Trojan impersonates identity of gusanito.com
Computer Emergency Response Team, UNAM-CERT, received a report about an email campaign leading to the download of a supposedly malicious executable file. The file pretended to be a legitimate postcard from the widely known gusanito.com site, so that UNAM-CERT proceeded to perform the analysis of the sample. Shown below, the body of the email:
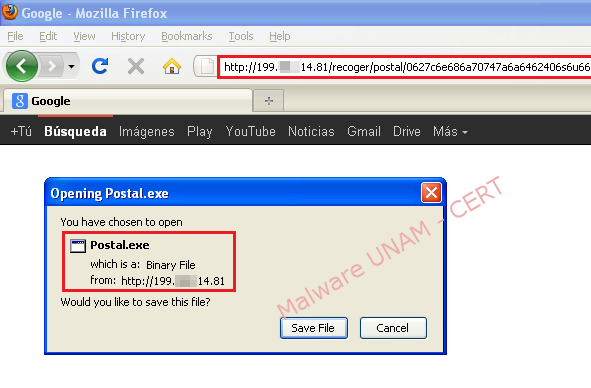
Those links redirected to the download of an executable file named “Postal.exe” from a server hosted in the United States. However, by subsequent reports to UNAM-CERT, it was found that the same sample was hosted on other servers in the United States and Lithuania.
File "Postal.exe" icon is a striking image that refers to the postal service of gusanito.com.

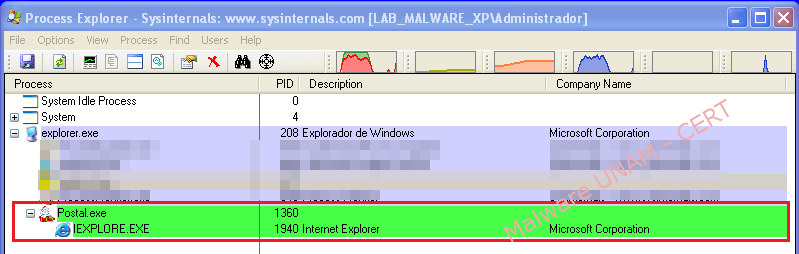
The sample was executed in a controlled environment without Internet connection. The sample started “IExplorer.exe” process, which is associated whit the “Internet Explorer” web browser.

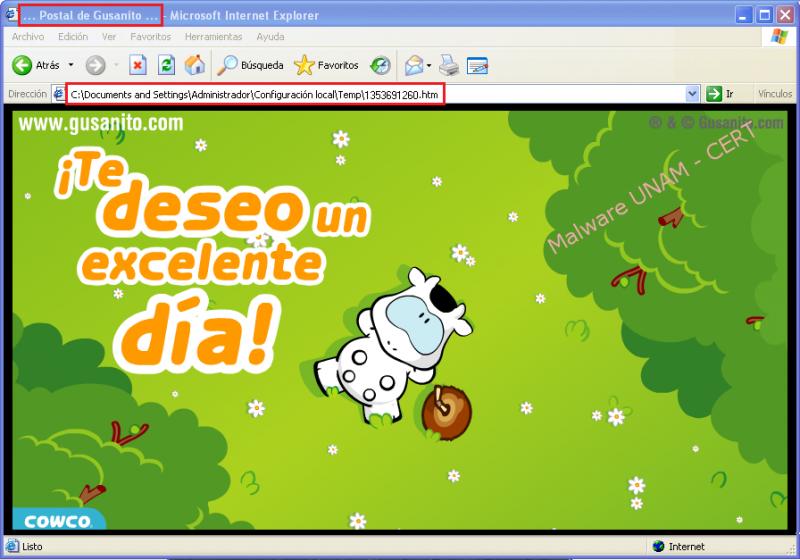
In the browser, the alleged gusanito postcard starts displaying, however, into the “Dirección” bar it can be observed a path to the file “1353691260.htm”, responsible for the animation playback.
With help of “Process Monitor” tool, included in SysInternals Suite from Microsoft, displays information from the file system, registry and process in real time, it is possible to review the creation of both files with “htm” format, just as the file with the “swf” extension, which is associated to programs in Flash that uses “ActionScript” language developed by Macromedia.

“Postal.exe” file creates the previously showed files in the “Process Monitor” report in the next path: “C:\Documents and Settings\Administrador\Configuración local\Temp”, but when the animation finishes, both files are deleted.
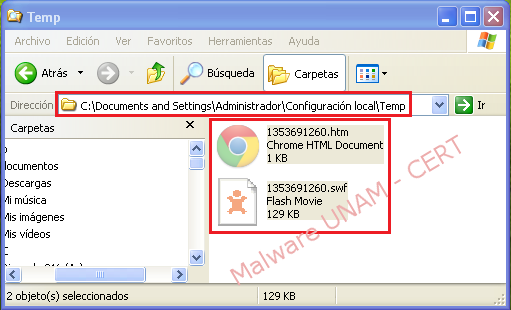
Once the files were recovered, some changes can be made to the files attributes using “attrib” command, which is included in Windows operating systems, like removing “file system” and “hidden file” attributes and thus be able to visualize them.
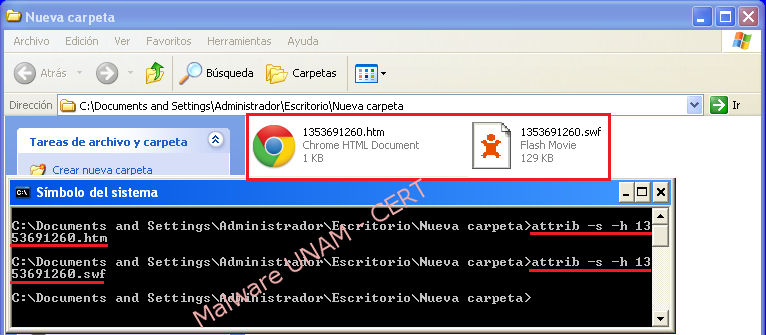
In the code “htm” file, it could be corroborated that this file is who displays the Flash file in the browser and not directly the “Postal.exe” file. The numerical names of the files “htm and swf” are randomly generated before the executable file “Postal.exe” create both files.
It is also possible to identify the <iframe> label that embeds a website hosted in Croatia.

The embedded website is shown below:
Performing static analysis to the “swf” file, it was found that it was using the version of ActionScript 1, both the file version as the label “DoAction”.
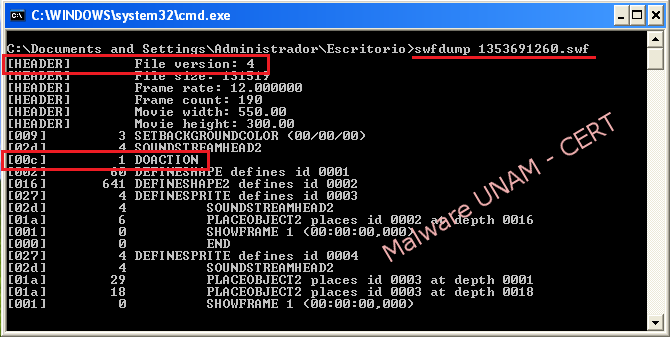
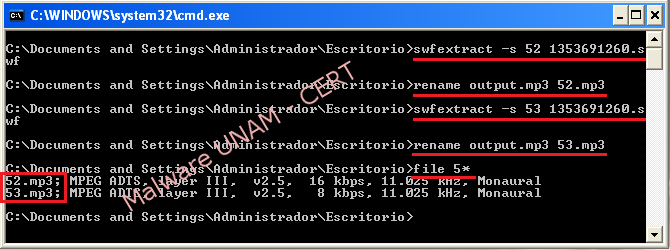
With the tool “swfextract”, included in the program installation Swftools, it was possible to list the elements of “1353691260.swf” file for later extraction.

The extracted elements are not malicious, each one of them are the audio and video elements of the postcard.
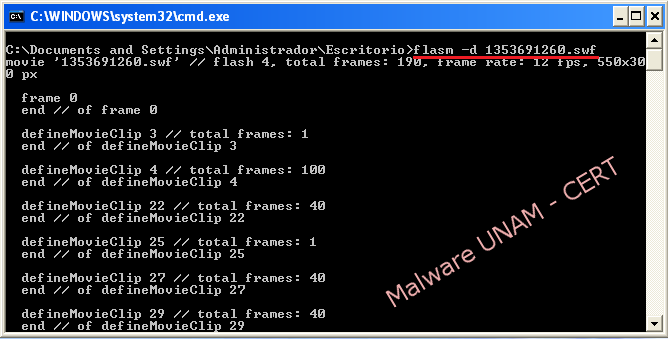
With “Flare” tool, the ActionScript instructions were extracted and it was possible to find that no one of them were malicious, those are only the order of execution to playback the postcard.
Some of the instructions are shown below:

“Flasm” tool was also used to disassemble the code of the Flash file and discard that could be compressed or visualize malicious actions. Finally, with the analysis to “swf” file, we could conclude that this file is not malicious, but it’s only a distraction to embedding a web page with tag <iframe>.
By providing Internet connection to the sample, it establishes a connection to the website mentioned on the <iframe> label.
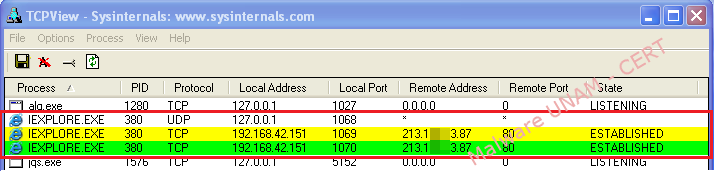
Network traffic shows that once connected, the malware begins to make requests by “GET” method to the remote site, requesting some files.
Below is the list of files that were downloaded to the infected computer because the embedding of the website by the attacker from “htm” file.
The downloaded file tree is shown below:
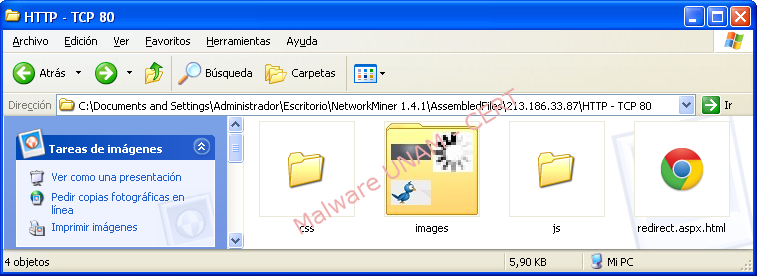
When opening the file “redirect.aspx.html” the web page is displayed as shown in the following image:
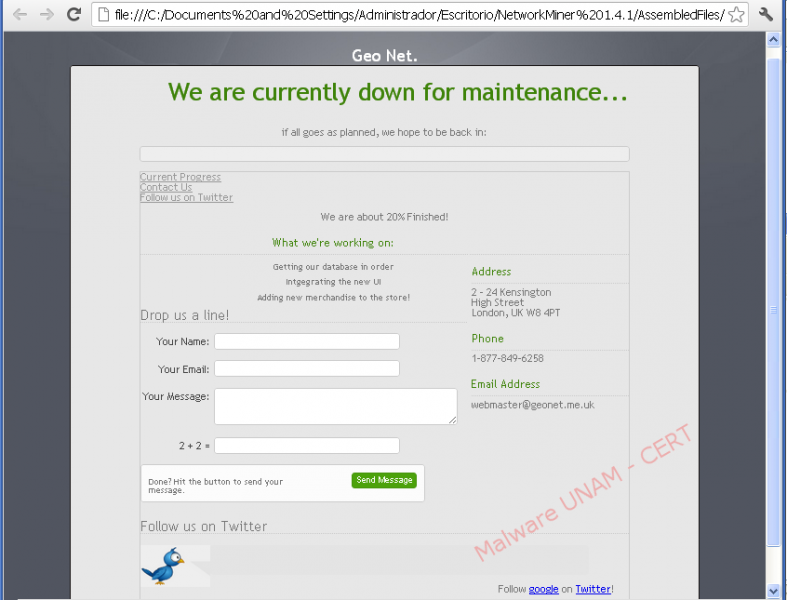
The site corresponds to the same site requested from the <iframe> label and therefore discharged, however by the time of the analysis, that site was not malicious.
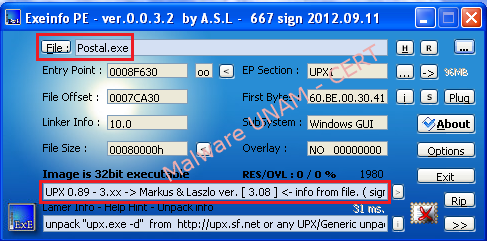
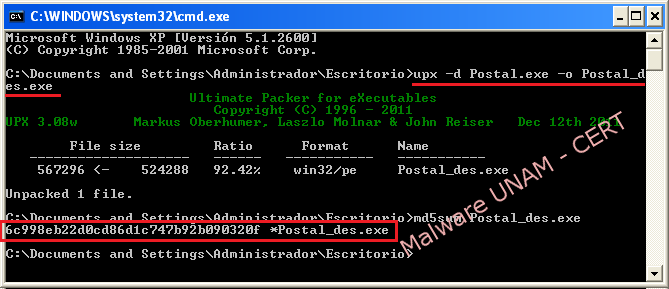
The malware sample “Postal.exe” was packaged with the tool “UPX”, as the report from “Exeinfo PE” tool shows below:
The binary file was unpacked to inspect the chains that could contain and to search in VirusTotal relevant information, however there’s no such a report on VirusTotal of the unpacked sample.
Below the VirusTotal report of the packed sample, where 34 of the 46 antivirus solutions detect the file as malicious: