DroidKungFu and the exploits RageAgainstTheCage and Exploid for Android
Summary
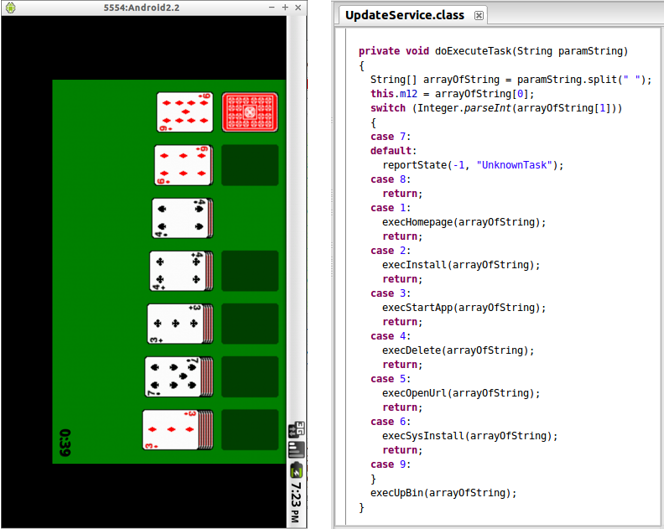
The analyzed sample is a trojan that pretends to be an application to play Solitaire while doing other background activities without the user’s consent, such as exploiting vulnerabilities and installing additional applications or unwanted advertisements (adware). This trojan belongs to the DroidKungFu malware family, detected on 2011 and that started affecting applications in China. The DroidKungFu variants have two important characteristics: they use exploits to escalate privileges (known as RageAgainstTheCage and Exploid) and these are ciphered with AES. Its main actions are: collecting information about the device to send it to remote servers, exploiting vulnerabilities to root the device, install other applications and receive instructions of its C&C (although this functionality could not be researched because the domains were down).
The banking trojan Banload and its techniques to evade security software
Abstract
Out of all the samples received during the last few weeks, the Visual Basic scripts (.vbs or .vbe) are the ones who caught our attention. In this report, we analyze a Visual Basic file that was coded with a legitimate Windows program to hinder its analysis. The analyzed sample is the first infection stage and its purpose is to download and, in some cases, assure persistence of additional modules or updates of the trojan; in addition to uninstalling the security software used in the computer (such as antivirus or banking plugins) and creating firewall rules to block the network traffic related to such executables in case the uninstall fails.
A glimpse to the phishing and malware situation in Mexico (April – June)
Abstract
As mentioned on the first statistics report of phishing and malware, it is important to show the most common cases to alert users and reduce the number of people affected.
During this trimester, some of the most interesting phishing campaigns were related to the Mexican Service Tax Administration (Servicio de Administración Tributaria, SAT) and with .cab files sent as attachments. There was also an increase in the amount of fake Banamex emails and the appearance of fake emails of Banorte, Netflix, WhatsApp and CFE (Federal Electricity Commission in Mexico), which were not observed during the first statistics report. Another notable characteristic is that phishing campaigns have opted to include two links, one for users and one for enterprises, and each redirects to different phishing sites. As for malware, the most common type is the malicious Word document.

Steam, platform for videogames, target of phishing and malware
Abstract
During the last few months, users of the popular videogames distribution platform called Steam have been affected by several fake login websites and chat messages with links that redirect to malware downloads which, after executed, steal the file that allow attackers to access the account without having the login credentials.
Malware for Windows detected in iPhone backup file
Abstract
Malicious programs can get to our devices in many ways; one of them is through the backup files of our mobile devices. And even though they do not present a threat due to its location and format, it is important to know why and how it happens. On this report, we analyze a backup up file of an iPhone 4S with iOS 8.2, that was detected as a threat by Microsoft Security essentials. The version of iTunes used to create the backup was the 12.1.1.4. The file detected was a malicious Word document sent to the user through email.
Cameron Diaz's sister, spreads fake AV through pictures
At the end of 2010, the security company McAfee published a list (see article) about the most dangerous celebrity names to search on the web. In first place was Cameron Diaz because the provided results by popular engines search, of pictures, screensavers and some common notes related to the actress, conduct to malicious code spreading, mainly, a fake antivirus that alerts users of supposed threats in their computer.

SPAM email: Your new Facebook password
At the start of the week, we received a notification about a spam email that is being spread in a startling manner that even so far, we got some of those emails, which have an attached file, called New_Password_IN75652.zip.
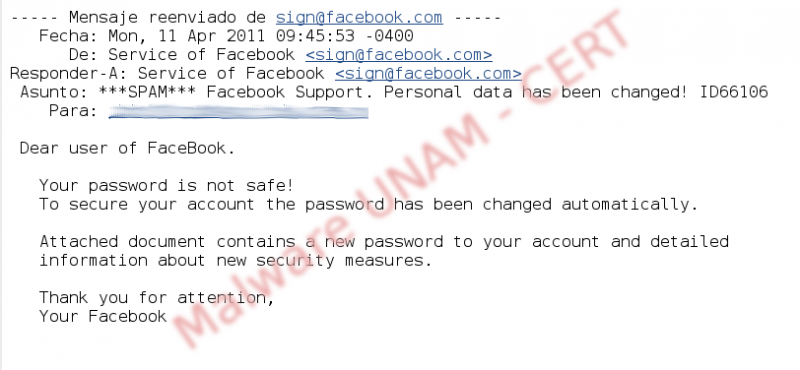
In the picture above, it is shown the email message, which notifies that the receiver's Facebook account has been changed and inside the compressed file, is the new password.
Malicious emails invite users to download malware
In these days, it has been spread an alleged email from SAT (Servicio de Administración Tributaria), which, through tricks, invites users to download a file where there are instructions to not being sanctioned for the supposed anomalies in the business tax situation.
It was commented that this email was only sent to small Mexican companies.

ZeuS, analysis of configuration file that attacked banking on Internet
Some days ago was spread a malware on the Internet, this malware belongs to the wide botnet family created with Zeus toolkit.
Zeus toolkit is a software that allows to any user with basic computer knowledge to create a group of zombies computers to carry out massive attacks, steal accounts of social networks, steal email accounts and in this case to steal users information from electronic banking. This toolkit is known as crimeware and is offered in underground forums and even by email at affordable prices.
SPAM email with message "POST Express Report " propagates malware
Recently, UNAM-CERT have received notifications about SPAM emails with the message POST Express Report, whose text is in English and informs to the user that a package was not sent to the address, for that reason the attached file contains instructions to recover the package mentioned above.
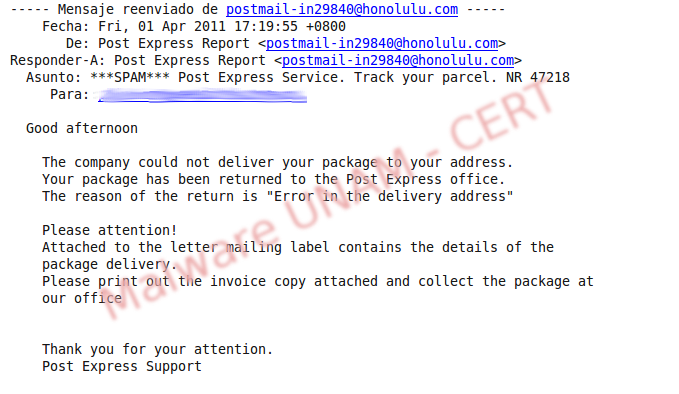
The attached file is in zip format, once decompressed, it creates the directory Invoice_Copy and then the Invoice_Copy.exe file, which is displayed with a Microsoft Word icon.