Phishing site – identity theft to Hotmail
UNAM-CERT received a notification informing about a possible identity theft campaign. The threat arrives by email as a warning about a probable fraudulent activity, either from the user or from the email address.
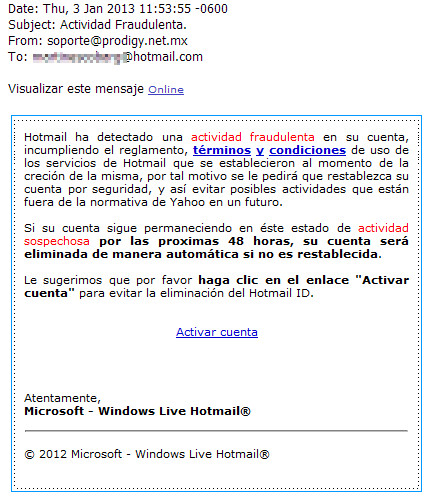
The email makes allusion to one of the most common strategies used by attackers on fraudulent emails: the sense of urgency that incites the users to act fast to avoid being affected on the service referenced on the email “if on the next 48 hours…” the user fails to do something.
When clicking the link that offers the alleged solution to the problem, the user gets redirected to another server, which in turn redirects to one more server with a site that looks very similar to Hotmail’s.
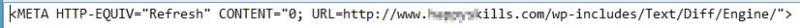
After analyzing the samples obtained from the different leaps, we realized that there is no JavaScript code used on the redirections, as it is normally done. The headers of the file, written in HTML, were modified to difficult the detection of the malicious activities.
Examples of the malicious URLs are shown below:
http://www.xxx.org/modules/mod_custom/tmpl/
http://xxxwildcat.writingnovelsthatsell.com
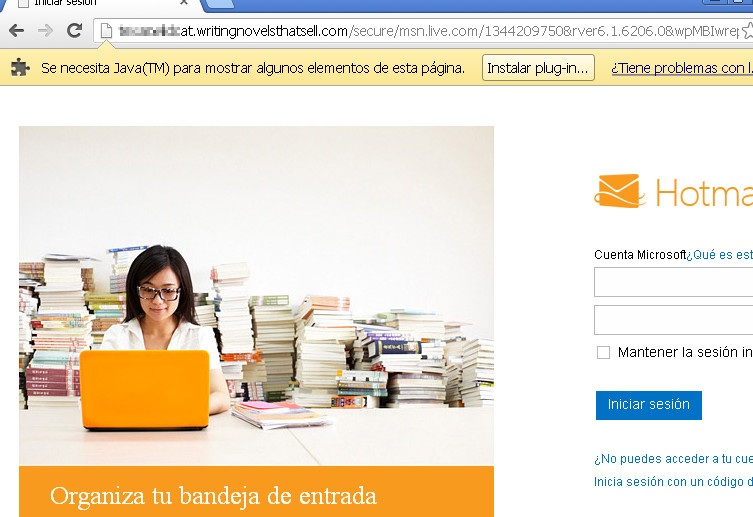
On the fake Hotmail website, fake access credentials were used to observe when the data got redirected to another server.
It is advisable to deactivate the execution of JavaScript code on the browser; otherwise, malicious code could be executed. It is also important to verify the reliability of a website before accessing it; to do this, we can check the address bar to make sure the URL is consistent to the site we want to visit.