Virus used to steal the navigation data from Internet Explorer
In this entry, we show the analysis of a virus that was captured in recent days. The objective of the virus was to steal the navigation data stored in the user’s infected computer. The sample is called 07102013.exe and its signatures are shown below:
MD5: f87231e93678130e635c0a6219e0a14a
SHA256: b87a2c53716970b2046a38cf7743e4c20484877aa68c0fc9b44bf8afbc9b1667
The string analysis allowed us to observe different functions of the Windows library used by the malware, such as: WriteFile, ReadFile and GetSystemTime; therefore, the creation of some kind of file was expected.
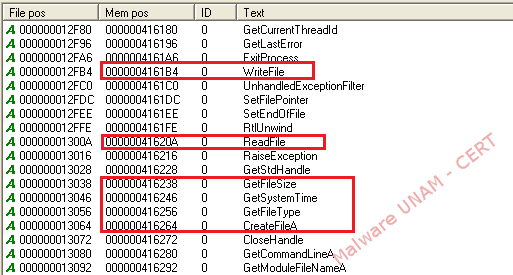
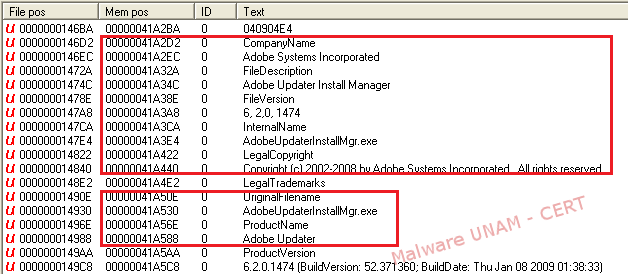
On the next image, the information related to the analyzed file, used to generate a new file on the infected computer, is shown in red. The malicious file uses names related to Adobe to be able to go unnoticed.
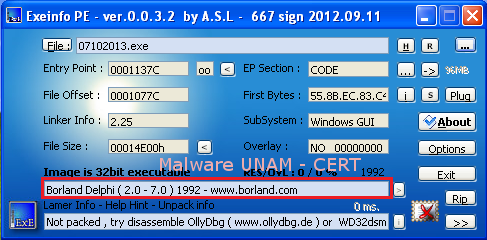
Using the tool called ExeInfo PE we could determine that the executable file was written in Borland Delphi.
Subsequently, the malicious file was executed, injecting itself into the legitimate processes svchost.exe.
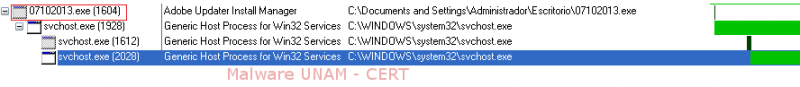
As a result, these processes are able to go unnoticed for the user; so even when using the tool Process Explorer, a malicious executable may appear with the description “Generic Host Process for Windows”.

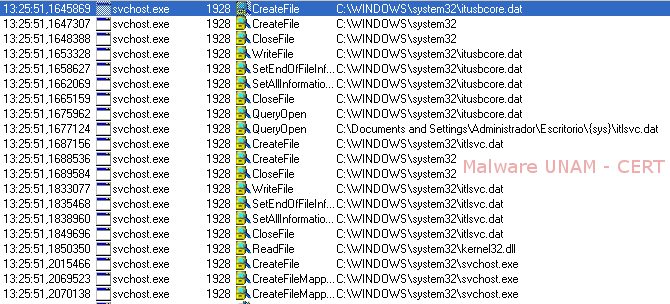
These processes generate two files, itlsvc.dat and itusbcore.dat, inside the directory with the path “C:\Windows\system32”. These files were downloaded via Internet, through the requests made by the sample, called 07102013.exe.
The log obtained with the tool Process Monitor, that shows the creation of the files mentioned before, can be seen on the image below.
On the next images, the GET requests captured in the network traffic,that perform the downloading of the malicious .dat files, are shown.
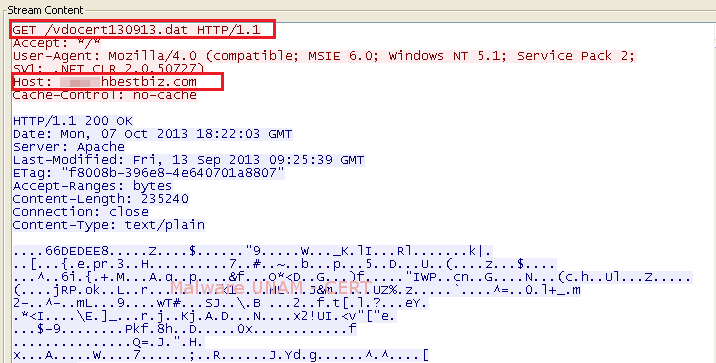
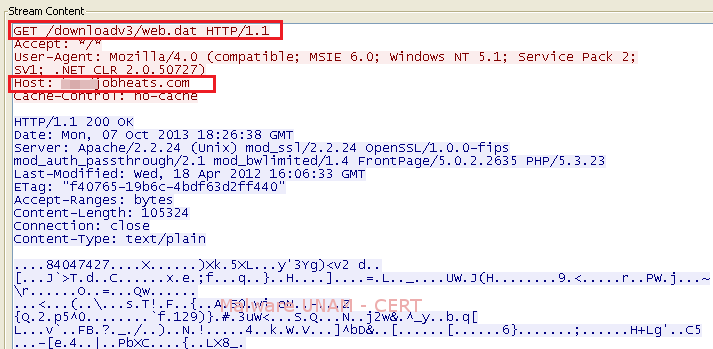
As for modifications in the file system, we observed the creation of the two .dat files mentioned above, of the AdobeUpdaterInstallMgr.exe whose name was found on the string analysis and of the adobbupd.dat which possibly uses the AdobeUpdater executable.

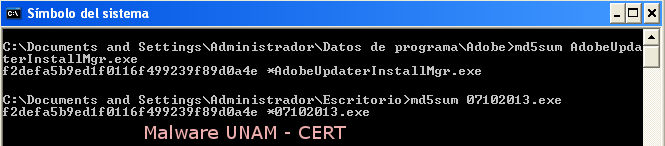
It is worth mentioning that the file AdobeUpdateInstallMgr.exe is a copy of 07102013.exe, the original file, given the fact that its MD5 hashes are the same.
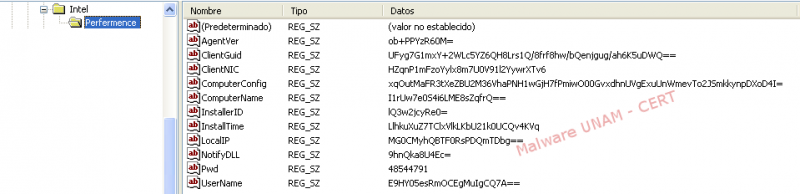
On the Windows registry, a key that apparently references the Intel software was added.

Using the tool regedit.exe we observed some values stored in the path of the specified key; apparently there is a routine in the malware that obfuscates this values.
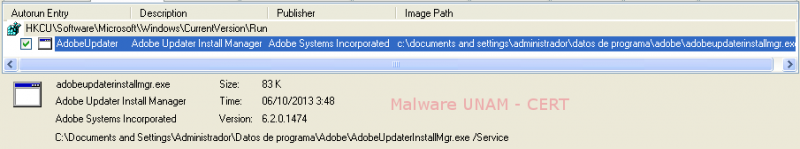
After this, the sample created a registry key to allow its execution at every startup.
While the malicious processes were active, every certain time they made requests with specific parameters to a malicious site to get some kind of code (shown in green on the image), probably an instruction that the malware was capable of execute.
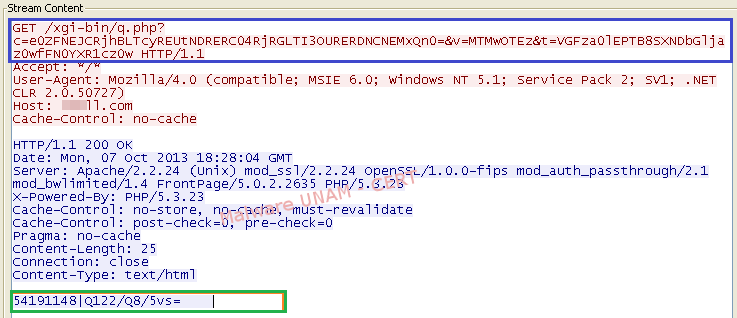
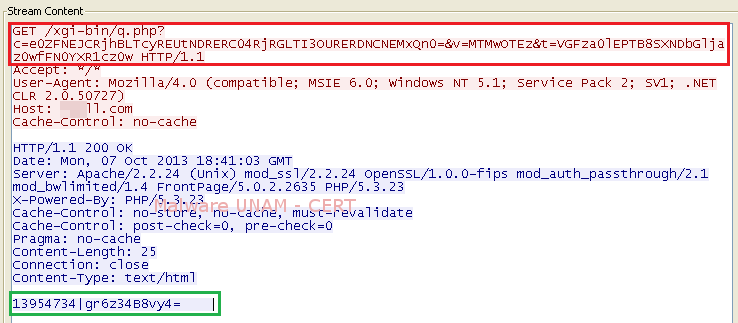
With the help of Process Monitor we were able to observe that, at the time these requests were made, the process svchost.exe was reading the file index.dat; which is a data file used by Internet Explorer to store information related to URLs, searches and files opened by the Windows Explorer.
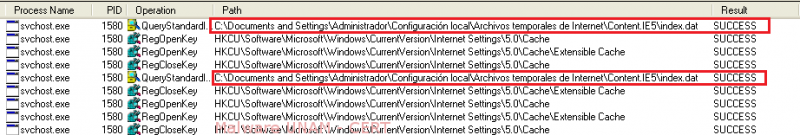
On an attempt to discover which kind of data could be collected by the malware, we used a forensic analysis tool for Windows called ‘index.dat’ Parser (id) on the website www.seguridad.unam.mx to generate any kind of registers that could be stored in the file index.dat.

Later, we used the tool id to extract the data from file index.dat, as shown on the next image.
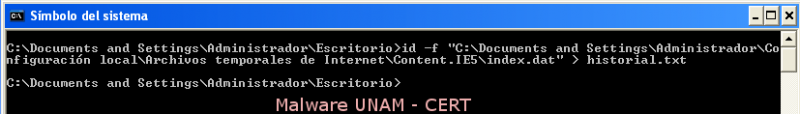
We opened the file “historial.txt” and found multiple references to the visited site, www.seguridad.unam.mx.

The MD5 signatures of the files used by the malware are these:
adodbupd.dat: 21d5b5ebeba05234d851d5b50ec711f5
itlsvc.dat: e0e604d1a90059a0324a492d0a82c0e4
itusbcore.dat: 6e5a014bedaa994beb8e05de8ab2ede6
The detection rate of the antivirus engines is shown below.
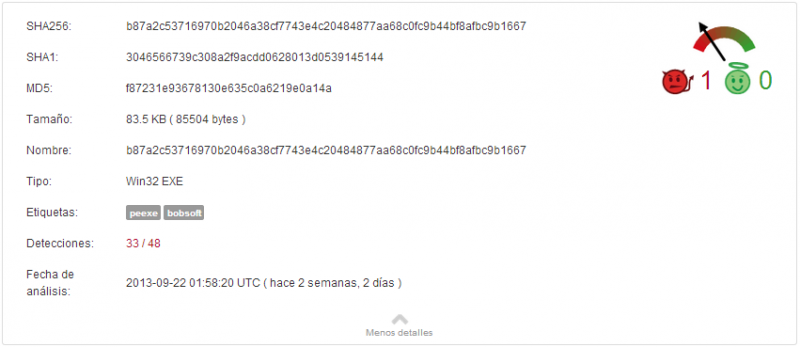
The complete report from VirusTotal can be consulted here: