Fake email of Gusanito postals spreads botnets
It was reported to UNAM – CERT about an alleged malware which spread by means of an alleged email from Gusanito and it suggests to the victim to click on a link to see a postal.

The email is an image containing a link which redirects to the site xxxxxx.com/images/Ver.php, the image is taken there in the url xxxxx.com/dreams/Postales/gus.jpg.
The .php file redirects to another site where is actually stored the malicious code (http://rutasxxxalma.com/Postal.exe).
The malware has the following hashes:
MD5 : f99e446f66b156e2f30eb1271513214d
SHA1 : 51f3de71840bc730f08587b58fd01bf028557cdd
The malicious code tried to execute in a Windows XP lab, which displays the following error and neither executes nor performs any modification.
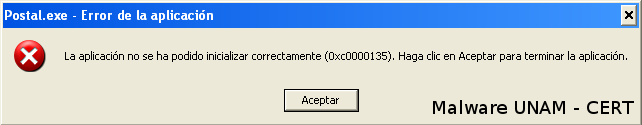
It was then when we decided to execute the malware in a Windows 7 lab. Where it was possible its execution.
When executed, it creates the files:
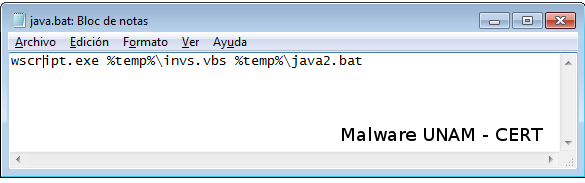
\AppData\Local\Temp\java2.bat
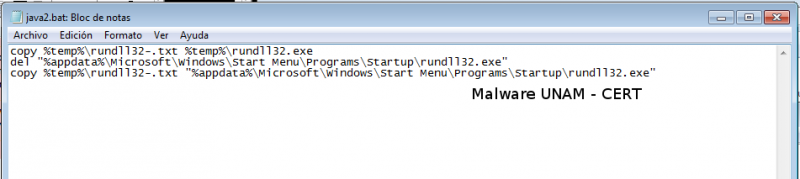
\AppData\Local\Temp\rundll32-.txt
\AppData\Local\Temp\invs.vbs
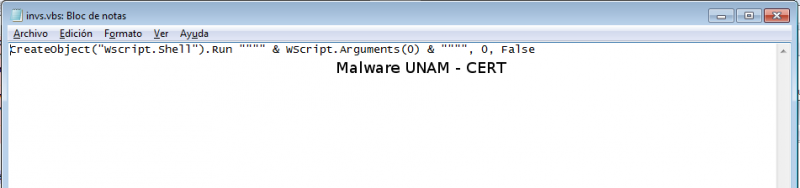
\AppData\Local\Temp\java.bat
Later the malware adds the following registry key, HKCU\Software\Microsoft\Windows\CurrentVersion\Run\rundll32 and deletes the next one: DeleteValueKey C:\Windows\System32\taskhost.exe -> HKCU\Software\Microsoft\Windows\CurrentVersion\Run\internat.exe.
In order to execute the Windows console “cmd”, at that moment, executes the wscript \AppData\Local\Temp\invs.vbs, which opens the Visual Basic Script file copied previously.
Once done, it opens the file AppData\Local\Temp\svhost.exe, a trojanized process which continues running in memory
Then execute the file \AppData\Local\Temp\java2.bat, the objective of this bat file is to rename the file \AppData\Local\Temp\rundll32-.txt in \AppData\Local\Temp\rundll32.exe, then deletes the file "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup\rundll32.exe" to copy its own file
Later it deletes the created files and leaves the trojanized svhost.exe process running.
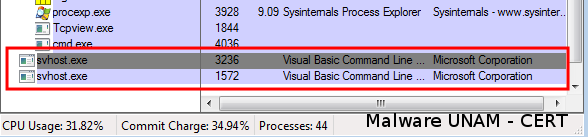
And this process starts requesting connections to an external site.
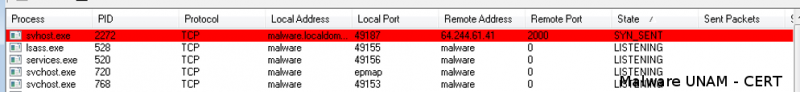
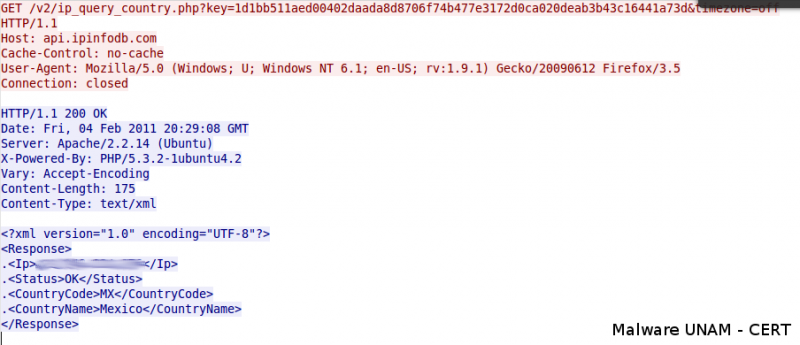
Moreover, it starts requesting an external http site.
The other new connections request the IP address 64.244.61.41, which starts sending packages on the TCP protocol to a cisco server.
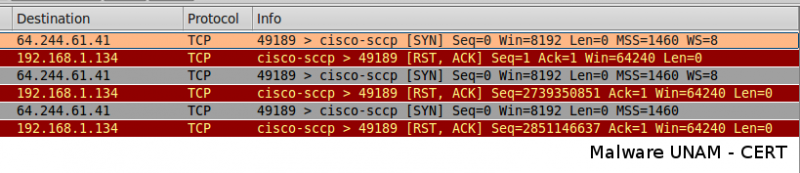
This service is used as a tool in VoIP.
This sample was obtained in February 4th, to the present day February 8th, 2010, only four antivirus engines recognize it as malicious.