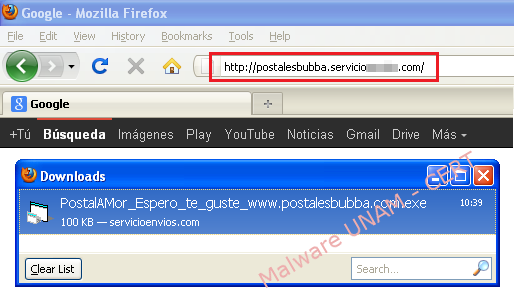
While executing malware in a controlled environment, the piece starts up a process with the same name than the executable file: PostalAMor_Espero_te_guste_www.postalesbubba.com.exe
The process shows up two interesting issues, the first one is in the Process Explorer tool Description column, which shows the value "NetBeans IDE". The second one is spotted out in the column "Company Name", where the string "Oracle Corporation" appeared.
The malware uses the name NetBeans trying to impersonate a valid process which main purpose is to deceive their victims.

By inspecting the executable file with PEiD and Exeinfo PE scanning tools, the results shows up that it’s programmed with Visual Basic language.

By running string's analysis, it can be concluded that the malware was programmed in Visual Basic with the Integrated Development Environment (IDE) Microsoft Visual Studio.
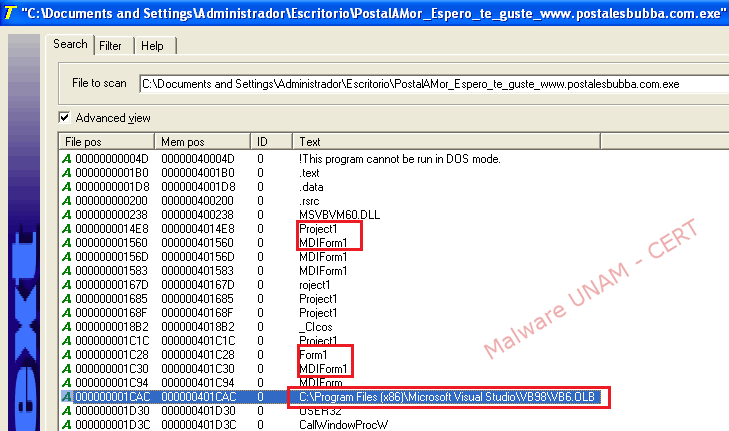
Some other important data was able to be quarried, such as the path to the file PDB, which is generated during the compilation of source code files: C:\Users\JUNIOR\Desktop\Project1.pdb.
This step also shows the user's Windows session where the malicious software was created.
Within the malware code, the section Company Name has the value of Oracle Corporation, in the File Description using the name NetBeans IDE in a version 7.2.0.0.
The Original Filename of the malicious sample is "netbeans.exe".

The malware creates an executable file "svchosts.exe" with the location C:\Documents and Settings\Administrator\Application Data. To ensure the file execution on each system start up, it generates the registry key "Google Inc". This new executable file tries to impersonate a legitimate Windows process, not trying to interact as a malicious threat.

While performing a search for the malicious file signature "PostalAMor_Espero_te_guste_www.postalesbubba.com.exe" in the VirusTotal service, no records are shown up, what implies that by the time this text was written, any service was able to detect this threat as malicious.
