Malware for Windows detected in iPhone backup file
Abstract
Malicious programs can get to our devices in many ways; one of them is through the backup files of our mobile devices. And even though they do not present a threat due to its location and format, it is important to know why and how it happens. On this report, we analyze a backup up file of an iPhone 4S with iOS 8.2, that was detected as a threat by Microsoft Security essentials. The version of iTunes used to create the backup was the 12.1.1.4. The file detected was a malicious Word document sent to the user through email.
Introduction
For malware analysts is common to find malicious Office documents that come as attachments in emails that pretend to be from a known organization or entity. What is unusual is to find a malicious Word document inside the backup directory of the iPhone. On this report, this case is addressed.
During a routine scan with Microsoft Security Essentials, protection tool against malicious software in Windows, the warning message, seen on the image below, opened. It indicated that a “possible threat” was found in the file 3a2732841c1297cbcfa59f941e0f286f5b4213e5 inside the directory C:\Users\<usuario>\AppData\Roaming\Apple Computer\MobileSync\Backup\.
This file was extracted from the computer and its analysis is detailed below.
Structure of an iPhone backup
When the iPhone synchronizes with a computer, most of its information is backed up inside a folder created by iTunes. Its name is made up of 40 alphanumeric characters and is known as Unique Device ID or UDID.
The first time the iPhone is synchronized with a PC, iTunes makes a full back up of the device, in such way that in further backups only the modified files are overwritten. The backup files are independent of the operating system.
The paths where iTunes makes the backups, according to the Windows version, are shown on the table below:
| Windows Version | Backup Path |
| Windows XP |
C:\Documents and Settings\ |
| Windows 7 |
C:\Users\ |
| Windows 8 |
C:\Users\ |
The backup folder contains several files with names of 40 alphanumeric characters and without extensions; each name is the SHA1 hash of the file’s path in the device, in such way that the full name works as a unique identifier of a data set.
The paths of the files have the following structure:
On the image bellow, the file selected corresponds to the one where Safari cookies are stored (this can be tested using fileformat.info):
HomeDomain-Library/Cookies = 18174053c0de10175f974ef86bddbfcf4218513f
The domain, which in this case is “HomeDomain”, contains several directories, as shown on the following image.
The “Library” directory contains data of the applications installed by default in iOS, such as: contact information, email accounts, SMS, calls history, websites access through Safari, etc.
These data can be seen with applications such iPhone Analyzer. An example of this is shown on the next image, where the cookies of the websites that the user visited on the Safari browser can be seen by opening the file Library/Cookies.binarycookies_tmp_1924_0.dat .
Manifest Files
Inside the backup directory you can find the files Manifest.mbdb and Manisfest.plist (although in other iTunes versions the Manifest.list is replaced with Manifest.mbdx). The file Manifest.pslit contains a list of the applications on the device. Manifest.mbdb and Manifest.mbdx are files that work as the iPhone’s database and contain registers of the files that must be backed up.
Analysis of the file
As shown on the image of the introduction, the file was detected as “TrojanDownloader:W97M/Adnel”. ”. According to this Threatpost report, the threats that make use of macros to download malware had a drastic increase at the beginning of the year and Adnel was one of the most detected variants.
This means the backup file most likely contains a malicious Microsoft Office document. A way of testing this is by looking for known strings in it. As mentioned in this and this report, malicious Office files need the user to enable the macros to download malicious code from remote servers; this means the file must contain the string“Macros”. As show on the image below, the backup file contains several strings related with macros, similar to the ones normally found in malicious documents.
Another common string is the one that references the URL from which the malicious sample will be downloaded. The most common name is “ss.exe” although sometimes it varies and is called, for example, calc.exe. At the time of analysis this domain had already been shutted down, so it was not possible to download the sample.
Now we know the backup file does contain a malicious Word document. To obtain it, Scalpel, could be used, which is an open source tool that recovers files by using certain hexadecimal characters located and the beginning (header) and at the end (footer) and that are common to each file type.
The command used and its result are shown on the following image. The first parameter is the name of the backup file. The second, with “-o”, specifies an empty directory where Scalpel will store the obtained files.
The file audit.txt shows a summary of the actions carried out by Scalpel. In this case, it indicates that the file 00000000.doc was extracted; however, the “Chop” column indicates the file was not “cut”.
Scalpel looks for a "footer" or indicator of the end of file, if it is found before the maximum size is reached, the new file is “cut” or “extracted” and this is why there’s usually a “Yes” in the “Chop” column of audit.txt. In this case, what happens is that the tool did not extract a part of the file but the whole backup file was the Word document.
As it can be observed, the size of both files is basically the same. This means the iOS stored the attached file of the malicious email in the device and iTunes backed it up in the computer without modifications but without extension.
In fact, the first hexadecimal characters of the infected backup file match magic number of Microsoft’s OLE files (Object Linking and Embedding), which is the format used by Office 97-2003 applications (Word, Power Point, Excel, …).
So if the “doc” extension is added to the file, it will open without problems on a Windows system with Microsoft Office installed.
Getting the phishing email address
Using the iPhone Analyzer tool it is possibly to examine the “Mail” directory, which contains the files AutoFetchEnabled, MailboxCollections.plist and Recents. After analyzing the file Recents on the hex editor of the application, some email addresses were observed.
The one that caught our attention was subdirsuc0409@santander.com.mx, since official Santander website declares that the only domain used by the institution to communicate with its clients is informa.santander.mx. In addition, the affected user confirmed he didn’t have a bank account in Santander. Therefore, it is possible that the phishing email, with a malicious Word document attached, was sent from this address.
Why was the malicious Word document backed up?
Despite knowing how the malicious document got to the mobile, it hasn’t been explained why it was saved on the computer. The file was not stored on the iPhone because of the “Mail” application, but because of the “Documents To Go” or “DocsToGo” application that was installed on the device.
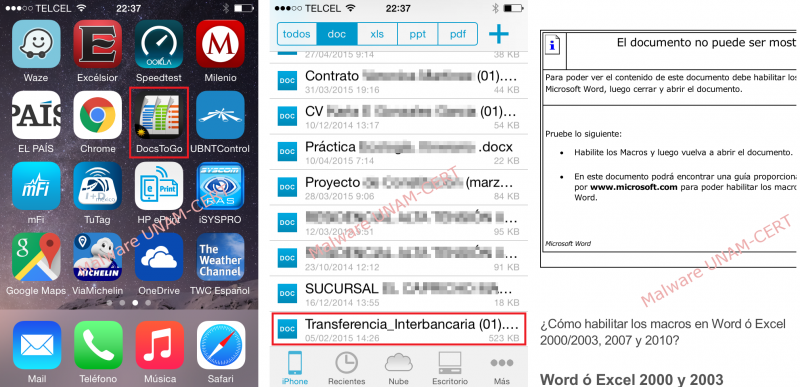
After checking the documents managed by the application, one called “Transferencia_Interbancaria (01).doc” (Spanish for Interbank Transfer) was found. When opened, the common format for malicious Word documents was observed, where the user gets asked to enable macros to see the content of the file.
Conclusion
Microsoft Security Essentials detected the backup file of the iPhone as malicious because it was in fact a Word document that iTunes saved in the computer without modifications. The only changes carried out during the backup process were: removing the extension and changing the name that the file had when it was sent through email for the SHA1 hash of the iPhone's path where it was stored.
Enlaces
To get more information about the iPhone’s structure and the forensic analysis carried out on its backup files, we recommend the following links:
· Ifans