Banking Trojan that presents itself as a Control Panel icon
Summary
The sample analyzed on this occasion was obtained from a report made to the Malware Analysis Team of the UNAM-CERT, where we were informed about some allegedly malicious programs found in Brazilian web sites. After the analysis, it was discovered that the sample sent information of the infected computers, such as: operating system, user privileges, security plugins of banks and IP address to a log that appears to be hosted in a legitimate URL.
Ransomware that usurps the identity of Law Enforcement Institutions in Mexico
In one of ourprevious publications on this blog, we presented the analysis of a malware sample that hijacked the user's session on the infected computer, usurping the identity of the Mexican Federal Police in order to raise money in exchange for the rescue.
Recently,several cases of infections caused by a ransomware, that attributed itself the identity of Law Enforcement Institutions to carry out extortions, were reported. The locked window is shown below:
Dynamic analysis of malicious DLLs
Inthis blog entry, the malware analysis team of UNAM-CERT will show a way to analyze a DLL file using already known tools and some specially developed by us.
ADLL or Dynamic Link Library is a file that contains blocks of code (functions or methods) that are run by request of a program. Is at this moment when it is loaded in memory.
Different programscan simultaneously use a DLL due to its modular scheme. Therefore, uninstalling a program could affect other applications that make use of shared libraries.

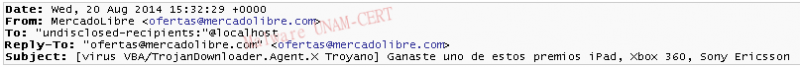
Reactivation of the digital signature… Phishing against Brazilian Bank
A few days ago, we received an email directed to customers of the bank Santander, in which users were notified that their Electronic Signature had expired and it could only be reactivated through the links contained therein. To make the message even more alarming, it is mentioned that if you do not activate it, the bank will charge you for sending a new Signature.
Pharming through Multimedia Messaging
Today we received the notification of a malicious code called 04_00_53_mensaje.exe that propagated by email using the following message:

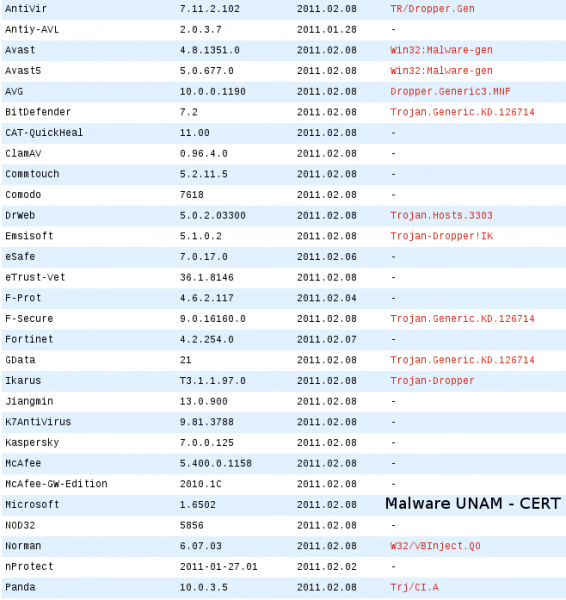
By the time of analysis it was recognized as a threat only by these antivirus engines:
Fake applications keep stealing information using social engineering
On a previous post, we informed about a fake application that pretended to come from the Santander Bank. In the same site we found an executable file called BKINTER.exe.

Spam campaign propagates malware and compromises computers
On recent days, UNAM-CERT was notified about a spam campaign that attracted users and deceived them to download files and execute them on their computers.
We visited the mentioned website and carried out some queries, however, the alleged malicious files had gif extension. At first glance, they looked like harmless images.inofensivos.
Do you get mad if I post this photo of yours on my facebook?: Messenger bots
Yesterday we received a notification that a link, from which a malicious executable could be downloaded, was propagating through Messenger. This malware is able to contact a remote server and, using specific instructions, take control of the infected computer.
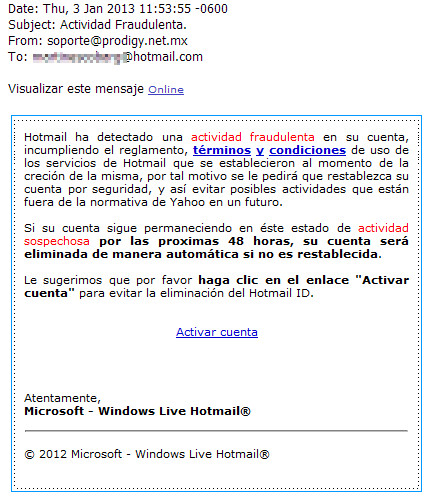
Phishing site – identity theft to Hotmail
UNAM-CERT received a notification informing about a possible identity theft campaign. The threat arrives by email as a warning about a probable fraudulent activity, either from the user or from the email address.
Malicious software used to steal credentials of information exchange services
In recent days we captured a malicious sample that, once executed on the computers, generated a large amount of network traffic; thus, we proceeded to analyze it.
The file captured was renamed 01082013.exe and has the following signatures:
MD5: b06966d77e3949e1e5edf64c82e54b1e
SHA256: 5c1a43ba2a4af38629421b12c6d1f43560c997565d5aa122b2bdb4fd99c60bba
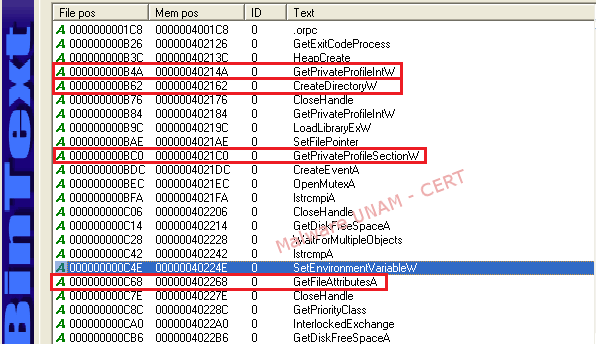
The string analysis of the file showed us a couple of functions used by the malicious file. On the next image, the functions marked in red are the ones that allowed it to obtain the configuration values from the initialization files (GetPrivateProfile), as well as the attributes from the directories and the files in the system (GetFileAttribute). The function CreateDirectory is also present, so the sample probably creates a directory on execution.