Spam campaign propagates malware and compromises computers
On recent days, UNAM-CERT was notified about a spam campaign that attracted users and deceived them to download files and execute them on their computers.
We visited the mentioned website and carried out some queries, however, the alleged malicious files had gif extension. At first glance, they looked like harmless images.inofensivos.
The tool wget was used to download the files. This is the structure of the website’s directories:
Once the website’s files were in our analysis lab, we used the file command to verify if they were actually images. The result, in both cases (a2.gif and aa1.gif) was that they were executable files for Windows. Therefore, the extensions were changed, adding .exe at the end.
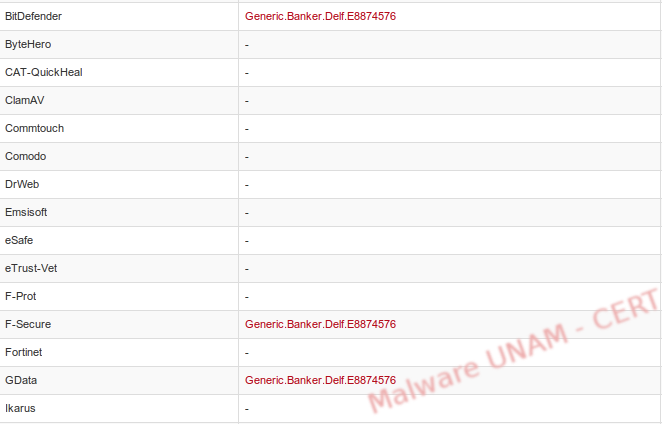
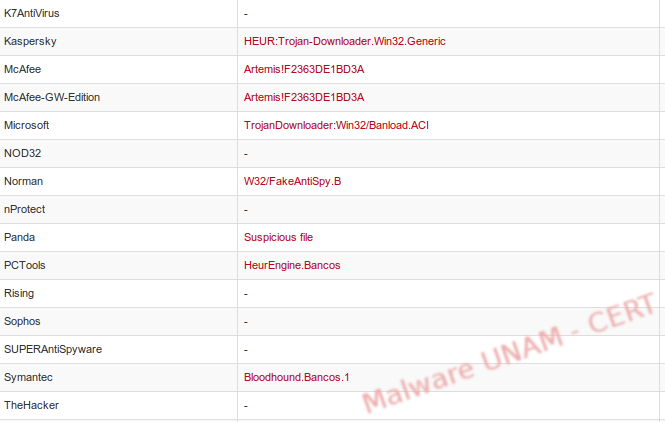
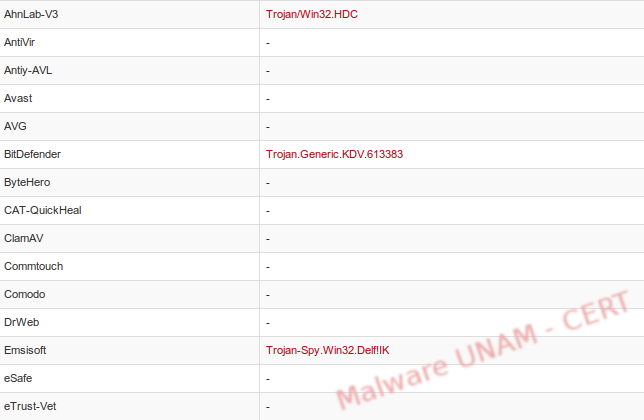
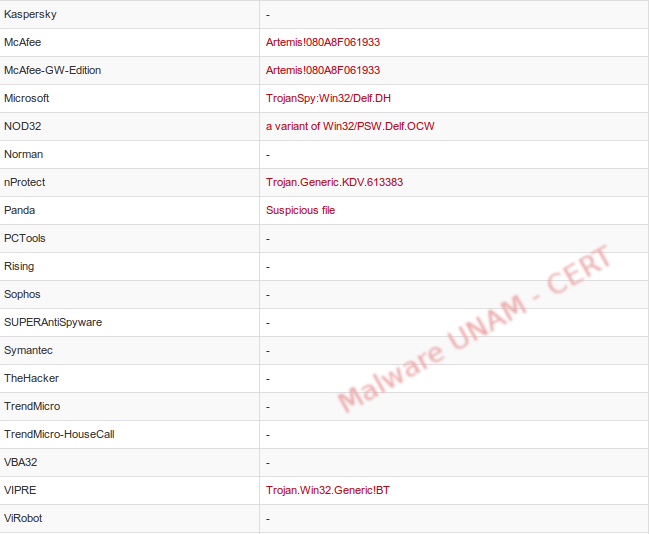
The VirusTotal website was used to analyze the samples. For the aa1.gif.exe only 11 antivirus engines detected it as malicious, classifying it, in general terms, as a Generic.Banker.
According to VirusTotal, the sample has also been received with the name xswindowsmsgs1111.exe, which made us think that it was propagating itself as software of Windows Messenger.
For the second sample, a2.gif.exe, 13 antivirus engines detected it as malicious; unlike the previous sample, this one was classified as a Trojan.
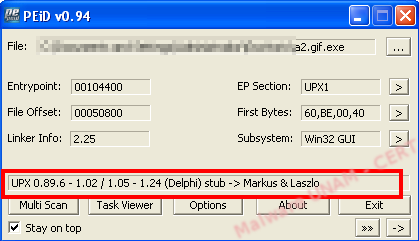
The first sample we analyzed was a2.gif.exe; according to VirusTotal, it was packed with UPX, which was confirmed with the PEiD tool.
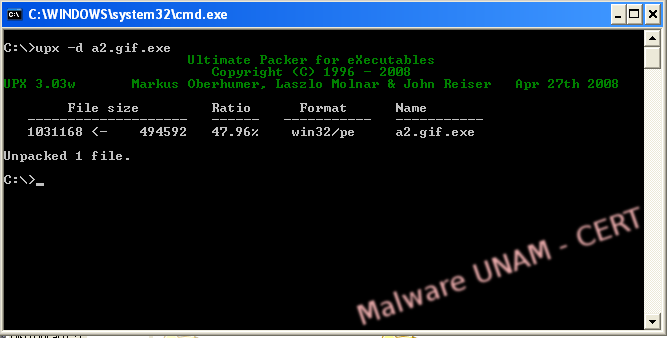
We named the unpacked file Unpack_a2.gif.exe and used the PEiD tool again; as can be seen, the file is no longer packed and it was possible to determine the programming language.
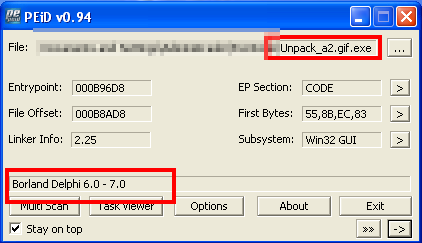
The only interesting thing we obtained from the string analysis was that the file contained modules referent to SSL and email, which could mean that the sample was used to massively send spam.
The strings “PASSWORD” and “USER_NAME” were found multiple times.
After gathering all this information about the sample a2.gif.exe, we proceeded to execute it in a controlled environment.
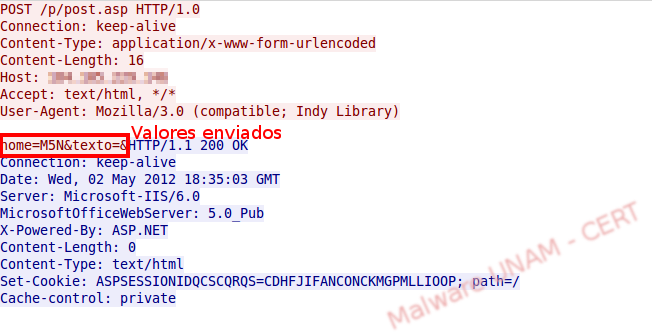
When the sample started, it sent a request towards a remote site, sent information and ended. It did absolutely nothing else. The remote site, to which the sample is connecting, is located in the United States. Among the data sent, there was a variable called “nome” with a value of “M5N” on the page /p/post.asp, just as shown on the image below.
As we mentioned previously, the process ends without leaving the computer infected and without any malicious demonstration.
The sample was executed again and the value of the variable “nome” is now sm7.
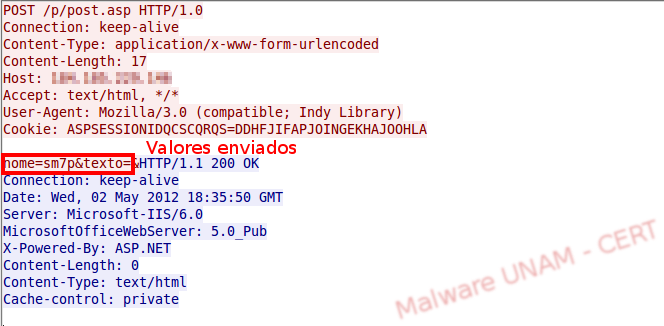
This made us think that the sample is part of a set of tools that the malware creator uses. Perhaps it receives instructions from another module. The additional module could be the sample aa1.gif.exe, therefore we proceeded to analyze it.
As the previous sample, the file was packed with UPX.
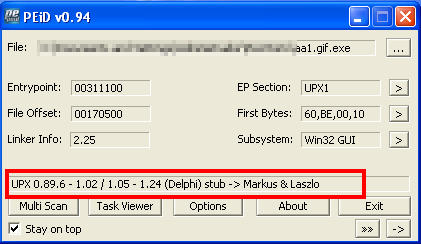
The sample was also unpacked with the UPX tool and called Unpack_aa1.gif.exe, after which the string analysis was carried out.
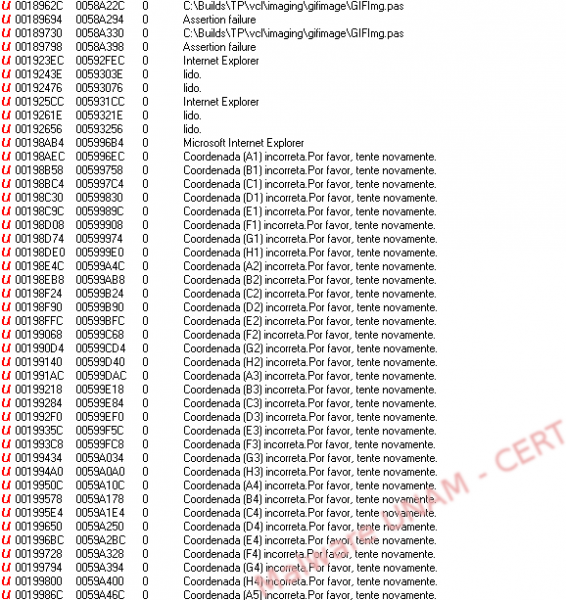
Amongst the strings we found many that were particularly interesting: several strings had the pattern “Coordenada (XX) incorrecta. Por favor, tente novamente.”, which translated in English could be something like “Coordinate (XX) is incorrect. Please try again”; that was possibly used to steal information from a coordinate’s card of some bank of a Portuguese speaking country.
The analysis of the second sample was done on a controlled environment. The process aa1.gif.exe was created immediately and started different connections to the same remote site as the previous sample, except it did consult other websites, as seen on the network traffic, where a new IP address appeared.
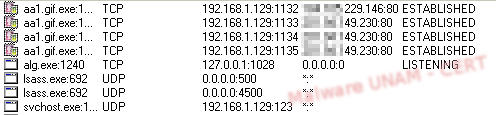
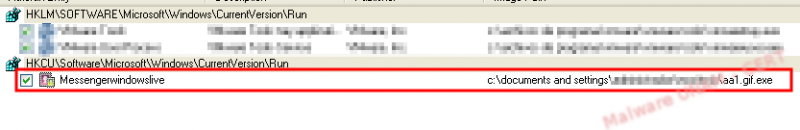
The process aa1.gif.exe continued with its execution during the entire analysis. It created a registry key called Messengerwindowslive that pointed to the location of the malicious executable. This key ensures its execution on every system startup.
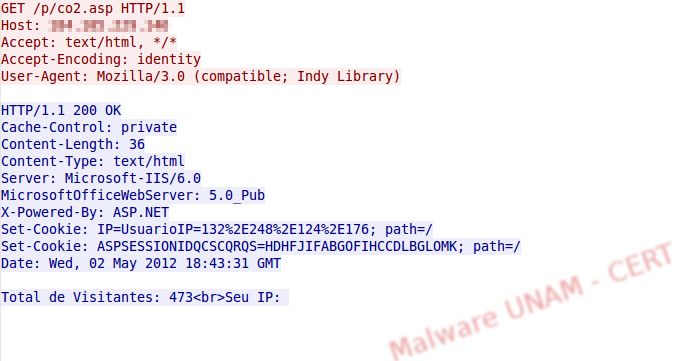
As for the information that it exchanged with the remote server, when we visited the site /p/co2.asp, it returned the message “Total de Visitantes: 473<br>Seu IP:” (Total visits: 473<br>Your IP:), possibly related to the amount of infections.
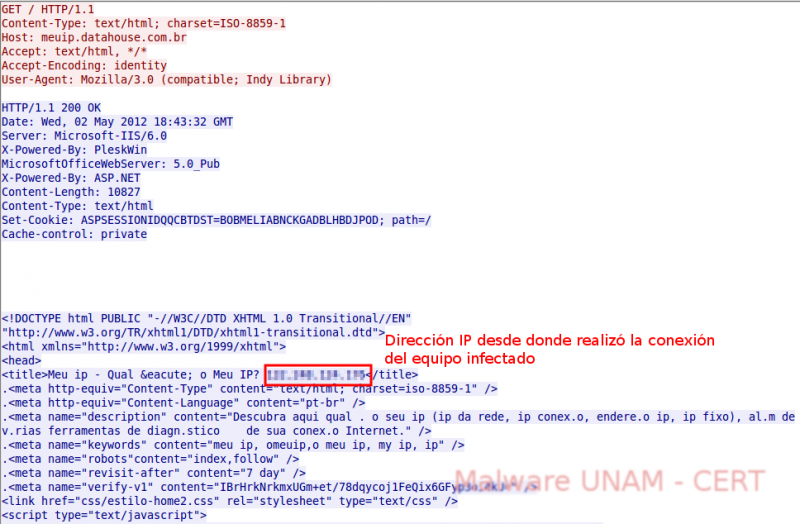
The new IP was resolved from the domain meuip.datahouse.com.br, which provides the geographical location of the infected computer from its IP address. We have seen this kind of behavior on previous samples. The purpose ofusing these services is to provide information about the geographical location of a particular computer, so that depending on the region, the criminals can send specific attacks.
The maliciousprocess kept itself running and during the time we were monitoring it, we observed that it continually made requests to the page /p/update2.txt, hosted on the compromised website. However, by the time of the analysis the page was not available, sending the message "The page cannot be found". Nonetheless, the malware author could upload the configuration file so that all infected computers begin to make some malicious activity, such as denial of service attacks, sending spam or any other action that the author had programmed.
.