Bots that use Messenger and Facebook for their spreading
Yesterday we received a notification about a malicious link, which is spread on Messenger. This link pretends that the victim clicks on it to see an alleged image from Facebook, also, at the end of the link appears the receiver's email.
The first that oneself should do to verify the link's authenticity, is ask to whom allegedly sent it, if he really did it. In case that he has unintentionally made it (generally he does not know that he is spreading these links), we must tell him that he is probably infected with some malicious code and he needs to scan his system to identify and remove the threat.
However, we do not always have an answer immediately, so it is necessary to check the link before thinking even, clicking on it. When a friend wants we see a photo that is a real photo, the link is very different compared with the showed in the picture: It does not contain apps.facebook.com, not even, an email at the end of this one. These links are very similar to the shown as follows:
http://www.facebook.com/photo.php?fbid=170627117759934&set=a.12909460056...
This link contains the main Facebook domain, followed by a PHP file called photo.php or it also could be album.php followed by some parameters used to identify the photo owner and an identifier for the photo at issue.
On February 18th we posted a report about how developed applications using the Facebook API can be used to steal personal user information, on this occasion, we could see how these applications can be created to spread malware through of the social network.
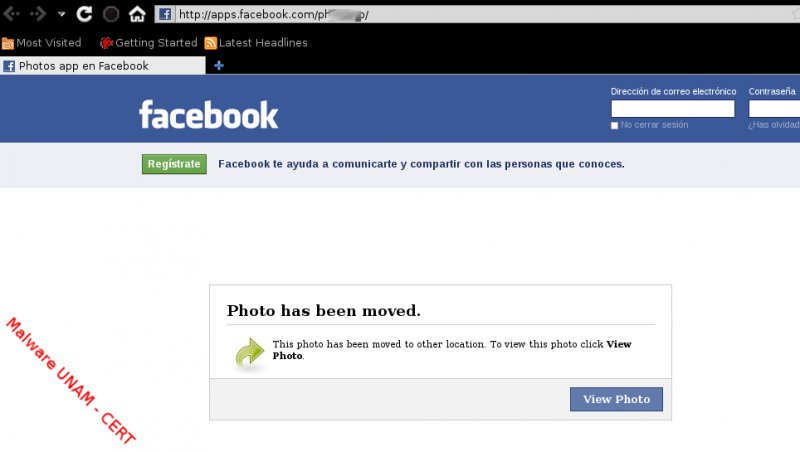
We copy the link on the web browser, omitting the email part and we were redirected to a page which shows a message where is mentioned that the image has been moved and automatically displays a window to save the executable photo_345349224.exe.
At the time of being analyzed the sample by different antivirus engines, only three detected it as a threat:

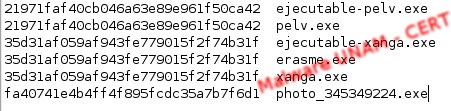
Its hashes are the following:

After executing the sample, were created in C:\WINDOWS, After executing the sample, were created in xanga.exe y pelv.exe, which were responsible for starting two processes with the same name.
These files were downloaded from the web servers img101.XXXX.com y img103.YYYY.com,respectively.
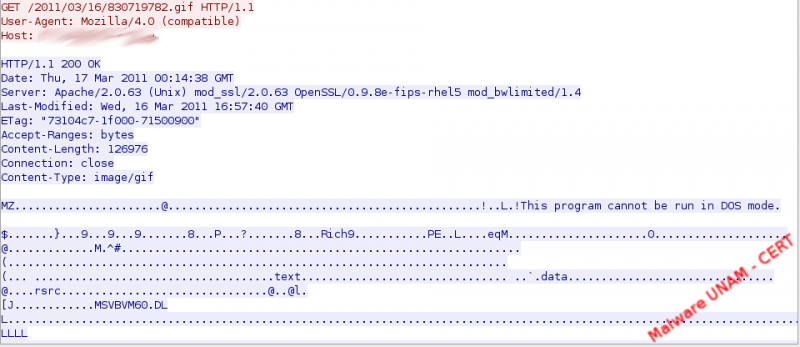
The xanga process was responsible for establishing a connection to the IRC server 46.XXX.XXX.42:6567
It can be seen in the IRC conversation a warning to all those who try to enter the IRC server without authorization, in addition to the download of eraseme_84424.exe file, which has the same MD5 hash xanga.exe than the executable.

Then, the MD5 hash of the downloaded executable are shown. The files ejecutable-pelv and ejecutable-xanga, we obtained them from the traffic capture.