Dorkbot variant download malware through an IRC C&C channel
In one previous post on this blog, it was performed the analysis of a malware sample that was spread on Skype, that sample was a Dorkbot variant. In recent days, several cases of infections performed by a computer worm were reported; therefore, the malware analysis team proceeded to conduct the inspection of the sample.
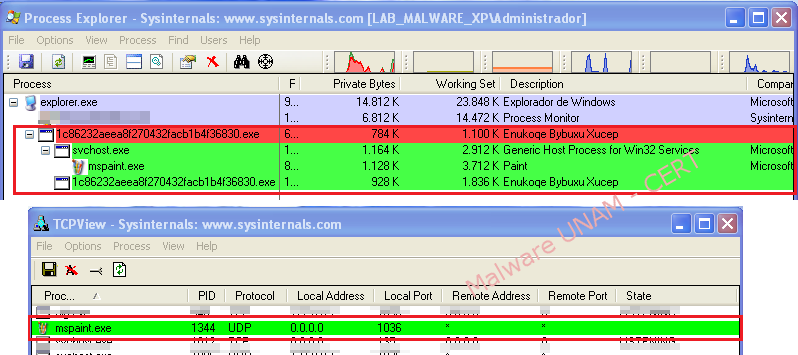
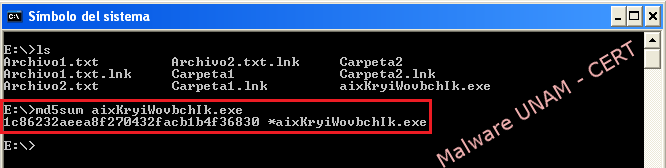
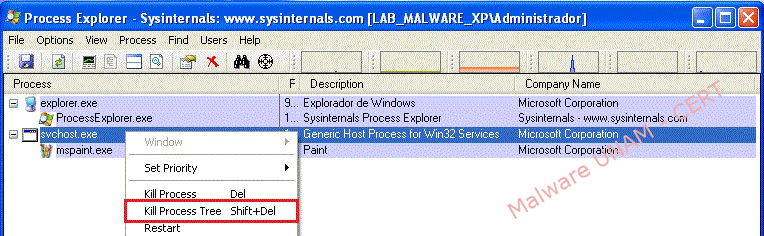
The file “1c86232aeea8f270432facb1b4f36830.exe” was executed in a controlled environment without Internet connection, the execution starts up the process “svchost.exe”, which in turn initiates the process “mspaint.exe”. This process is associated to Microsoft Windows “Paint” image editor, however, at no time such editor shows up.
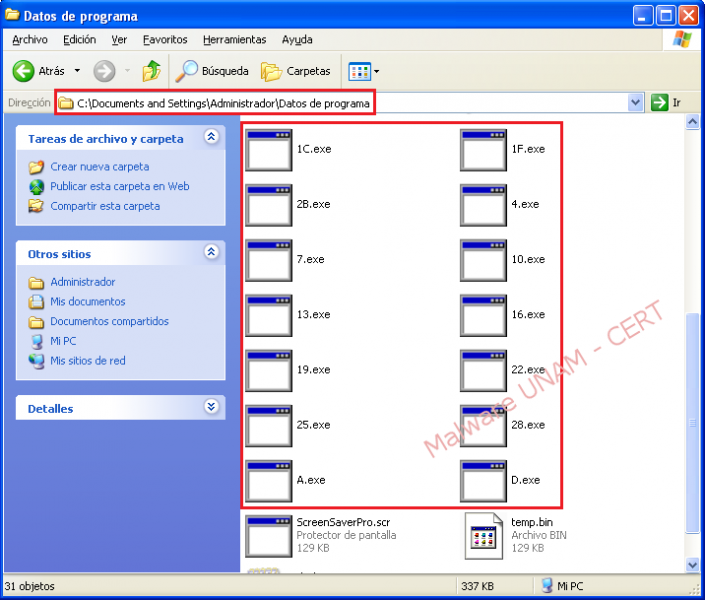
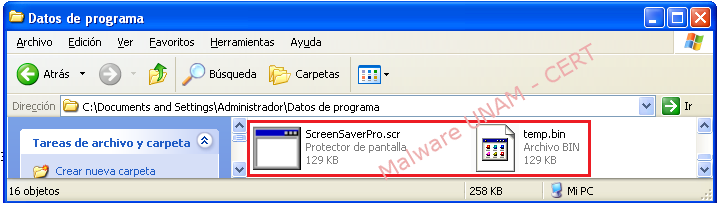
In the Windows Registry, it creates a key to keep running on every system startup. In the File system, it duplicates itself twice: “ScreenSaverPro.scr” and “temp.bin”. Finally it erases itself form where it was executed, in this case from the Windows “Desktop”.
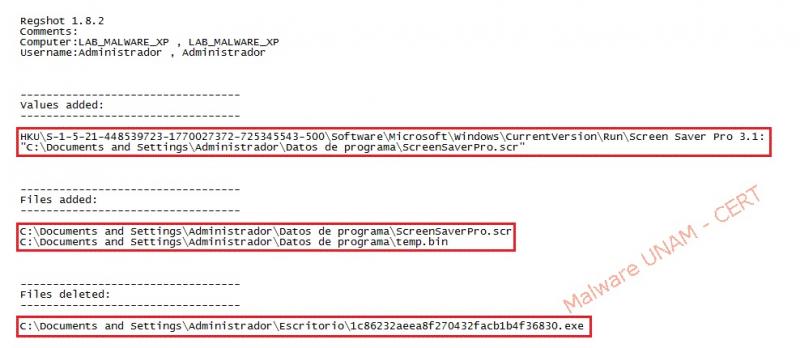
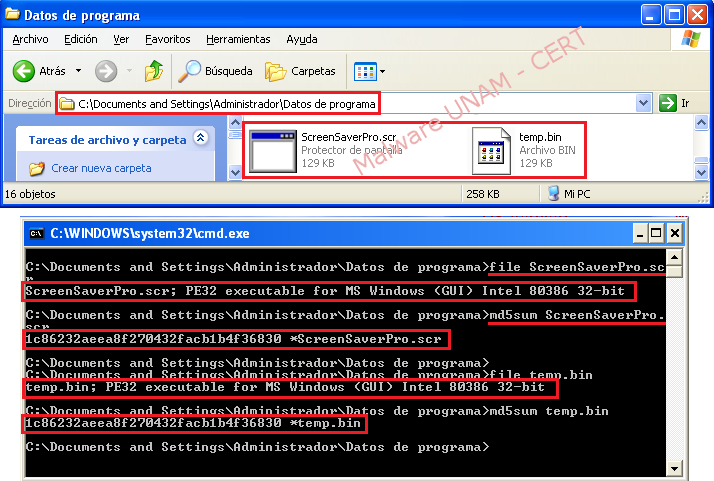
In the image below are shown the created files and its md5 firms:
Analyzing the files with the tools “PEiD” and “Exeinfo PE”, they throw different results. PEiD does not detect that the binary file is packed and ExeInfo PE does, detecting that the malware is packed with UPX.

This was corroborated performing a string analysis, where it was found that the strings were obfuscated, and also it was found evidence that the file was packed with UPX.

While unpacking the executable file, "upx" showed an error message saying that the file could't be unpackaged because of possible changes by the creator of the malware.
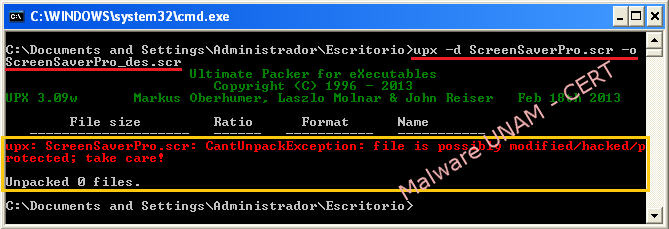
Without the unpacked executable file, a memory dump was performed in order to get the original process and also more useful information.
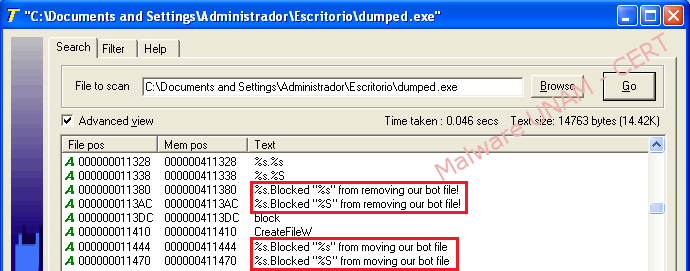
In early results were found keywords that helped determine that it was a "bot" associated with IRC service.

Subsequently, some connection attempts to various services on the Internet were found.

Below is a list of the domains to which the malware sends requests.

Also, it was found a number of configuration actions to be performed on USB devices.

In network traffic, the malicious process attempted to resolve four domains. Below are DNS queries.
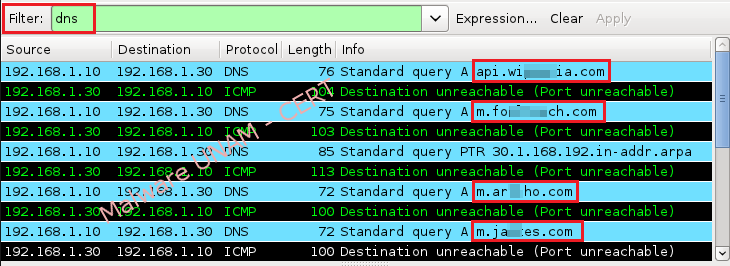
Having identified the domains that the malware was trying to solve, the file “hosts” was edited in order to redirect traffic and queries to another machine on the same network segment. Once the malware was fooled by providing fake domains, the network traffic showed connection attempts, both web services as a service on port “7384”.
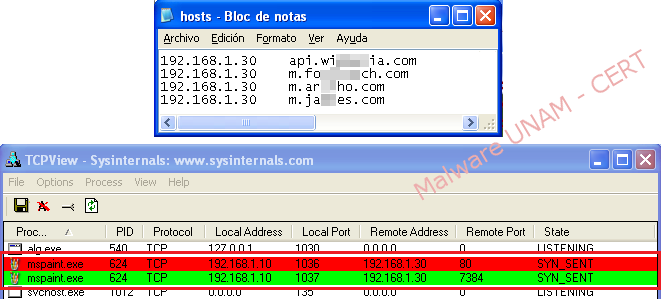
Below are shown two folders and two files stored on a USB device that will be used to test the infection by connecting it to the infected computer:
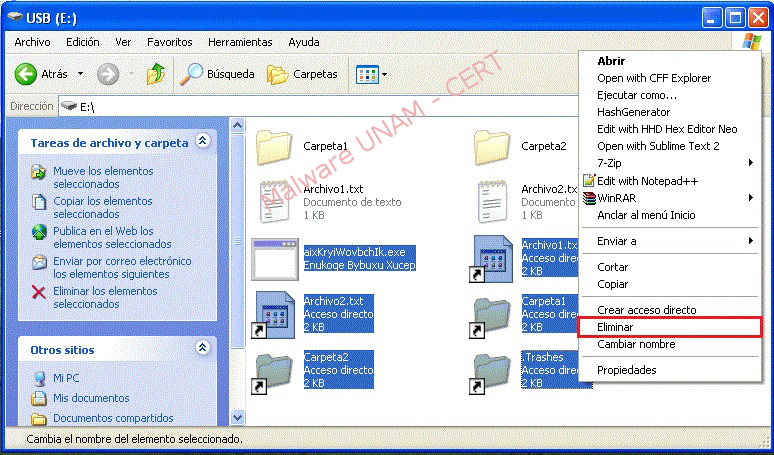
Immediately after connecting the USB device, the original files have changes in their attributes, since they are hidden now. Also, shortcuts of all the files and folders was created, which will be visible to the victim. Finally, it creates an executable file with the name “aixKryiWovbcIk.exe”, and a folder named “.Trashes”.
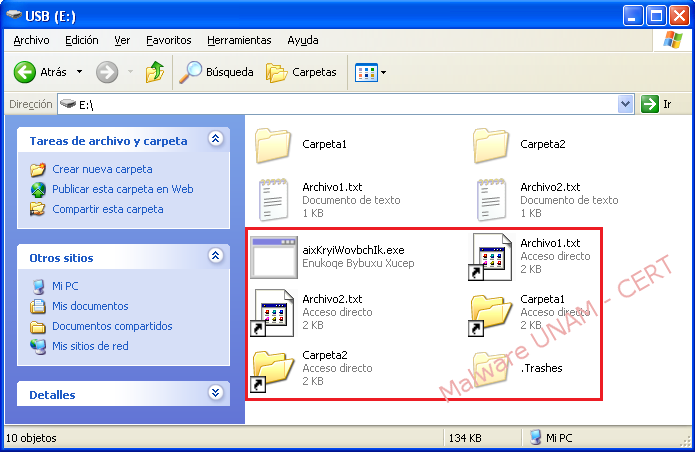
The executable file corresponds to the original malware sample, so it can be determined that all USB drives that are introduced into an infected computer, will be compromised if the computer do not have installed any antivirus solution:
Performing a string analysis to one of the shortcut created files, it was found a command that performs two actions when the victim gives double click on it: first, it opens the file pointed by the shortcut, and second, it runs the binary file that was created on the USB device.

Below are the two files created in the folder “.Trashes”: “Desktop.ini” (configuration file) and "e2a38afd" (again the original malware).

The sample was allowed to interact with the Internet, and it managed to connect to the service associated with the port “7384” and some web services. Below are the different connections established by the trojanized process “mspaint.exe”.

Once the connection is established with different websites, the download of multiple executable files begin.
Below is a list with the downloaded files:
In network traffic, it was determined that the service offered by the port "7384", which was attempting to create a connection by the malware, corresponds to an IRC service, where once authenticated the victim's computer with the password "smart", received orders to download more malicious files.

Below are all the URLs of the files that were downloaded: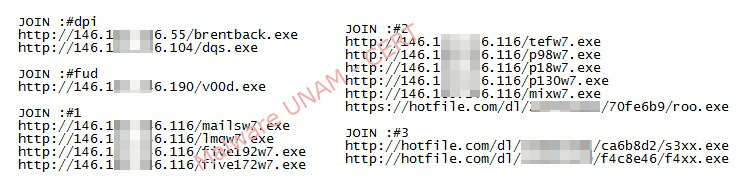
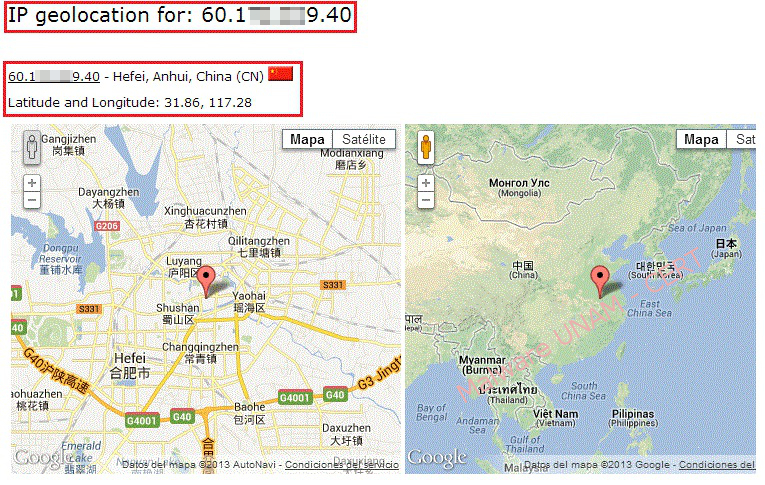
The IRC server IP address belongs to China.
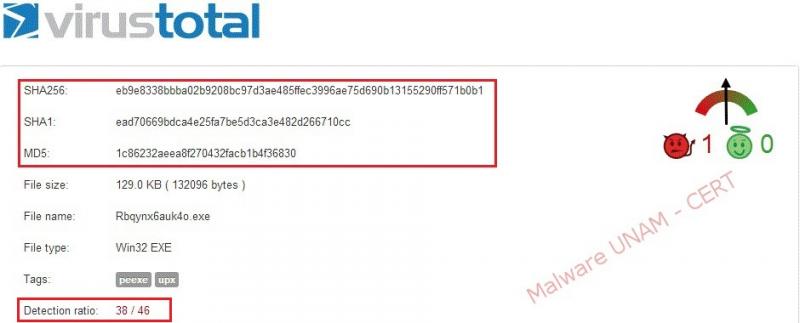
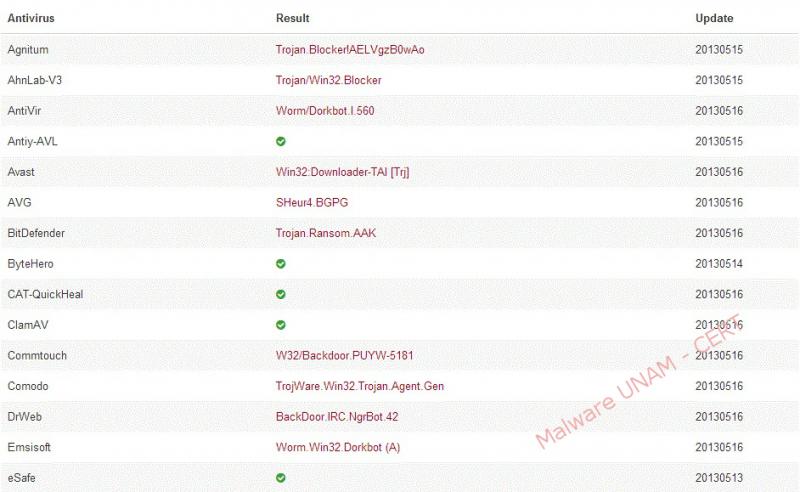
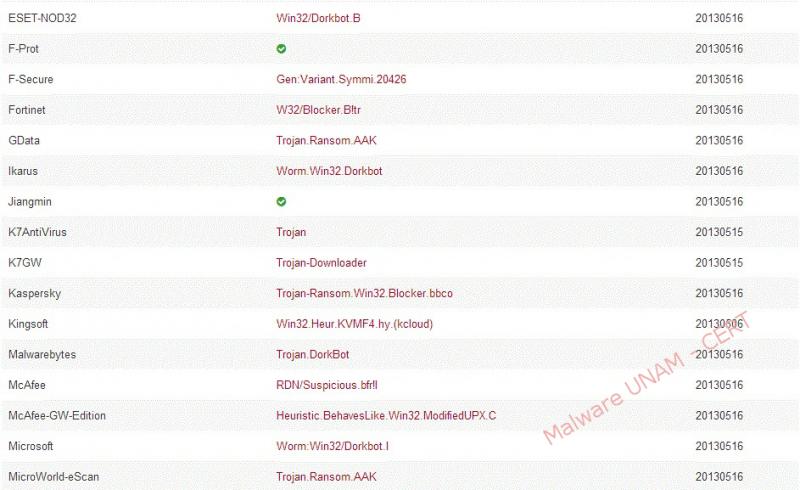
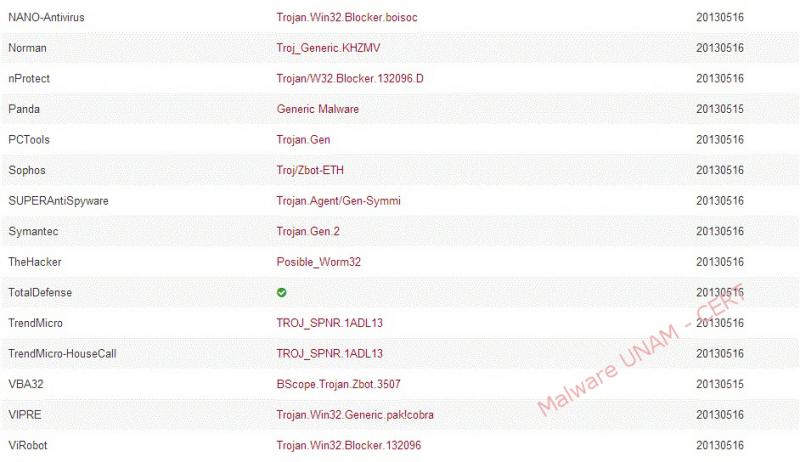
Consulting VirusTotal service, shows up that 38 of 46 antivirus solutions detect the file as malicious. Below is the report:
- Cleaning of the infected computer and recovery of the files stored in the USB device
To disinfect the computer, it can be used the “Process Explorer” program from Microsoft Sysinternals suite, in order to close the process tree that lifts the malware.
Subsequently, it should be removed malware copies, generated due to infection.
In the USB device, all shortcuts to files and folders hidden malware must be removed, also the executable file and folder “.Trashes”.
Finally, to remove the attributes "file system" and "hidden file" to all files, folders and sub folders, “attrib” command will be useful and it’s included in Windows operating systems. The symbol “*” is to indicate that the command it applies to everything that is in the USB memory.
The following command causes the modification of the attributes recursively:
