Ransomware that usurps the identity of Law Enforcement Institutions in Mexico
In one of ourprevious publications on this blog, we presented the analysis of a malware sample that hijacked the user's session on the infected computer, usurping the identity of the Mexican Federal Police in order to raise money in exchange for the rescue.
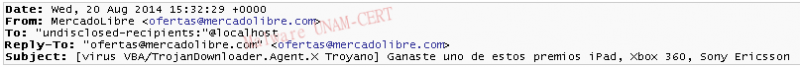
Recently,several cases of infections caused by a ransomware, that attributed itself the identity of Law Enforcement Institutions to carry out extortions, were reported. The locked window is shown below:
It displays some information about the infected user, such as:
- Public IP Address
- Country
- Region
- City
- ISP (Internet Service Provider)
- Operating system
- User Name
This particular sample is hosted in the infected with the name "cache.dat" which, when verified with the file, tool, shows that it is an executable for Windows

We renamed the sample to “cache.exe” and ran it in a controlledenvironment without Internet access.

The process"cache.exe" remains active for a couple of seconds and, immediately after closing, the trojanized process "svchost.exe" starts.

DNSrequests to resolve the domains “n**fw.net**”, “x** lx.com” and “k**qs.ru”.

After the hosts file was modified to resolve the domains requested by the sample, synchronization requests to port 80 were observed, which is associated to web services.

Below,theSYNrequestscan be seen:

Subsequently, we proceeded to start a web service:

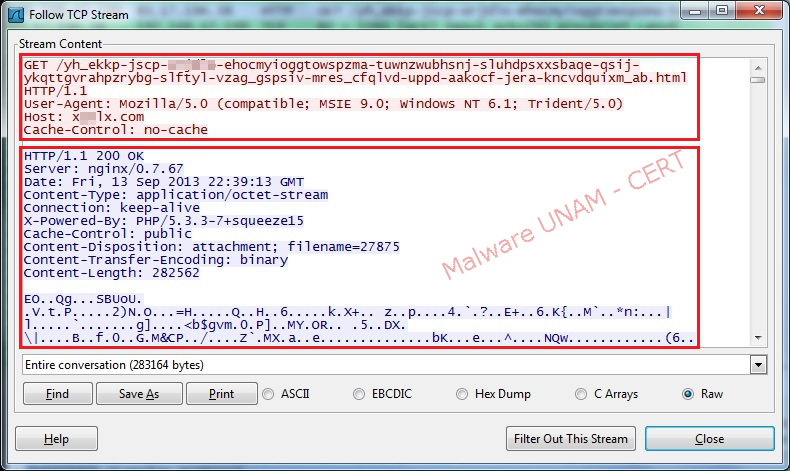
Once the sample resolves one of the requested domains, the web service makes a GET request, through port 80, to load an HTML file.

On the image below, the GET requests, with a filter in Wireshark, can be seen.

The activity in theWindows Registry consists on the creation of the key "shell" in the path: HKU\S-1-5-21-448539723-1770027372-725345543-500\Software\Microsoft\Windows NT\CurrentVersion\Winlogon with the value: "explorer.exe, C:\Documents and Settings\Administrator\Application Data\cache.dat".
The above configuration loads winlogon when the user logs in with the settings established by the malware: to start the process "explorer.exe" along with "cache.dat", hosted in the path C: \ Documents and Settings\Administrator\Application Data.

The path where the file "cache.dat" stores itself in Windows XP systems is shown below:

With the tool Process Monitor, the creation of the file "cache.dat" conducted by the Trojanized process "svchost.exe" can be seen.

It is also possible to observe the creation of the registry key "shell", which starts the malware at every system startup:

About two minutes after the infection, the window that locks the user's session with the logos of the Ministry of Public Security (Secretaría de Seguridad Pública in Spanish), the Attorney General's Office (Procuraduría General de la República) and the Federal Agency of Investigation (Agencia Federal de Investigación), and the coat of arms of Mexico, information about the infected computer, the clauses that specify why the computer may have been blocked and indications of how to pay the ransom for the kidnapping of the team. The ransomware window is displayed on the image below:



As a test, a random PIN code of 19 digits was entered to see the behavior of the application. From the menu of amounts the value of $2,000 pesos was selected; the other four quantities available were: $250, $500, $1,000 and $1,500 Mexican pesos.

Once the“PayUkash” button was pressed, a message indicating that the code or serial number entered was incorrect appeared and that the payment should be done again.

The GET requestto the malicious server once the malicious sample was allowed to interact with the Internet is shown below:
Incase the users try to boot into "Safe Mode", they won’t be able to, due to a Windows shutdown caused by the configuration of the ransomware.


On the image below, thewindows displayed when the "Safe Mode" fails to start, is shown:


For this particular sample, tests were performed on both a Windows XP operating system and a Windows 7 in order to regain control of the system and to take security measures with respect to the information stored.
How to remove this ransomware in Windows XP?
Once the computer is infected, the malware does not allow the start of the "Windows Task Manager" with the key combination CTRL + ALT + DEL, nor booting the system in "Safe Mode". The proposed solution to start the system with a Linux Live CD, in our case the distribution used was Ubuntu 12.04.
- After turning the computer on, press theF2 key to enter the BIOS (Basic Input / Output System). Go to the "Boot" tab and change the boot order of the devices with the "+" or "-" keys, leaving the "CD- ROM Drive" option first. Note that this procedure may vary depending on the computer.

- Once the boot order is set correctly, press the F10 key to save the changes and exit the BIOS, this action should display a confirmation message about saving the changes and we must select the affirmative choice. Immediately after this the system restarts automatically..

- With the Live CD inside the computer, the "Ubuntu 12.04" operating system will start.

- After the user picks the preferred language in which the operating system will be displayed, the button "Try Ubuntu" must be selected to start the Ubuntu test distribution.

- Next, go to the icon of the "Personal Folder" (HOME), shown in the left sidebar:

- Once the browser opens, select the partition of the Windows file system, in our case the 27 GB hard drive.

- Afterwards, go to the path: "Documents and Settings\Administrator\Application Data" where "Administrator" is the user of the infected computer.

- The files "cache.dat" and "cache.ini" must be deleted.

- So far the threat has been removed, so the only thing left to do is to reboot the system and enter Windows normally.


- So far the threat has been removed, so the only thing left to do is to reboot the system and enter Windows normally.
Once the user has logged in correctly, it should delete the registry key that the malware generated. To do this, go to the "Start" menu and select "Run..."
- To open the Windows "Registry Editor" you must type the word "regedit" and click on the "OK" button. Later, head to the path HKU\S -1-5-21-448539723-1770027372-725345543-500\Software\Microsoft\Windows NT\CurrentVersion\Winlogon and eliminate the registry key with the name "shell".

- Another way to remove the registry key is using the Autoruns tool. For Windows XP, the key appears segmented, so you must deselect the five fields.

- You can also select the "Jump to ..." option to go directly to the path where the registry key "shell" is hosted and remove it manually.

The registry key created by the ransomware is shown below:


How to remove this ransomware in Windows 7?
To delete the malware in the Windows 7 operating system, you must perform the same steps described for Windows XP but taking into consideration the user name and the location of both the key and the binary file "cache.dat".
- The created registry key is:
HKU\S -1-5-21-1378332399-1373618527-3381202181-1000\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\shell" explorer.exe, C:\Users\malware\AppData\Roaming\cache.dat"

- The executable file to be deleted is in the path:
C:\Users\malware\AppData\Roaming\cache.dat

- Finally remove the registry key "shell".
