Dynamic analysis of malicious DLLs
Inthis blog entry, the malware analysis team of UNAM-CERT will show a way to analyze a DLL file using already known tools and some specially developed by us.
ADLL or Dynamic Link Library is a file that contains blocks of code (functions or methods) that are run by request of a program. Is at this moment when it is loaded in memory.
Different programscan simultaneously use a DLL due to its modular scheme. Therefore, uninstalling a program could affect other applications that make use of shared libraries.

The DLLused for this analysis was created as a proof of concept (PoC) with some common malicious actions. On the image below we show that the file "malicious.dll" actually corresponds to a dynamic link library using the "file" command for Windows.

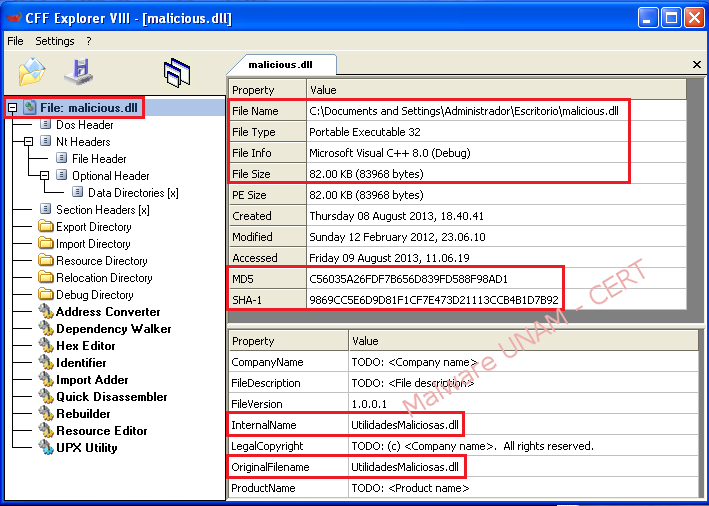
With the"CFF Explorer" tool you can get important information such as: the programming language with which the file was created, its size in bytes, its md5/sha1 signatures, the original file name, among other characteristics.
For the file "malicious.dll" the following information is displayed:
It is recommended to carry out a string analysis to malicious DLLs, as it is done with suspicious executable files, in order to obtain more information. In this case, using "BinText" it can be observed that it calls for the Windows command line interface with the argument "C:\WINDOWS\system32\calc.exe", which is an indication that the DLL contains code to run the binary of the calculator.

When disassemblingthe DLL with "IDA Pro", it can be confirmed that, once injected into a process, "calc.exe" is executed. The system call "ShellExecuteA" performs an operation on a specific file, in this case it opens the Windows calculator.

Unlikeexecutable programs, you cannot double-click the DLL files to execute them, since they are not an autonomous entity, hence, they require a process to operate. The Windows operating systems include a utility called "rundll32.exe" (32 bit version) to run DLL files. However, the malicious actions will be attributed to the process "rundll32.exe"; so if "ProcessMonitor" is used to monitor the actions of the malicious DLL, the filter name of the process should be for "rundll32.exe".
Theprocess tree is shown below:

Also,there may be a problem to run a DLL with the "rundll32.exe" command if the dynamic link library validates the process in which it must be injected. One solution would be to rename the tool "rundll32.exe" with the name of the target process, which would imply a more thorough inspection in the assembly code.
Also,there may be a problem to run a DLL with the "rundll32.exe" command if the dynamic link library validates the process in which it must be injected. One solution would be to rename the tool "rundll32.exe" with the name of the target process, which would imply a more thorough inspection in the assembly code.
- DLL_Injector: GUI tool to inject one or more DLLs into a process.

- DLL_Shot: GUItool to identify active DLLs injected into the malware process and into another objective processes. This is done by comparing the active dynamic link libraries in the system before and after the execution of the malware or DLLs injection.

To examine theDLLs, we started the following monitoring tools: "Process Explorer", "TCPView", "Regshot", "DLL_Injector" and "DLL_Shot".

1) Execute the program in which the malicious DLL will be injected, for example the “Notepad”.

2) List the system processes. On the tool “DLL_Injector”, with the “List” button, we select the objective process.

3) Search for the malicious DLL with the “Browse” button.

4) We take the first shot using both “Regshot” and “DLL_Shot”

5) Inject the DLL into the objective process with the button “Inject”.

6) Observe the process activity.

7) Observe the network activity.

8) Take the second shot of the tools from step 4.

9) Compare results.

10) Analyze results.
- In step 6, the process activity shows that from the trojanized process "notepad.exe", the process “calc.exe” gets started.
- In step 7, the Trojanized process opens the local port 50500 in listening mode, which is an indication of a backdoor.
- In step 9, the activity in the file system was the creation of a folder and a file with a "txt" extension. As for the DLLs, it can be seen that the file "malicious.dll" was correctly injected into the process "notepad.exe". The DLL "netcfgx.dll" loaded by the process "svchost.exe" is also shown, and it has the description “Network Configuration Objects“, which involves network protocols and is shared by several Windows applications.
Finally, a way to check if the local port 50500, which was opened in listening mode, has an associated shell is by using the "telnet" command from another computer. On the image below, the obtained Windows “cmd” can be seen:

It established a network connectionto port 50500 from a Linux computer and another instance of the trojanized process remained in listening mode:
