Fake email spoofs SAT in order to distribute malware
UNAM-CERT received a report of an email usurping the identity of the Mexican Tax Administration Service (SAT, Sistema de Administración Tributaria) that alleges statements related incidents, in order to review this, users had to consult a document included in the email. The message is shown in the image below:
In email body, there was a link that redirected to the download of a compressed ZIP file with the name “exp_230157.zip”.
The website referred by the link is hosted in Belgium, and the reference mentioned before was to a script containing a second redirection to the server hosting the malware.
The website that hosted the malware is located in Romania. If the download link was accessed directly in the browser, it showed the message “File not found”, this was because of a non-access validation that should be performed through the first redirect, that is made when clicking on the link contained in the email.
Below is an image showing the home page of the web server that hosted the malware:
When unzipping the file “exp_230157.zip” the executable “vista.scr” is obtained.

The sample was executed in a controlled environment without Internet.

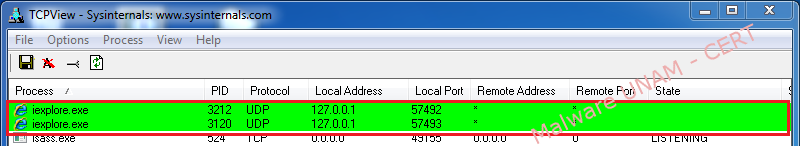
“vista.scr” starts up the process “tinstall.exe”, which in its own way, initiates “explorer.exe”

The process “iexplore.exe” launches the browser that the user has set as default with the fake SAT message.
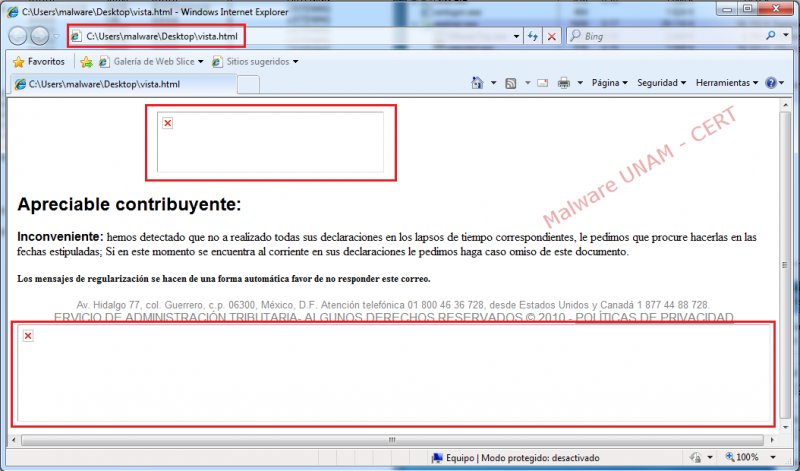
Below is the file “vista.html” with the message addressed to tax payers:
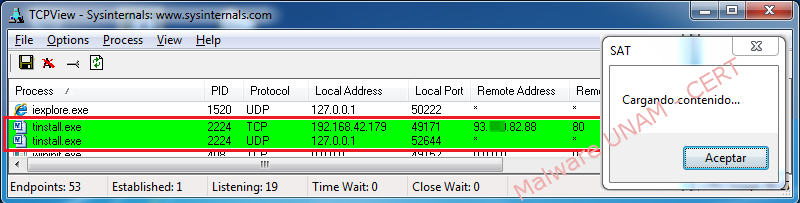
The process “tinstall.exe” makes attempts to synchronize with a web server hosted in Romania. It also shows a window named “SAT” and the message “Loading content…”
The malware sample creates three files and then deletes itself:
Below is an image showing the created files:

The file named “bdel” (without file extension) is a plain text file that indicates the path where the malware was executed.

The file “vista.html” contains the message displayed in the browser and also four URL that refer to the official website in order to download legitimate images.
When leaving malware sample interact with the Internet, it can be observed in the web browser the message to taxpayers with official images from sat.gob.mx site.

Below is the network traffic that requests the SAT official website images.
In the process activity is shown “win64.exe”

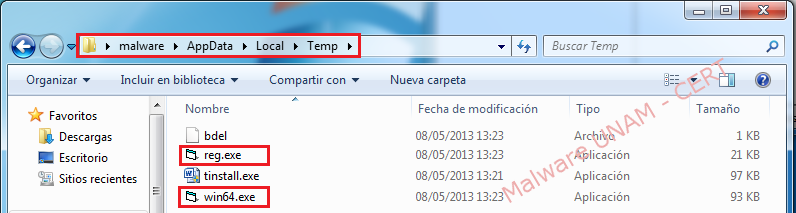
Below it is shown the registry key “win64” and the files “req.exe”, “win64.exe”, created from the interaction of the malware with the Internet.
The new files are created in the path “C:\Users\malware\AppData\Local\Temp”.
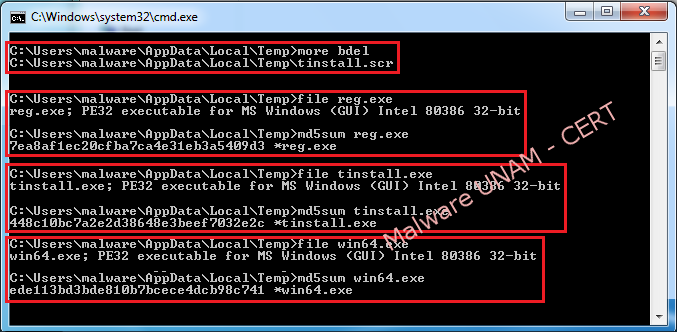
Next, the md5 signatures of each one of the files:
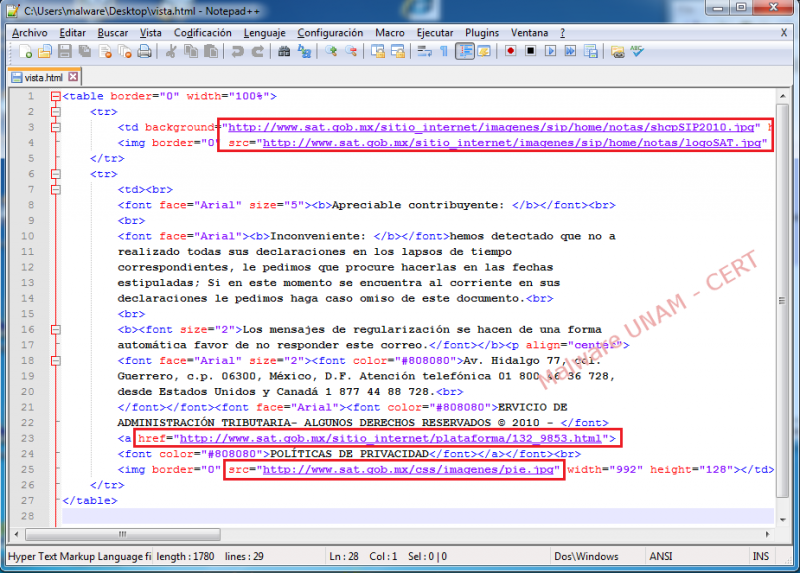
In a string analysis to the binary file “vista.scr” it was found the structure that creates the file “vista.html”.

A domain that is not consulted while executing the sample and the original name of the binary (instala.exe), were also found.

Below the image of the file referred into the string analysis.
Making an analysis of the sample in VirusTotal service, it shows that 9 out of 46 antivirus detect it as malicious. Below the report: