Regional malware still propagates itself through a botnet
A few days ago, an administrator sent us a sample found on a computer classroom, to be analyzed. It had been propagating through USB devices and had not been detected by the antivirus used so far.
The sample was provided as found in the removable storage devices. Usually this kind of malware stores itself in the RECYCLER directory (that serves as the recycle bin of the device, is hidden and has special permissions). The structure of the infected directory looked as follows:

The name of the malware was 13a0ea84.exe; however, names like this make us think that the malware uses an algorithm to generate names randomly.
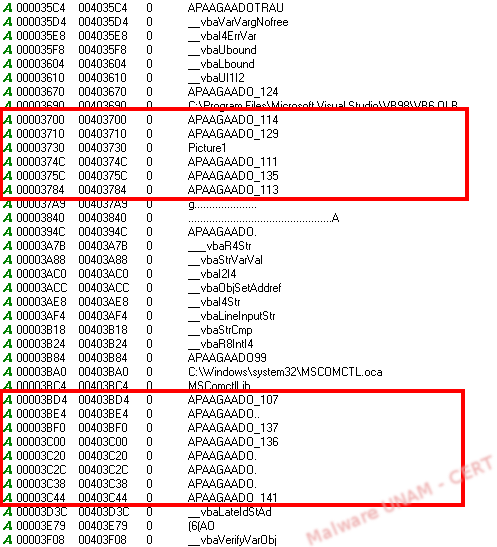
The sample was not packed by any tool or algorithm and, because of the strings found, it was most likely programmed in VisualBasic. Many of the strings discovered in plain text were “APAAGADO”, which is a badly spelled word in Spanish for “turned off”, followed by a number.
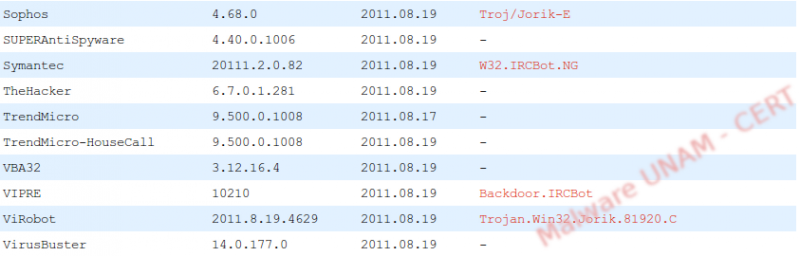
The file was detected as malicious by 16 antivirus engines.

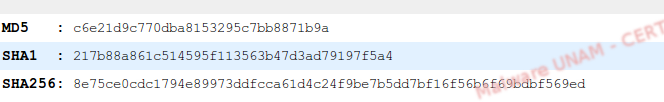
Its signatures are shown on the image below.
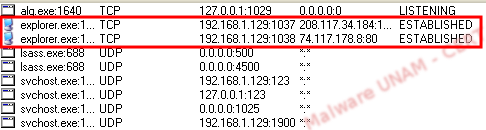
During its execution, process 13a0ea84.exe modified the registry key HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\AppData, subsequently closing the process. After which, Explorer.exe was injected with malicious libraries to turn it into a trojanized process.
Explorer copied the original executable, 13a0ea84.exe, to C:\Documents and Settings\[User]\Program Data with the name Rmpspj.exe, which was randomly generated. We know the names are produced randomly because on a previous occasion the file’s name was Ldxaxl.exe.
It also created this registry key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Rmpspj.
Afterwards, it deleted the malicious file from its original location. For this analysis we had stored the sample on the Desktop, from where it was deleted.
Immediately after that, the sample started making DNS requests to the website api.wipmania.com, which is a service used to get the geographical zone of an IP address.
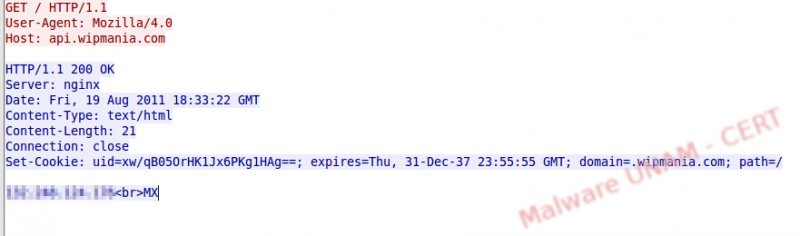
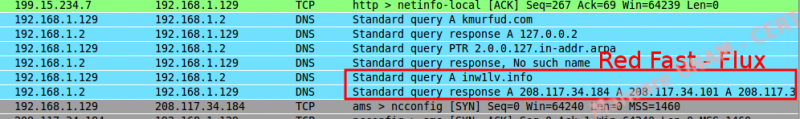
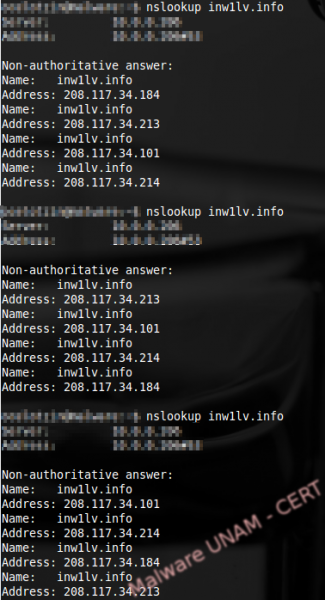
It is possible to know that we are dealing with a Fast Flux Network because when trying to resolve the name of the host with the nslookup command, it returns multiple IP address in different order, as shown on the image below:
The traffic captured from the botnet showed that it connected to the ##center channel, on the 4shared.com website, and downloaded additional software to compromise the computer even more.

The first executable file downloaded was called newtorres.exe and we obtained it from the captured traffic.

After analyzing it using VirusTotal, we found out that it was detected as malicious by 13 antivirus engines.
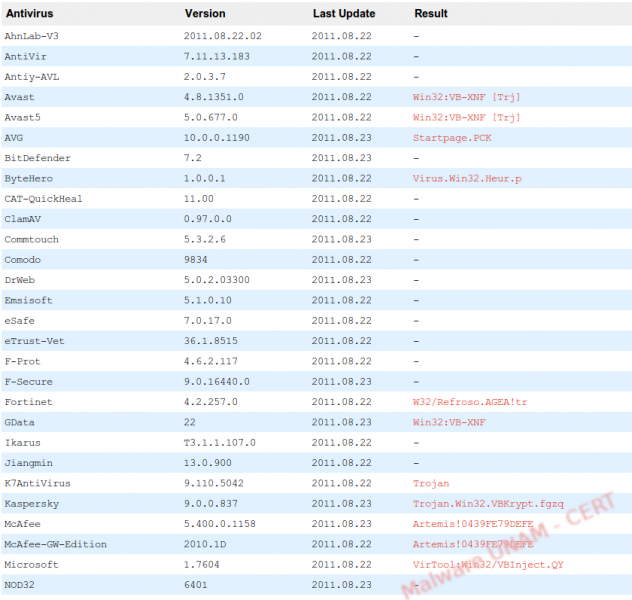

Its digital signatures are shown below:

During the analysis of the strings we observed the word “GROCERIA” followed by a number.
When the sample was executed it had a similar behavior as its predecessor: using the api from wipmania it obtained the geographical position through the IP address of the infected computer, made DNS requests to the Fast Flux network to finally connect to the botnet.

For a short period of time there was no activity; however, after some time it connected to a channel on the C&C server and we were able to observe the communication, which showed what looked like a pharming attack on the computers controlled by the IRC.

Nevertheless, the hosts file on the computer was not modified and the fake site was not activated, even though the IP address was active and with http service at the moment of the analysis.
The sample attempted to download two more files, robertiniii.exe y fdbfdf542.exe, from the 4shared website, but the files were not available.

As the previous sample, it copied itself to C:\Documents and Settings\[Usuario]\Datos de programa\Rmpspj.exe with a random name and then deleted itself from the original location.
The sample created a registry key for the new executable at HKCU\Software\Microsoft\Windows\CurrentVersion\Run\.
Finally, the Process Explorer application used on the analysis got injected with malicious libraries and became the one making the connection to the botnet.