SPAM email: Your new Facebook password
At the start of the week, we received a notification about a spam email that is being spread in a startling manner that even so far, we got some of those emails, which have an attached file, called New_Password_IN75652.zip.
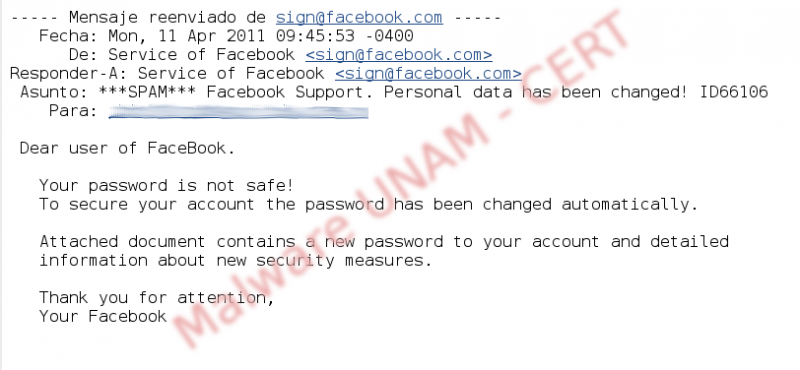
In the picture above, it is shown the email message, which notifies that the receiver's Facebook account has been changed and inside the compressed file, is the new password.
Inside the compressed file is the New_Password.exe executable, the following antivirus engines detect it as a threat:
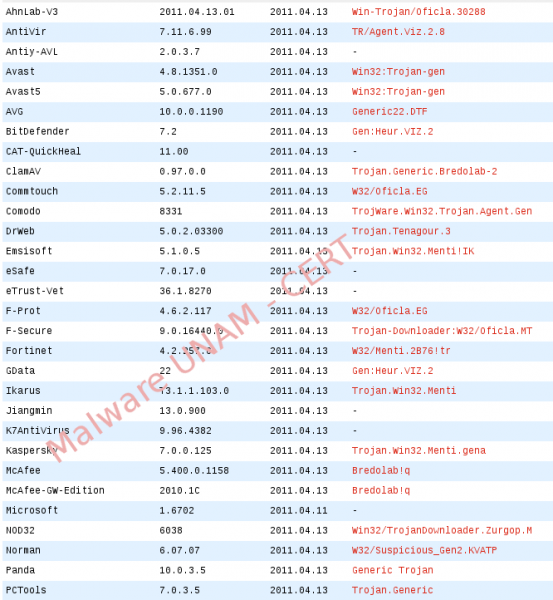
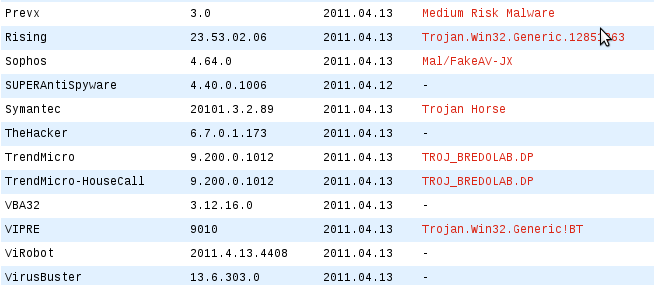
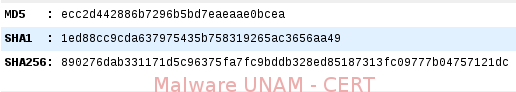
Its hashes are the following:
At the beginning of sample analysis, we executed it in a laboratory where it had not been installed the Microsoft Office Suite and it only was downloaded the document.doc file, from hxxp://profmiale.ru/TGQW4nHJOS/ and it was opened in Wordpad Application.
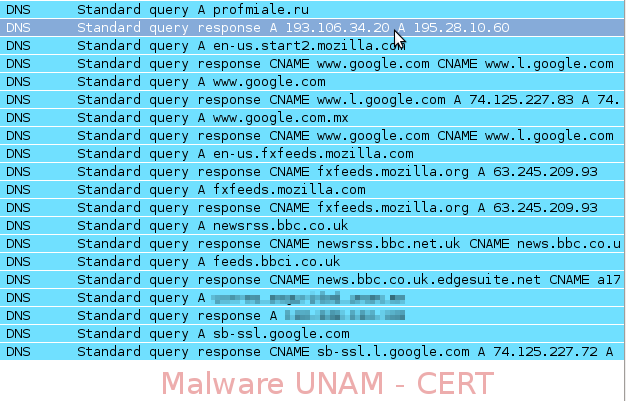
In addition, it performed some DNS queries to several domains.
Supposing that the malware could be exploiting the MS Office (MS11-023) vulnerability whose patch Microsoft just released this Tuesday and for its classification of important, according to the security bulletin, we installed Office 2003 in our laboratory and we repeated the analysis.
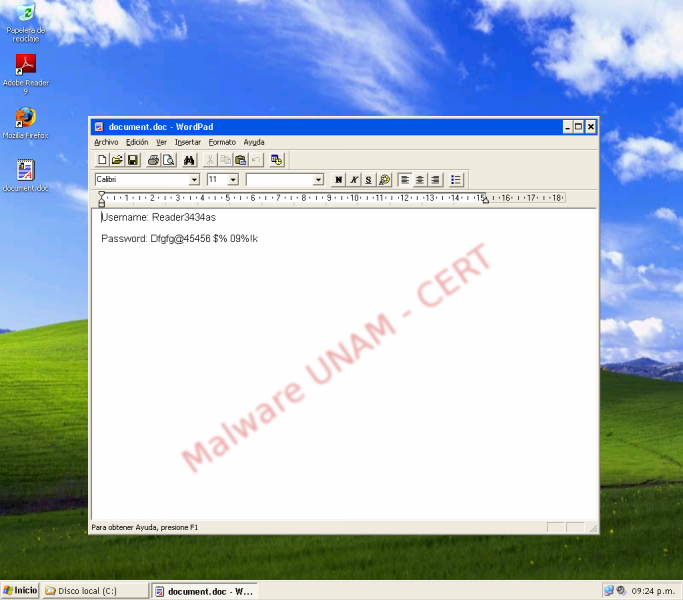
After a few seconds, it opened the document.doc file (MD5=1f62a7c87434e7af5a16a97c80387def), showing the alleged new information for the Facebook account.
Username: Reader3434as
Password: Dfgfg@45456 $% 09%!k
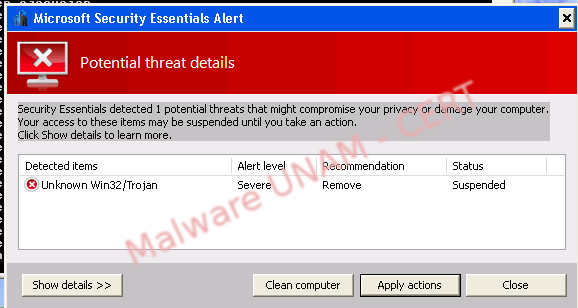
Immediately, it decreased the Windows desktop resolution and showed an alert window of an alleged application called Microsoft Security Essentials, which, warns about a detected threat in the computer.
No matter what button is clicked on, it appears another window pointing out that is required an online scan.
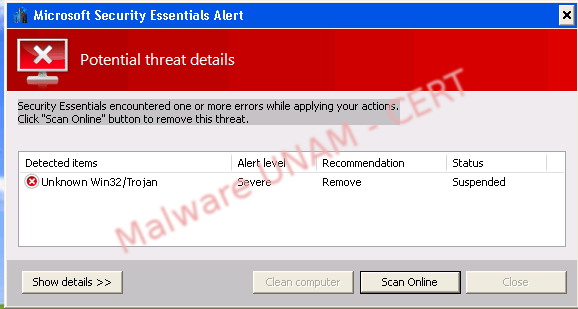
Apparently, the alleged tool is scanning the computer, but actually is carrying out the downloading of several executable from Internet.
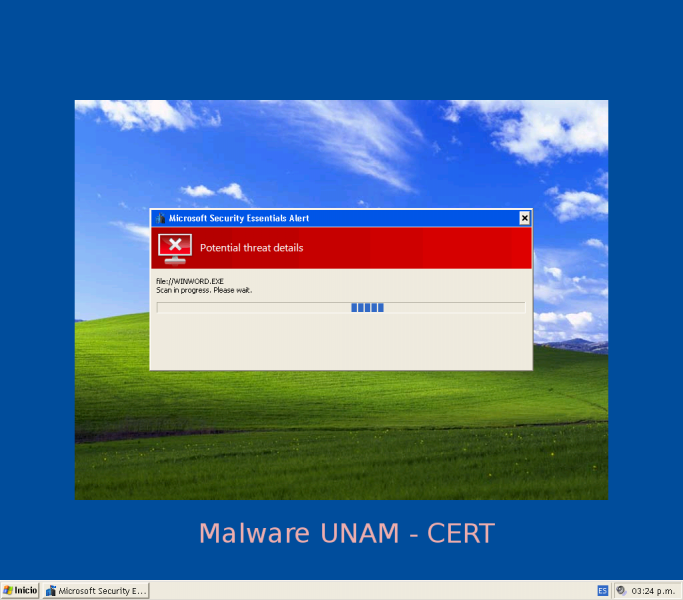
Once finished the alleged scanning, it shows a dialog warning that was found a solution that will allow remove the detected Win32.PAV.64.a trojan by the tool and it is necessary to restart the computer.
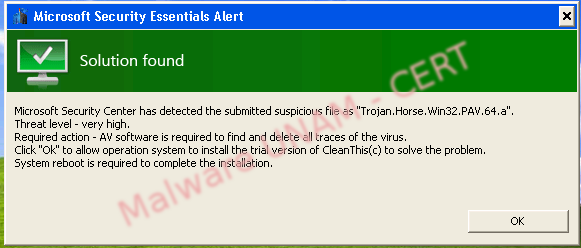
Then, the computer, as expected, was restarted and during the SO startup, again, appears the Start screen of an alleged antivirus tool called CleanThis.

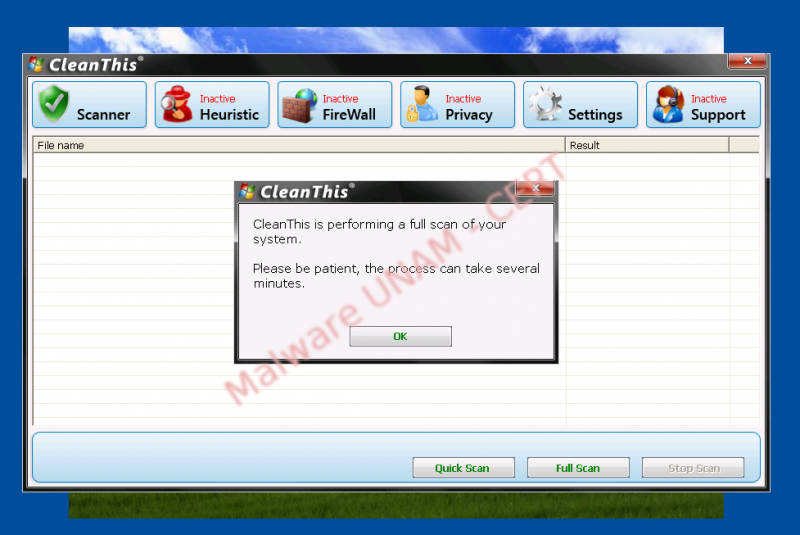
Later, it notifies that is performing a complete system analysis.
Moreover, it shows us results of the alleged detected threat and at that moment, loads the Windows task bar, a tool's icon and the recycler bin icon, on the desktop.
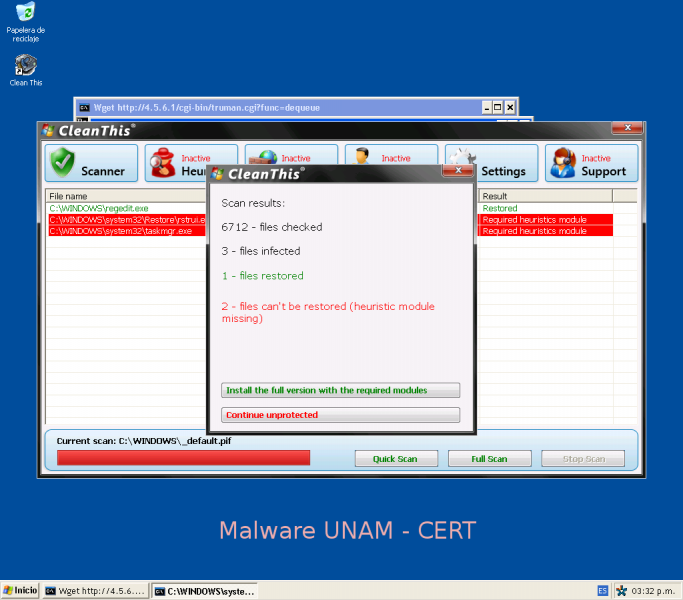
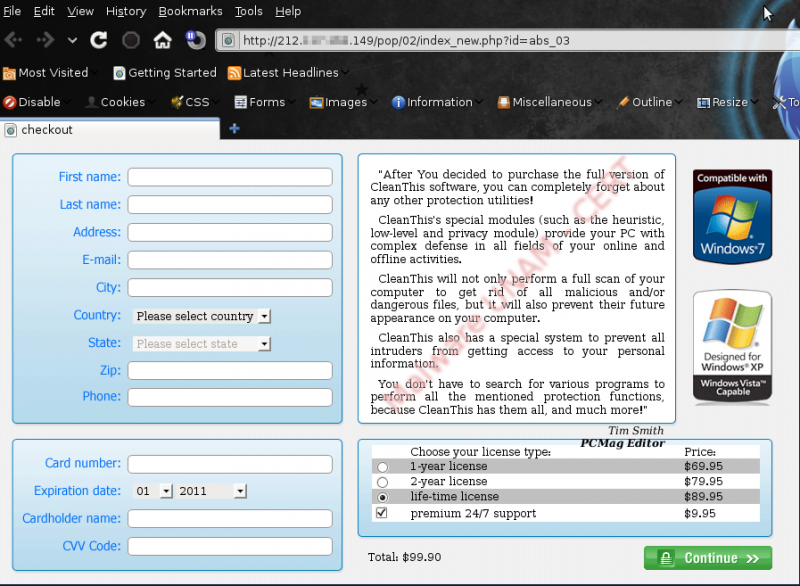
As expected, when is performed the threat removing, the application opens a form asking user information and exhorts the user to buy a proper version to remove the detected threats.
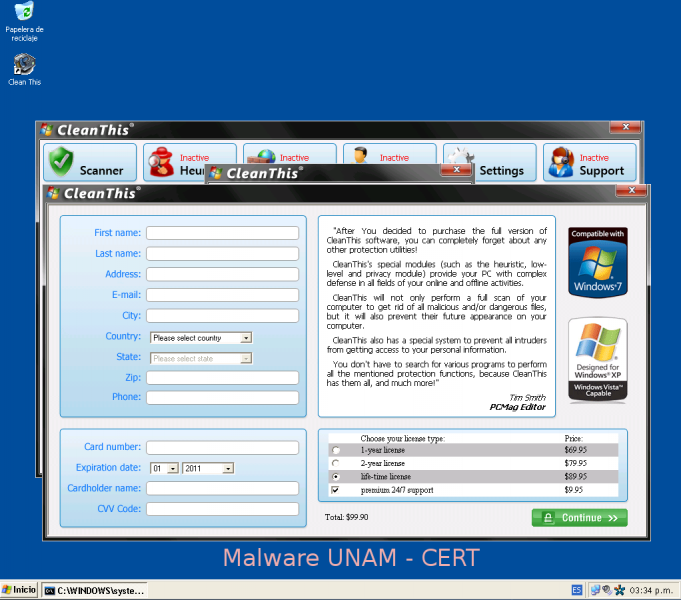
We completed the form several times, with fictitious information and it only showed messages that the requested operation could not be completed.
The behavior analysis showed that the sample downloaded more files than just the Word document, such as gog.exe and aspimgr.exe.
C:/DocumentsandSettings/<usuario>/Datosdeprograma/gog.exe
C:/WINDOWS/system32/aspimgr.exe
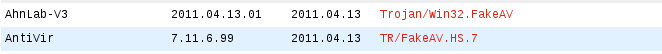
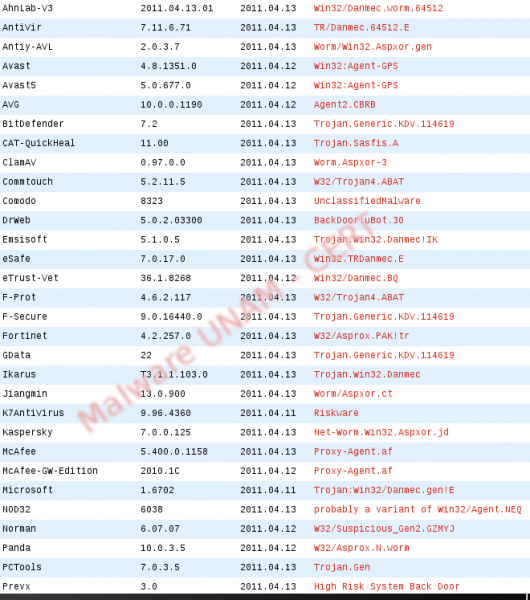
At the moment, the following antivirus engines detect it as a threat.
gog.exe

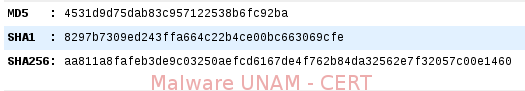
Its hashes are the following:

aspimgr.exe

Its hashes are also shown, as follows:
The gog.exe executable, is responsible for the execution of the fake antivirus tool CleanThis. Besides, the aspimgr.exe is responsible for the massive sending of the email shown at the beginning of this work.
The following pictures show the email message and the attached zip file, which the compromised computer was sending repeatedly, they were obtained from the sample's network traffic analysis, generated by the sample.
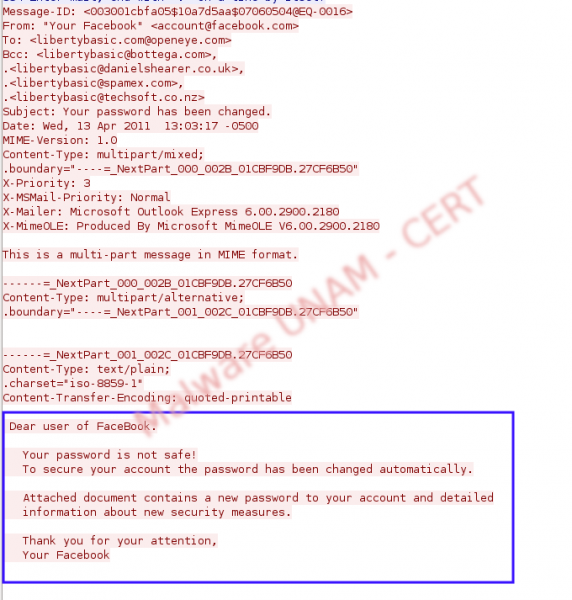

It was also possible to see, the performed connections after sending the email to multiple domains:
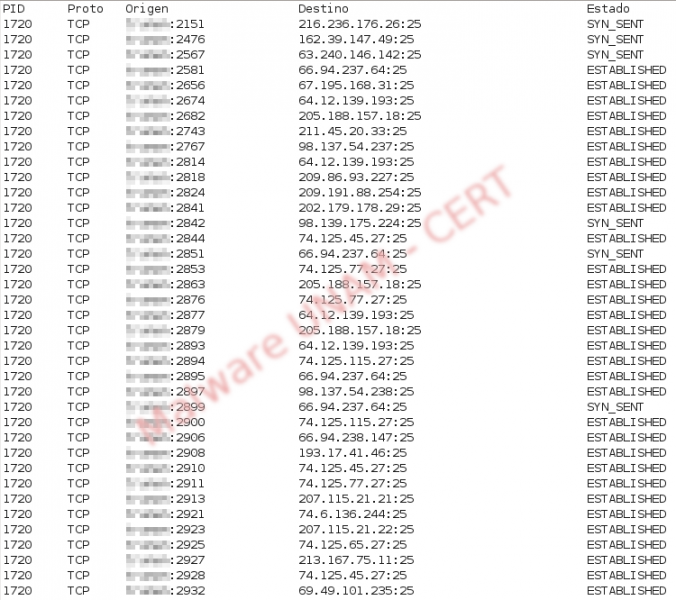
The supplanted accounts, in other words, from where were sent the emails, are shown in the following picture and the number in parentheses represents the amount of sent files from each account:
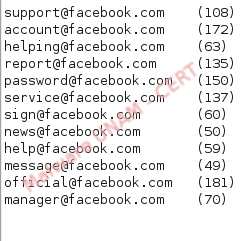
Moreover, the user email names to which were sent the malicious emails, start with the word liberty, then a string and the domain. The main affected domains were gmail with approximately 49 emails, yahoo with 153 emails and hotmail with 55. It could be counted 572 approximately, which were sent in five minutes during the analysis with an automatized tool.

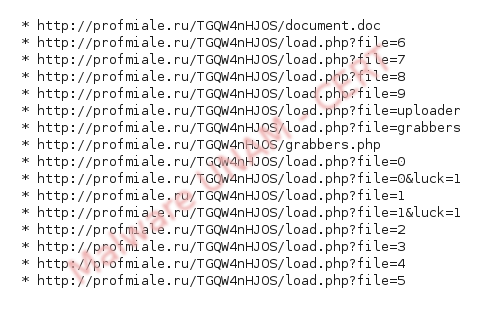
Besides, we detect the following URLs, from where are downloaded the malicious executable.
Finally, we found out that the form, is actually taken from the following URL:
http://212.XXX.XXX.149/pop/02/index_new.php?id=abs_03 y actualmente está activo.
For better or worse, social networks are changing the way people relate and communicate and through these fulfill the necessity of being in contact with others. The malicious code creators are taking advantage of this situation to affect a great audience and to obtain a benefit, specially commercial.
The most important to consider when are received this kind of email, is that a company as Facebook, first ,would never reset a user account and second, would never send it in an attached compressed file.
Another issue to consider, is that before downloading any file of this kind, you must verify that your account access, from any site, not only Facebook, has not been blocked, using the sign in information that you know. If for some reason, you cannot enter into your account, or you forgot your password, use the implemented procedures in the official sites to recover your password.